
There is hope
Virtual Money Part 2 of 5…US banking corruption !
1781–1836: The Bank of North America; the First, and Second, Bank of the United States[edit]
Bank of North America[edit]
Some Founding Fathers were strongly opposed to the formation of a central banking system; the fact that England tried to place the colonies under the monetary control of the Bank of England was seen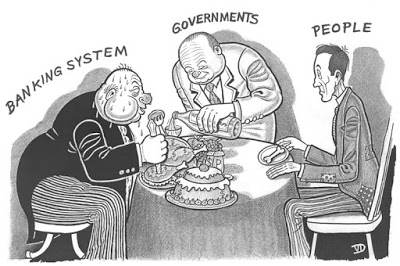 by many as the “last straw”[verification needed] of oppression which led directly to the American Revolutionary War.[citation needed]
by many as the “last straw”[verification needed] of oppression which led directly to the American Revolutionary War.[citation needed]
http://www.investopedia.com/articles/forex/09/factors-drive-american-dollar.aspOthers were strongly in favor of a central bank. Robert Morris, as Superintendent of Finance, helped to open the Bank of North America in 1782, and has been accordingly called by Thomas Goddard “the father of the system of credit and paper circulation in the United States.” As ratification in early 1781 of the Articles of Confederation had extended to Congress the sovereign power to generate bills of credit, it passed later that year an ordinance to incorporate a privately subscribed national bank following in the footsteps of the Bank of England. However, it was thwarted in fulfilling its intended role as a nationwide central bank due to objections of “alarming foreign influence and fictitious credit,” favoritism to foreigners and unfair policies against less corrupt state banks issuing their own notes, such that Pennsylvania’s legislature repealed its charter to operate within the Commonwealth in 1785.
First Bank of the United States
In 1791, former Morris aide and chief advocate for Northern mercantile interests, Alexander Hamilton, the Secretary of the Treasury, accepted a compromise with the Southern lawmakers to ensure the continuation of Morris’s Bank project; in exchange for support by the South for a national bank, Hamilton agreed to ensure sufficient support to have the national or federal capitol moved from its temporary Northern location, New York, to a “Southern” location on the Potomac. As a result, the First Bank of the United States (1791–1811) was chartered by Congress within the year and signed by George Washington soon after. The First Bank of the United States was modeled after the Bank of England and differed in many ways from today’s central banks. For example, it was partly owned by foreigners, who shared in its profits. Also, it was not solely responsible for the country’s supply of bank notes. It was responsible for only 20% of the currency supply; state banks accounted for the rest. Several founding fathers bitterly opposed the Bank. Thomas Jefferson saw it as an engine for speculation, financial manipulation, and corruption.[1] In 1811 its twenty-year charter expired and was not renewed by Congress. Absent the federally chartered bank, the next several years witnessed a proliferation of federally issued Treasury Notes to create credit as the government struggled to finance the War of 1812; a suspension of specie payment by most banks soon followed as well.
Second Bank of the United StatesMain article: Second Bank of the United Stateshttp://www.investopedia.com/articles/forex/09/factors-drive-american-dollar.asp
After five years, the federal government chartered its successor, the Second Bank of the United States (1816–1836). James Madison signed the charter with the intention of stopping runaway inflation that had plagued the country during the five-year interim. It was basically a copy of the First Bank, with branches across the country. Andrew Jackson, who became president in 1828, denounced the bank as an engine of corruption. His destruction of the bank was a major political issue in the 1830s and shaped the Second Party System, as Democrats in the states opposed banks and Whigs supported them. He was unable to get the bank dissolved, but refused to renew its charter. Jackson attempted to counteract this by executive order requiring all Federal land payments to be made in gold or silver. This produced the Panic of 1837.
1837–1862: “Free Banking” Era[edit]
| Period | % Change in Money Supply | % Change in Price Level |
|---|---|---|
| 1832–37 | + 61 | +28 |
| 1837–43 | − 58 | −35 |
| 1843–48 | +102 | + 9 |
| 1848–49 | − 11 | 0 |
| 1849–54 | +109 | +32 |
| 1854–55 | − 12 | + 2 |
| 1855–57 | + 18 | + 1 |
| 1857–58 | − 23 | −16 |
| 1858–61 | + 35 | − 4 |
In this period, only state-chartered banks existed. They could issue bank notes against specie (gold and silver coins) and the states heavily regulated their own reserve requirements, interest rates for loans and deposits, the necessary capital ratio etc. These banks had existed since 1781, in parallel with the Banks of the United States. The Michigan Act (1837) allowed the automatic chartering of banks that would fulfill its requirements without special consent of the state legislature. This legislation made creating unstable banks easier by lowering state supervision in states that adopted it. The real value of a bank bill was often lower than its face value, and the issuing bank’s financial strength generally determined the size of the discount. By 1797 there were 24 chartered banks in the U.S.; with the beginning of the Free Banking Era (1837) there were 712.
state supervision in states that adopted it. The real value of a bank bill was often lower than its face value, and the issuing bank’s financial strength generally determined the size of the discount. By 1797 there were 24 chartered banks in the U.S.; with the beginning of the Free Banking Era (1837) there were 712.
During the free banking era, the banks were short-lived compared to today’s commercial banks, with an average lifespan of five years. About half of the banks failed, and about a third of which went out of business because they could not redeem their notes.[2] (See also “Wildcat banking“.)
During the free banking era, some local banks took over the functions of a central bank. In New York, the New York Safety Fund provided deposit insurance for member banks. In Boston, the Suffolk Bank guaranteed that bank notes would trade at near par value, and acted as a private bank note clearinghouse.[citation needed]
1863–1913: National Banks[edit]
The National Banking Act of 1863, besides providing loans in the Civil War effort of the Union, included provisions:
- To create a system of national banks. They had higher standards concerning reserves and business practices than state banks. Recent research indicates that state monopoly banks had the lowest long run survival rates.[3] The office of Comptroller of the Currency was created to supervise these banks.
- To create a uniform national currency. To achieve this, all national banks were required to accept each other’s currencies at par value. This eliminated the risk of loss in case of bank default. The notes were printed by the Comptroller of the Currency to ensure uniform quality and prevent counterfeiting.
- To finance the war, national banks were required to secure their notes by holding Treasury securities, enlarging the market[vague] and raising its[vague] liquidity.
As described by Gresham’s Law, soon bad money from state banks drove out the new, good money; the government imposed a 10% tax on state bank bills, forcing most banks to convert to national banks. By 1865, there were already 1,500 national banks. In 1870, 1,638 national banks stood against only 325 state banks. The tax led in the 1880s and 1890s to the creation and adoption of checking accounts. By the 1890s, 90% of the money supply was in checking accounts. State banking had made a comeback.
Two problems still remained in the banking sector. The first was the requirement to back up the currency with treasuries. When the treasuries fluctuated in value, banks had to recall loans or borrow from other banks or clearinghouses. The second problem was that the system created seasonal liquidity spikes. A rural bank had deposit accounts at a larger bank, that it withdrew from when the need for funds was highest, e.g., in the planting season. When combined liquidity demands were too big, the bank again had to find a lender of last resort.
These liquidity crises led to bank runs, causing severe disruptions and depressions, the worst of which was the Panic of 1907.
National banks issued National Bank Notes as currency. Because they were uniformly backed by US government debt, they generally traded at comparable values in contrast to the notes issued during the Free Banking era in which notes from different banks could have significantly different values. National bank notes were not however “lawful tender”, and could not be used as bank reserves under the National Bank Act. The Federal government issued greenbacks which fulfilled this role along with gold.[4]
Congress suspended the gold standard in 1861 early in the Civil War and began issuing paper currency (greenbacks). The federally issued greenbacks were gradually supposed to be eliminated in favor of national bank notes after the Specie Payment Resumption Act of 1875 was passed. However, the elimination of the greenbacks was suspended in 1878 and the notes remained in circulation. Federal debt throughout the period continued to be paid in gold. In 1879, the United States had returned to the gold standard, and all currency could be redeemed in gold. [5]
1907–1913: Creation of the Federal Reserve System[edit]
Panic of 1907 alarms bankers[edit]
Early in 1907, New York Times Annual Financial Review published Paul Warburg‘s (a partner of Kuhn, Loeb and Co.) first official reform plan, entitled “A Plan for a Modified Central Bank,” in which he outlined remedies that he thought might avert panics. Early in 1907, Jacob Schiff, the chief executive officer of Kuhn, Loeb and Co., in a speech to the New York Chamber of Commerce, warned that “unless we have a central bank with adequate control of credit resources, this country is going to undergo the most severe and far reaching money panic in its history.” “The Panic of 1907” hit full stride in October. [Herrick]
Bankers felt the real problem was that the United States was the last major country without a central bank, which might provide stability and emergency credit in times of financial crisis. While segments of the financial community were worried about the power that had accrued to JP Morgan and other ‘financiers’, most were more concerned about the general frailty of a vast, decentralized banking system that could not regulate itself without the extraordinary intervention of one man. Financial leaders who advocated a central bank with an elastic currency after the Panic of 1907 included Frank Vanderlip, Myron T. Herrick, William Barret Ridgely, George E. Roberts, Isaac Newton Seligman and Jacob H. Schiff. They stressed the need for an elastic money supply that could expand or contract as needed. After the scare of 1907 the bankers demanded reform; the next year, Congress established a commission of experts to come up with a nonpartisan solution.
Aldrich Plan[edit]
Rhode Island Senator Nelson Aldrich, the Republican leader in the Senate, ran the Commission personally, with the aid of a team of economists. They went to Europe and were impressed with how the central banks in Britain and Germany appeared to handle the stabilization of the overall economy and the promotion of international trade. Aldrich’s investigation led to his plan in 1912 to bring central banking to the United States, with promises of financial stability, expanded international roles, control by impartial experts and no political meddling in finance. Aldrich asserted that a central bank had to be, paradoxically, decentralized somehow, or it would be attacked by local politicians and bankers as had the First and Second Banks of the United States. The Aldrich plan was introduced in 62nd and 63rd Congresses (1912 and 1913) but never gained much traction as the Democrats in 1912 won control of both the House and the Senate as well as the White House.
A regional Federal Reserve system[edit]
The new President, Woodrow Wilson, then became the principal mover for banking and currency reform in the 63rd Congress, working with the two chairs of the House and Senate Banking and Currency Committees, Rep. Carter Glass of Virginia and Sen. Robert L. Owen of Oklahoma. It was Wilson who insisted that the regional Federal Reserve banks be controlled by a central Federal Reserve board appointed by the president with the advice and consent of the U.S. Senate.
Agrarian demands partly met[edit]
William Jennings Bryan, now Secretary of State, long-time enemy of Wall Street and still a power in the Democratic party, threatened to destroy the bill. Wilson masterfully came up with a compromise plan that pleased bankers and Bryan alike. The Bryanites were happy that Federal Reserve currency became liabilities of the government rather than of private banks—a symbolic change—and by provisions for federal loans to farmers. The Bryanite demand to prohibit interlocking directorates did not pass. Wilson convinced the anti-bank Congressmen that because Federal Reserve notes were obligations of the government, the plan fit their demands. Wilson assured southerners and westerners that the system was decentralized into 12 districts, and thus would weaken New York City’s Wall Street influence and strengthen the hinterlands. After much debate and many amendments Congress passed the Federal Reserve Act or Glass–Owen Act, as it was sometimes called at the time, in late 1913. President Wilson signed the Act into law on December 23, 1913.
The Federal Reserve[edit]
The Federal Reserve System—also known as the Federal Reserve or simply as the Fed—is the central banking system of the United States today. The Federal Reserve’s power developed slowly in part due to an understanding at its creation that it was to function primarily as a reserve, a money-creator of last resort to prevent the downward spiral of withdrawal/withholding of funds which characterizes a monetary panic. At the outbreak of World War I, the Federal Reserve was better positioned than the Treasury to issue war bonds, and so became the primary retailer for war bonds under the direction of the Treasury. After the war, the Federal Reserve, led by Paul Warburg and New York Governor Bank President Benjamin Strong, convinced Congress to modify its powers, giving it the ability to both create money, as the 1913 Act intended, and destroy money, as a central bank could.
During the 1920s, the Federal Reserve experimented with a number of approaches, alternatively creating and then destroying money which, in the eyes of Milton Friedman, helped create the late-1920s stock market bubble.[6]
After Franklin D. Roosevelt took office in 1933, the Federal Reserve was subordinated to the Executive Branch, where it remained until 1951, when the Federal Reserve and the Treasury department signed an accord granting the Federal Reserve full independence over monetary matters while leaving fiscal matters to the Treasury.
The Federal Reserve’s monetary powers did not dramatically change for the rest of the 20th century, but in the 1970s it was specifically charged by Congress to effectively promote “the goals of maximum employment, stable prices, and moderate long-term interest rates” as well as given regulatory responsibility over many consumer credit protection laws.
Factors Affecting Dollar Value
The point is that when it comes to taking a position in the dollar, the currency trader needs to assess the different factors that affect the value of the dollar to try to determine a direction or trend. The methodology can be divided into three groups as follows:
- Supply and demand factors
- Sentiment and market psychology
- Technical factors
Let’s take each group individually.
Read more: 3 Factors That Drive The U.S. Dollar | Investopedia http://www.investopedia.com/articles/forex/09/factors-drive-american-dollar.asp#ixzz4d3v9EQCV
Follow us: Investopedia on Facebook
upply Versus Demand for Dollars
When we export products or services, we create a demand for dollars because our customers need to pay for our goods and services in dollars and, therefore they will have to convert their local currency into dollars. Hence they sell their currency to buy dollars so that they can make the payment.
In addition, when the U.S. government or large American corporations issue bonds to raise capital, and if these bonds are bought by foreigners then again the bonds have to be paid for in dollars and the customer will have to sell their local currency to buy dollars so they can effect payment. Also, if there is strong growth in the U.S. and companies are expanding their earnings then the desire by foreigners to own corporate stocks in the U.S. also requires that they sell their currency to buy dollars to pay for the purchase of stocks.
Sentiment and Market Psychology
But what if the U.S. economy weakens and consumption slows due to increasing unemployment? Then the U.S. is confronted with the possibility that foreigners may sell their bonds or stocks and return the cash from the sale in order to return to their local currency. Hence they sell the dollars and buy back their local currency.
Technical Factors
As traders, we have to gauge whether the supply of dollars will be greater or less than the demand for dollars. To help us determine this, we need to pay attention to various news and event items, such as the release by the government of various statistics, such as payroll data, GDP data, and other market and economy measuring information that can help us to determine what is happening in the economy and to estimate whether the economy is strengthening or weakening. (For a comprehensive overview of 24 major indicators, take a look at our Economic Indicators Tutorial.)
In addition, we need to determine the general sentiment regarding what the players in the market think the outcome of events is likely to be. Very often, sentiment will drive the market rather than the fundamentals of supply and demand . To add to this mix of prognostication, besides the measurement of supply and demand factors and sentiment, we also have the historical patterns generated by seasonal factors, support and resistance levels, technical indicators and so on. Many traders believe that these patterns are repetitive and therefore can be used to predict future movements. (Learn about the basics of technical analysis in our Technical Analysis Tutorial.)
Bringing Them All Together
Since trading relies on the ability of a trader to take a risk and manage it accordingly, traders usually adopt some combination of the three above methods to make their buy or sell decisions. The art of trading exists in stacking the odds in your favor and building an edge. If the probability of being correct is high enough the trader will enter the market and manage his hypothesis accordingly. To stack the odds in our favor we therefore need to take into account each one of the three methodologies and hopefully find them to be congruent, meaning that they all point in the same direction.
An Example
The economic conditions during the recession that began in 2007 forced the U.S. government to play an unprecedented role in the economy. Since economic growth was receding as a result of the large deleveraging of financial assets taking place, the government had to take up the slack by increasing government spending to keep the economy going. The purpose of their spending was to create jobs so that the consumer could earn money and increase consumption thereby fueling the growth needed to support economic growth. (For a review of the recession during this time period, refer to The 2007-08 Financial Crisis In Review.)
The government took this position at the expense of an increasing deficit and national debt. It financed this increase by essentially printing money and by selling government bonds to foreign governments and investors – resulting in an increase in the supply of dollars. Hence the dollar depreciated as a result. Another concern for countries that rapidly issue debt is that the interest burden will increase and, therefore, more tax dollars will be allocated just to cover the interest rate.
One of the roles of the government is to create the conditions necessary to allow the markets to grow so that is the economy is as close to full employment as possible, but with controlled inflation. Thus when the economy deflates the government will try to do all it can to re-inflate it in a controlled manner.
The Bottom Line
It may be helpful for a trader to keep an eye on the Dollar Index chart to provide an overview of how the dollar fares against the other currencies in the index. By watching the patterns on the chart and listening to the sentiment in the market, as well as monitoring the major fundamental factors that affect supply and demand, a trader can develop a big picture sense of the flow of dollars and thus develop an insight to choose profitable positions in future trades.
 TRADING
TRADING3 Factors That Drive The U.S. Dollar
Currency traders assess supply and demand, sentiment and market psychology, and technical factors to develop a big picture sense of the U.S. dollar’s flow. TRADING
TRADINGThe U.S. Dollar: What Every Forex Trader Needs To Know
The U.S. dollar is by far the most significant currency in the global market. Find out what you need to know if you want to trade it. INSIGHTS
INSIGHTS4 Factors That Shape Market Trends
Trends allow traders and investors to capture profits. Find out what’s behind them. TRADING
TRADINGTop Economic Factors That Depreciate The $US
A variety of factors contribute to currency depreciation, including monetary policy, inflation, demand for currency, economic growth and export prices. TRADING
TRADINGHow Equities Affect The FX Market
We look at how you can predict a currency movement by studying the stock market. TRADING
TRADINGPlay Foreign Currencies Against The U.S. Dollar And Win
Don’t panic when the dollar drops. Learn to exploit the greenback’s decline and profit from it. TRADING
TRADINGMain Factors that Influence Exchange Rates
The exchange rate is one of the most important determinants of a country’s relative level of economic health and can impact your returns. TRADING
TRADINGWeekend Analysis: A Path To Forex Profits
A weekend analysis can strengthen your forex trading through preparation and planning. TRADING
TRADINGDrastic Currency Changes: What’s The Cause?
Currency fluctuations often defy logic. Learn the trends and factors that result in these movements. INSIGHTS
INSIGHTSExploring The Current Account In The Balance Of Payments
Learn how a country’s current account balance reflects the country’s economic health.
-
What happens to the US dollar during a trade deficit?
Learn what happens to the U.S. dollar during trade deficits. Trade deficits happen when imports exceed exports leading foreigners … Read Answer >> -
What is the difference between a nation’s current account deficit and its currency …
Learn the respective meanings of the two terms, current account deficit and currency valuation, and understand the relationship … Read Answer >> -
What are key economic factors that can cause currency depreciation in a country?
Read about the causes of currency devaluation, and find out how to differentiate between relative and absolute currency devaluation. Read Answer >> -
How are international exchange rates set?
International currency exchange rates display how much one unit of a currency can be exchanged for another currency. Currency … Read Answer >>
Read more: 3 Factors That Drive The U.S. Dollar | Investopedia http://www.investopedia.com/articles/forex/09/factors-drive-american-dollar.asp#ixzz4d3vENyp4
Follow us: Investopedia on Facebook
Virtual Money Part 1 of 5 part series !
-
Part 1: What is virtual Money/currencies?







Part 2: What’s wrong with regular banking?
-
Part 3: Where can i use Virtual Monies ?
-
Part 4: Which sites should i AVOID?
-
PART 5: Help ME with buying virtual monies !
First, let’s start with my own adventures in virtual money ! In 2010 i bought 1 bit coin for $100 USD [approx]. Today that bit coin is worth $1069.48 . So let’s for shits and giggles assume i actually bought 100 Bit coins @ that $ 100 USD…how much is that today? yep ! roughly $100,ooo USD. Keep reading i’m going to lay this all out for you in a 5 part mini-series blog ! Michael J Ludowise
Keep reading i’m going to lay this all out for you in a 5 part mini-series blog ! Michael J Ludowise
A virtual currency [ scroll down for youtube videos of virtual money and it’s partners !]

or  virtual money has been defined in 2012 by the European Central Bank as “a type of unregulated, digital money, which is issued and usually controlled by its developers, and used and accepted among the members of a specific virtual community.”
virtual money has been defined in 2012 by the European Central Bank as “a type of unregulated, digital money, which is issued and usually controlled by its developers, and used and accepted among the members of a specific virtual community.”

The Financial Crimes Enforcement Network (FinCEN), a bureau of the US Treasury, defined virtual currency in its guidance published in 2013. In 2014, the European Banking Authority defined virtual currency as “a digital representation of value that is neither issued by a central bank or a public authority, nor necessarily attached to a fiat currency,
Authority defined virtual currency as “a digital representation of value that is neither issued by a central bank or a public authority, nor necessarily attached to a fiat currency,
but is accepted by natural or legal persons as a means of payment and can be transferred, stored or traded electronically”.
Sometimes called ” clean “or “virtually laundered “money . This does not imply that it’s illegal, it, should more imply that this is money not touched by dirty bankers.

It is inflation proof ! Virtual money makes people nervous the second you say clean or virtually laundered people freak out why because all we have been trained is that banking must be done by the big banks the people that own everything about your existence filthy dirty rotten eggs yes takes a concern themselveswith nothing but their own egotist driven goals if we want to get down deeper we can take it into the one world order of banking as a matter fact that was just a Segway to let you know that I am part two we will be discussing modern banks the corruption of from the local credit union to the Roth Childs themselves those might be whores of money.
Virtual currency bitcoin bringing real rewards to Australian businesses, but reservations remain
The real-world use of virtual currency is catching on with Australian businesses, despite criticism the system is too unreliable.
The bitcoin online currency was launched in 2009 with the promise of cutting out bank fees, but since then it has been linked with drug websites and has attracted the ire of the Chinese government.
Despite that, a number of Australian businesses are now saying it gives them an edge in an increasingly competitive marketplace.
One company on board is Tomcar, an all-terrain vehicle manufacturer based in the Melbourne suburb of Oakleigh South that sells online to farmers, the military and emergency services.
“Using bitcoins to pay our suppliers overseas allows us to save a huge amount of exchange rate costs and banking fees,” Mr Brim told the ABC’s 7.30 program.
“We purchase parts from Israel in bitcoin and we only pay a 1 per cent fee.
“We’ve saved easily [$50,000] in fees, and that money can go into R and D (research and development), and customer service, so it’s important.
“We’ve sold parts to customers in New Zealand who’ve paid us in bitcoin.
“We’ve sold merchandise to Canada and America, (but) we haven’t sold a car yet in bitcoin.”
Volatile prices represent a risk to businesses
However, as the currency’s use on the open market has increased, so have its price fluctuations.
In one of the first known transactions, one bitcoin was worth 6 US cents, but last year it was briefly worth more than gold and soared through the $US1,000 mark.
David Glance, director of the University of Western Australia Centre for Software Practice, warns that there are a number of risks involved in using bitcoins.
“The price is very volatile, so it represents a risk like any investment,” he said.
“People who have kept them in digital wallets online in certain sites have been hacked, so bitcoins have been lost that way.
“Certain exchanges have gone out of business and people have lost bitcoins that way.”
That volatility means businesses know it is not safe to hold onto bitcoins and, instead, there are merchants servicing the currency who convert payment to real dollars.
Or you can use one of Australia’s two bitcoin machines, owned by bitcoin enthusiast Dale Dickins.
“I see it becoming a lot more user friendly and accessible to people who don’t have access to banks and international remittance for people who transfer funds overseas,” Ms Dickins said.
Melbourne cafes, fashion stores accepting bitcoins as payment
However, there are only a handful of real world places where you can spend bitcoins.
The price is very volatile, so it represents a risk like any investment.
University of WA’s David Glance
Cafe Imbiss25 in Melbourne is one of them and co-owner Scott Rigg believes that “as it goes along, it will become more stable”.
“I’m fascinated by what the Government and the banks [are] going to do about it, if it really starts to impact on their bottom line,” he said.
“Is this another way to start to chip away at that power structure?
“I don’t know, but I don’t mind being involved in that.”
Around the corner, clothing and jewellery store Eclectico is also taking bitcoins.
Buyers hope to cash in on other virtual currencies
Hot on bitcoin’s tail, more alternative virtual currencies are cropping up, with litecoin and dogecoin the best known so far.
James Croft, the editor of technology website Reckoner, says people have seen the value of bitcoins skyrocket and are trying to cash in.
“We’re seeing an explosion of them and the vast majority of them are junk, they’re not worth anything at the moment,” he said.
“But the reason they’re being created is that very slight chance that there might be something in the future.
“The reason all these alternative currencies have been created is because whoever gets in on the ground floor can make quite a lot of money if that takes off.”
FOLLOWING, ARE VIDEOS FOR LEARNING THE BASICS OF VIRTUAL MONEY !
THE CONTRIBUTORS OF EACH VIDEO, WORK HARD TO PUT TOGETHER THEIR PRESENTATIONS FOR YOUR LEARNING !
PLEASE LIKE AND SUBSCRIBE WHERE APPLICABLE TO THE PRESENTERS SITES !
(7.30)
The real-world use of virtual currency is catching on with Australian businesses, despite criticism the system is too unreliable.
The bitcoin online currency was launched in 2009 with the promise of cutting out bank fees, but since then it has been linked with drug websites and has attracted the ire of the Chinese government.
Despite that, a number of Australian businesses are now saying it gives them an edge in an increasingly competitive marketplace.
One company on board is Tomcar, an all-terrain vehicle manufacturer based in the Melbourne suburb of Oakleigh South that sells online to farmers, the military and emergency services.
“Using bitcoins to pay our suppliers overseas allows us to save a huge amount of exchange rate costs and banking fees,” Mr Brim told the ABC’s 7.30 program.
“We purchase parts from Israel in bitcoin and we only pay a 1 per cent fee.
“We’ve saved easily [$50,000] in fees, and that money can go into R and D (research and development), and customer service, so it’s important.
“We’ve sold parts to customers in New Zealand who’ve paid us in bitcoin.
“We’ve sold merchandise to Canada and America, (but) we haven’t sold a car yet in bitcoin.”
Volatile prices represent a risk to businesses
However, as the currency’s use on the open market has increased, so have its price fluctuations.
In one of the first known transactions, one bitcoin was worth 6 US cents, but last year it was briefly worth more than gold and soared through the $US1,000 mark.
David Glance, director of the University of Western Australia Centre for Software Practice, warns that there are a number of risks involved in using bitcoins.
“The price is very volatile, so it represents a risk like any investment,” he said.
“People who have kept them in digital wallets online in certain sites have been hacked, so bitcoins have been lost that way.
“Certain exchanges have gone out of business and people have lost bitcoins that way.”
That volatility means businesses know it is not safe to hold onto bitcoins and, instead, there are merchants servicing the currency who convert payment to real dollars.
Or you can use one of Australia’s two bitcoin machines, owned by bitcoin enthusiast Dale Dickins.
“I see it becoming a lot more user friendly and accessible to people who don’t have access to banks and international remittance for people who transfer funds overseas,” Ms Dickins said.
Melbourne cafes, fashion stores accepting bitcoins as payment
However, there are only a handful of real world places where you can spend bitcoins.
The price is very volatile, so it represents a risk like any investment.
University of WA’s David Glance
Cafe Imbiss25 in Melbourne is one of them and co-owner Scott Rigg believes that “as it goes along, it will become more stable”.
“I’m fascinated by what the Government and the banks [are] going to do about it, if it really starts to impact on their bottom line,” he said.
“Is this another way to start to chip away at that power structure?
“I don’t know, but I don’t mind being involved in that.”
Around the corner, clothing and jewellery store Eclectico is also taking bitcoins.
Buyers hope to cash in on other virtual currencies
Hot on bitcoin’s tail, more alternative virtual currencies are cropping up, with litecoin and dogecoin the best known so far.
James Croft, the editor of technology website Reckoner, says people have seen the value of bitcoins skyrocket and are trying to cash in.
“We’re seeing an explosion of them and the vast majority of them are junk, they’re not worth anything at the moment,” he said.
“But the reason they’re being created is that very slight chance that there might be something in the future.
“The reason all these alternative currencies have been created is because whoever gets in on the ground floor can make quite a lot of money if that takes off.”
FOLLOWING OUR BLOG/PAGES FOR UP TO THE MINUTE POST NOTIFICATIONS AND MORE !
FOLLOWING IS A SHORT INTRO TO PICKING A WALLET! iF YOU WATHCHE DTHE VIDEOS ABOVE YOU HEARD ALOT OF TALK ABOUT VIRTUAL WALLETS ! As always educate yourself on choosing the wallet for your needs ! Note some are more secure, some are easier to use, some are just plain junk ! somwe are a scam, although the ones listed below are safe and well established wallet sites !—MJL
Choose your Bitcoin wallet
Find your wallet and start making payments with merchants and users.
 Take time to educate yourself
Take time to educate yourself
Bitcoin is different from what you know and use every day. Before you start using Bitcoin for any serious transaction, be sure to read what you need to know and take appropriate steps to secure your wallet. Always remember that it is your responsibility to choose your wallet carefully and adopt good practices in order to protect your money.
COMING SOON pART 2—MJL
Onion site marketplaces ! [Hidden web]
Full guide: How to access I2p sites & Use TheMarketplace.i2p
Note: TMP Does not exist anymore, but this tutorial was left as an I2P usage guide.
This Amazing Guide was posted on reddit by the username: moonsh00t All The Credit goes to him! – As It was listed on the Guide that the License is BSD we believe it would be a great service to give this guide more publicity outside Themarketplace.i2p subreddit and that the hard to follow formatting should be fixed, so its our pleasure to reformat it (a bit) and post it here – The OP and updates can be found On This link
Contents
- Legal Disclaimer
- Versioning
- Terminology & Abbreviations
- Prerequisites
- Concepts
- Installation & Configuration
- Refunds
- Selling on The Marketplace
- Finalising transactions outside of The Marketplace
- Transaction String Formatting
Legal Disclaimer
This guide is intended to outline the functional aspects of The Marketplace site. It should only be used to assist in the acquisition or resale of goods and services which you are lawfully permitted to purchase or engage in. Basically; don’t do anything naughty and if you do and Santa finds out, it’s on you. License: BSD – do whatever you want with it.
Versioning
| Version | Comments |
|---|---|
| 0.1 | Basic guide. Needs expansion on what to do when things go wrong and finalization etc |
| 0.2 | Improved guide with end-to-end Seller tutorial. Needs expansion on what to do when things go wrong; disputes and refunds |
| 0.3 | Full tutorial on how to claim a Refund. Improved the buyers guide slightly. |
| 0.4 | End-to-end detail on how to claim a payment without TMP’s involvement. Other miscellaneous corrections. |
| 0.5 | Tutorial on installing and configuring TAILS with persistent storage, Electrum and TMP’s Electrum plugin. Other miscellaneous corrections. |
| 0.6 | New, more sane Tails setup |
Terminology & Abbreviations
| Term | Meaning |
|---|---|
| TMP | The Marketplace |
| BTC | Bitcoin |
Prerequisites
The following guide describes how to connect to and place your first order. Note: The Marketplace is on I2P which is slow compared to TOR, if you get timeouts, just refresh until it connects. The situation should improve as usage grows. This guide assumes you are configuring from scratch for a Windows system. The following software will be installed and used. You should download these pre-requisites to a folder on your hard-disk (E.g. C:\temp\tmpsetup\) before continuing.
- Java Virtual Machine: Java software – prerequisite for I2P software to install
- Mozilla Firefox Browser: Browser for accessing I2P network
https://www.virwox.com?r=1a5251
- Bitcoin QT client 0.8.6+: Default Bitcoin client – supports multi-signature transactions. You can also use Electrum (simple to swap in), but this guide only covers Bitcoin-QT
- GPG4Win 2.2.1: Provides communication encryption
- I2P 0.9.9 (or above) Windows Graphical Installer: Provides access to the I2P network
- Bit Address: Used for generating the public/private keys you need for signing each order. You need to generate a new address for each order (see below for usage details)
- TOR Browser Bundle: Provides a more secure browser to use when using TMP.
- Bitmessage: Provides a secure method for buyers and sellers to communicate outside of TMP – suggesd method for buyer-seller communication in section Finalising transactions outside of The Marketplace tutorial
- About: Bitmessage – Semi-technical video highlighting Bitmessage functionality. Not required, just for those interested.
- Tutorial: Installing and Configuring Bitmessage – Note: If you opt to connect over TOR, you may need to initially connect with Proxy of None otherwise the icon sits on red (unconnected) for hours. Once a successful connection has been established and the icon goes yellow, change the Network Settings to use the appropriate TOR proxy indicated in the tutorial link (127.0.0.1 Port 9150 or 127.0.0.1 Port 9050) and restart Bitmessage. The icon should be yellow or green and you’ll be connected over TOR.
- TAILS (Secure Linux): Provides a secure operating system to connect to TMP. Required as part of the Installation & Configuration – For TAILS (Linux) with Electrum” tutorial.
- Electrum – Lightweight Bitcoin Client: Provides a simple, flexible Bitcoin Wallet that supports The Marketplace specific plugins to make seller order management easier. Required as part of the Installation & Configuration – For TAILS (Linux) with Electrum tutorial
Concepts
The Marketplace is conceptually pretty different from the other markets out there. Other darknet markets are basically giant online wallets into which buyers transfer Bitcoins before they go shopping. Once the buyer has received their goods, they permit the darknet market to release the funds to the seller who must then withdraw them. Once of the biggest disadvantages of this approach is that both the seller and buyer need to trust the darknet market to not:
- collapse; or
- walk away with all the money stored on the platform
for the duration of the transaction. When either of these eventualities occur, it can be very expensive and frustrating for both buyers and sellers. TMP goes some way to addressing these concerns using what’s called multi-signature transactions. Multi-signature transactions allow all the parties involved in handling the money (so that’s the buyer who is paying, the seller who is to be paid for the goods and the darknet market that wants their fee for providing a website to do all the business on), to always retain some control over the money for the duration of the order.
An Order Overview
To accomplish this, the buyer, the seller and the darknet market agree on a single use Bitcoin Address (the Bitcoin Deposit Address) into which the buyer will deposit the Bitcoins necessary to pay for their order. This agreement is reached by the repurposing of Bitcoin Addresses (the ones you are normally familiar with using to deposit your Bitcoins too), to act as keys to the agreed Bitcoin Deposit Address. Each participant (that’s the buyer, the seller and the darknet market) generate a Bitcoin Address which they use as a key to the Bitcoin Deposit Address. For anyone to move any of the Bitcoins out of the Bitcoin Deposit Address, it requires that at least two of the key holders authorise it. Once a buyer has received their order, they will mark it as Finalized on the TMP website. TMP then effectively inserts their key (creates a transaction signed with their key) into the Bitcoin Deposit Address used for the order and asks the seller to do the same. Once the seller inserts their key (signs the transaction), the Bitcoins held in the Bitcoin Deposit Address can be moved to the sellers nominated Bitcoin Address (E.g. a blockchain.info wallet, a BTC exchange etc) by broadcasting the signed transaction to the Bitcoin network. And that’s the magic. Unlike traditional darknet markets (Pandora, BlueSky etc), if TMP staff turned bad and wanted to steal the Bitcoins in a Bitcoin Deposit Address, they would also need either the buyer or the seller for every in-progress order to also sign off. If none of the parties agree, the Bitcoins will just sit in the Bitcoin Deposit Address for eternity but it also means that a buyer and a seller can get together completely outside of TMP and release any Bitcoins stored in Bitcoin Deposit Addresses to which they both hold the keys.
TMP Service Fees
Those who have been paying attention may be wondering where TMP receives its fee in all this? Well, when TMP creates the transaction that both it and the seller will sign to release the Bitcoins held in the Bitcoin Deposit Address, the transaction contains two output Bitcoin Addresses. One is the sellers nominated Bitcoin Address and a second is a Bitcoin Address owned by TMP which is where their fee goes. The transaction that TMP creates and asks the seller to sign can be decoded and inspected to check the proportion of Bitcoins they’ve allocated to themselves from the Bitcoins held in the Bitcoin Deposit Address before sign-off. Once the seller is happy, signs off and broadcasts the transaction to the Bitcoin network, everything is final and each party gets their share of the Bitcoins stored in the Bitcoin Deposit Address.
Declined Orders & Order Cancellations
When a buyer cancels an order that’s in progress or an order is declined by a seller (E.g. no stock etc), the process is the same as that of a seller signing off except that in this instance it is the buyer who signs-off to release the Bitcoins stored in the Bitcoin Deposit Address. TMP will ask the buyer to provide a Bitcoin Address they want their refund sent too, and then automatically create and sign the transaction (insert their key). The transaction is then passed to the buyer, who then signs off (inserts their key) and broadcasts the transaction to the Bitcoin network.
Order Disputes
Finally, in the unfortunate scenario where a buyer and a seller enter into a dispute (all toys out of the pram), TMP will propose a solution (For example; 50% of the Bitcoins held in the Bitcoin Deposit Address to the buyer, and 50% to the seller). Provided at least the buyer *or* the seller agree to this, TMP will then sign the transaction and submit it to either the buyer or the seller for sign-off and broadcasting to the Bitcoin network. The Bitcoins will then be distributed as agreed.
What if The Marketplace disappears?
The beauty of TMP is that they are not required to release Bitcoins stored in Bitcoin Deposit Addresses provided the buyer and the seller can get in contact with each other and agree on a transaction. It may therefore be a good idea for buyers and sellers participating in regular or large transactions to provide alternative contact details for each other so that in the event of a service outage, any outstanding orders can be finalized and the Bitcoins released. Note: In this instance either the buyer or the seller would need to create and sign a transaction which the opposite party (buyer or seller) would also need to sign-off on. Either party could then broadcast the signed transaction to the Bitcoin network. Creating a raw transaction to finalize without TMP is covered in this section of the guide: Finalising transactions outside of The Marketplace. You may also (if you are technically minded) want to read up on raw transactions and that information can be found here: Raw Transactions.
Installation and Configuration
For Windows
- Double click the I2P software installer (i2pinstall_0.9.9_windows.exe)
- Press [Next] until you reach the pack installation choice window
-

- The default option Base will be checked, but you also have the option of installing I2P as a Windows Service. This means it will automatically run in the background whenever you start your computer and you will always be participating in the I2P network. If you intend to be a frequent user, you may wish to consider this option for two reasons:
- A) Everyone who uses I2P provides routing services and bandwidth for everyone else – e.g. in the same was as you upload a torrent when you’re not downloading to help others, if you are always connected to I2P you help make the network faster for everyone else.
- B) Plausible deniability. If you are always connected to I2P, regardless of whether you are using it, your traffic cannot be so easily categorised as unique by malicious entities. For example, in the recent Harvard Bombscare the perpetrator was caught because Law Enforcement worked out how many unique users were on the TOR network at the time, and paid each one of them a visit. The perpetrator had only logged on to TOR briefly during the period identified by LE, and therefore stuck a huge red flag on himself. If you are always connected to I2P, it would be significantly more difficult to accuse you of using it for less than legal purposes…assuming you did, which of course you wouldn’t.
- Press [Next] through all the remaining steps and [Done] once the software has installed

- If you have opted to install I2P as a Windows Service you will stop the service for the purposes of this tutorial. This ensures you can check for errors. If you have not opted to install as a Windows Service, skip to the next step.
- A) Start->Run->type: services.msc and press [Enter]
- B) Scroll down until you find I2P Service
- C) Right click and select Stop
- D) Close the Services window
- Click Start and navigate to I2P shortcuts menu and click Start I2P (restartable). The I2P software will now start.
- You will be presented with the I2P command box:
- followed shortly by your default browser opening with the I2P web interface:
7-At this point it takes I2P several minutes to initialise and find the necessary connections to other participants in the network. Click the I2P logo in the top left hand corner (market in red in the screenshot below) to change the management bar to reflect the details of your I2P connection. You may need to click twice before the full management view is visible.
Once the management bar is visible look down and once you see Network: OK (in the green box in the above screenshot), you are connected to the I2P network. The lower box that says “Rejecting tunnels: starting up” will eventually change to “Accepting tunnels”. You can optionally wait for this stage if you want to ensure you are a full participant in the I2P network. It can take about 30 minutes. 8. Now that I2P has loaded, you need to configure your browser in order to access the marketplace. As indicated in the pre-requisites, we’ll be using Mozilla Firefox. The next stage is therefore to install Mozilla Firefox and the QuickJS and FoxyProxy extensions. 9. Once you have installed Mozilla Firefox and the extensions, you should see two new icons in the browser:  10. Click the FoxyProxy icon to bring up the configuration window:
10. Click the FoxyProxy icon to bring up the configuration window: 
Ensure the window looks like the screenshot above and select Add New Proxy from the menu on the left side. When the Proxy Settings window is displayed, choose the Proxy Details tab and enter 127.0.0.1 in the Host or IP Address box and 4444 in the Port box: 
Click the URL Patterns tab and click Add New Pattern. Choose a Pattern Name of I2P and in the URL pattern box enter *.i2p*. Click [OK]. 
Click [OK] to return to the configuration window. It should now look like this: 
Click [Close].
- You are now configured to connect your Mozilla Firefox browser to I2P. The penultimate stage is to check that JavaScript is disabled. The QuickJS icon should be clicked until it represents a broken wheel (hovering over will show that this is JavaScript disabled mode):
- In the address bar of Mozilla Firefox enter http://themarketplace.i2p – The I2P network will then wander off to try and route your connection. It is likely that you will receive a window saying Warning Eepsite Not Found in Addressbook. When this appears, click the stats.i2p jump service link.
 When this returns, you should receive a Success window like the one below.
When this returns, you should receive a Success window like the one below.  You will be automatically directed to save the address to your router configuration (see screenshot below), when this window displays choose Save themarketplace.i2p to router address book and continue to eepsite. It may take several attempts to get this process to happen. You only need to do this once though, when you navigate to http://themarketplace.i2p in future, it should route you directly.
You will be automatically directed to save the address to your router configuration (see screenshot below), when this window displays choose Save themarketplace.i2p to router address book and continue to eepsite. It may take several attempts to get this process to happen. You only need to do this once though, when you navigate to http://themarketplace.i2p in future, it should route you directly.  Finally, you will reach your goal – The Market Place…
Finally, you will reach your goal – The Market Place…
- Select the [Register] button to begin the registration process. As part of this process you will need to supply a PGP encryption key. This ensures that all correspondence between you and any other vendors of the site is encrypted. If you have already got a PGP public key, you can paste it in here and skip past the following steps, if not – you need to install the GPG4Win 2.2.1 package listed in the prerequisites and follow the instructions below to create your key.
- Install the GPG4Win 2.2.1 package – as part of this process ensure you check the box to install GPA, and once installed select Start->GPA icon from the start menu. This will launch the GNU Privacy Assistant which you will use to encrypt and decrypt any communications and generate your initial PGP public key.
- When GPA starts for the first time it will ask you if you wish to Generate a Key or Do it Later. Choose Do it Later and navigate to Keys menu and choose New key….
- When the Generate key wizard displays, enter your username that you intend to use on The Marketplace:
- Click [Forward] and enter a fake email address of {THE-MARKETPLACE-USERNAME}@themarketplace.i2p, E.g. tmptestaccount@themarketplace.i2p. Click [Forward].
- At this stage you can optionally create a backup of your key. This is recommended and you should store the backup on a secure USB stick that only you have access to. This means if you encounter a hardware failure or other problem, you can always decrypt communications for your The Marketplace account, especially important if you’re a vendor. Click [Forward]
- Finally, you will be prompted for a passphrase. Ensure its a memorable, strong password – you will need to use it every-time you want to decrypt a communication.
- You’ve now created the keys you need for your The Marketplace registration, now to export the keys. Right click your new key and select Export Keys… from the menu
- You will be prompted to save the public portion of your key (this is the bit you can circulate to anyone so they can encrypt communications for you) to a file. Choose a location on your hard disk E.g. c:\temp\tmp\mypubkey.txt
- Start Notepad (or your favourite text editor) and open the newly saved public key file. Copy the text content from the file into the The Marketplace registration form and complete the registration process.
- You will now be logged in. Click the Products link from the menu bar and shop for some legal, medicinal remedies. Once you’ve chosen, lets cover how you actually pay for your item… Navigate to your cart and click the [Checkout] button
Your order will now be created and require payment. The Marketplace is unique in that it requires multi-signature transactions, which basically means that you, the vendor and TMP Staff all have keys to your transaction, but in order for any one person to claim it, two of you have to agree. This ensures that the TMP staff can’t walk away with your (or the vendors) money. It would require either collusion between the TMP staff and the vendor, or yourself – either way, the potential damage is limited. On the screen under Order requires payment choose Please click here to create the escrow address 
You will now be requested to enter the Public Key that will be used to create the new wallet to which you will send funds. The terminology says “wallet”, but what it actually means is: “create a new Bitcoin Deposit Address that is unique to this order and to which you will pay your Bitcoins”. Each order will involve creating a different Bitcoin Address, unique to that order into which you will deposit your cash to pay for your order. 
When you are presented with the Create escrow address window, you need to create a Public Key which is used – along with the vendor and TMP Staff’s public keys – to create a unique Bitcoin Address into which you will deposit your money to pay for your goods. This sounds confusing, but what you are basically doing is providing your part of the key in this multi-signature transaction. So, to do this you need to generate a public key. Navigate to https://www.bitaddress.org/ to generate a new Bitcoin Address (NOTE: This Bitcoin Address is nothing to do with your order, it’s just an easy way to generate a public and private key. So don’t accidentally deposit funds to it). Once you generated your Bitcoin Address, it should look something like this: 
- The only bit you are interested in is the Private Key. Copy the Private key value into a text file somewhere and keep it safe DONT LOSE IT. You will need it to authorise or finalise the order or in the case of a dispute.
- Now you need to get the Public Key. On https://www.bitaddress.org/ copy the Private Key to your clipboard and click the Wallet Details tab. Here, enter the Private Key and click the [View Details] button.
- Highlight the Public Key (130 characters [0-9A-F]): value and copy it to your clipboard.
 Return to The Marketplace and paste this into the Public key (SEC) box and click [Create escrow address]
Return to The Marketplace and paste this into the Public key (SEC) box and click [Create escrow address]  Your single use Bitcoin Deposit Address will now be created:
Your single use Bitcoin Deposit Address will now be created: 
Send the exact amount required to this address using the Bitcoin QT client (or Electrum if you are using it) and record the transaction ID. To do this, open Bitcoin-QT and click the [Send] button. Copy the details carefully from The Marketplace order window and send the required funds. You can use the Label: field if you are using Bicoin-QT to record the Private Key you generated in Step 24 for your order (it’s only visible to you). This makes it easier to find the key you need in the event of a refund you need to claim. The format {FRIENDLY-LABEL} – PRIV KEY: {REPURPOSED-BTC-ADDRESS-PRIVATE-KEY} ADDRESS: {REPURPOSED-BTC-ADDRESS} works well.

- Once the funds have been sent, you need to retrieve the transaction id so that The Marketplace knows that you’ve paid. In Bitcoin-QT, click the [Transactions] button, simply highlight the recent transaction you’ve just made, right click and select Copy transaction id. The transaction will be copied to your clipboard.
 The Marketplace will now take over and monitor the transaction. Once it reaches the required number of confirmations, it will be forwarded to the vendor for processing. Note: You can cancel the transaction even after it has been paid but before it has been passed to the vendor. For more information on refunds and how to claim one, see the Refunds section. But we’re not done quite yet! Finally, you need to set your address so the vendor knows when to send your order. Click the [Set Address] button.
The Marketplace will now take over and monitor the transaction. Once it reaches the required number of confirmations, it will be forwarded to the vendor for processing. Note: You can cancel the transaction even after it has been paid but before it has been passed to the vendor. For more information on refunds and how to claim one, see the Refunds section. But we’re not done quite yet! Finally, you need to set your address so the vendor knows when to send your order. Click the [Set Address] button.  You now need to encrypt your delivery address, and send it to the vendor. In the top right hand of the screen, click the [View vendors PGP Key]
You now need to encrypt your delivery address, and send it to the vendor. In the top right hand of the screen, click the [View vendors PGP Key]  A new window will open and inside will be the vendors PGP public key, which you use if you want to send them any correspondence. Copy the text contents of this window to your clipboard, open Notepad (or your favourite text editor), paste it in and save the file to somewhere on your hard-disk, E.g. C:\temp\tmp\myvendorpubkey.txt
A new window will open and inside will be the vendors PGP public key, which you use if you want to send them any correspondence. Copy the text contents of this window to your clipboard, open Notepad (or your favourite text editor), paste it in and save the file to somewhere on your hard-disk, E.g. C:\temp\tmp\myvendorpubkey.txt 
- You can close the browser tab once you’ve saved the key. Just keep the tab that requires your delivery address open.
 Each vendor will have their own key. This ensures that if The Marketplace is ever breached, any communications intercepted between vendors and buyers are effectively unreadable. Click the Clipboard button. The GNU Privacy Assistant – Clipboard is where you encrypt any communications to vendors and decrypt any communications in messages sent to you. Enter your delivery address in the window
Each vendor will have their own key. This ensures that if The Marketplace is ever breached, any communications intercepted between vendors and buyers are effectively unreadable. Click the Clipboard button. The GNU Privacy Assistant – Clipboard is where you encrypt any communications to vendors and decrypt any communications in messages sent to you. Enter your delivery address in the window  Once you have entered it, click the [Encrypt] button and choose the vendors key. The text will be replaced by the encrypted version which can only be decrypted by the intended recipient (your vendor in this case).
Once you have entered it, click the [Encrypt] button and choose the vendors key. The text will be replaced by the encrypted version which can only be decrypted by the intended recipient (your vendor in this case).  Copy this encrypted text to your clipboard and paste it into The Marketplace Update address window and click [Submit].
Copy this encrypted text to your clipboard and paste it into The Marketplace Update address window and click [Submit].  That’s it, your order is now with the vendor. In due course you should receive your order. When you do, you need to login to the site to finalize:
That’s it, your order is now with the vendor. In due course you should receive your order. When you do, you need to login to the site to finalize:  You will now be prompted to leave a review (which you should do for the benefit of other potential customers) and the order life-cycle is complete. If you were unfortunate enough not to receive your order, or have another issue with the buyer, you can open a Dispute. This is covered elsewhere in this guide.
You will now be prompted to leave a review (which you should do for the benefit of other potential customers) and the order life-cycle is complete. If you were unfortunate enough not to receive your order, or have another issue with the buyer, you can open a Dispute. This is covered elsewhere in this guide.
Order Refunds (Order Cancelled, Order Rejected)
Refunds are the mechanism used by TMP to return Bitcoins to a buyer who has:
- paid for an order but decided to cancel it; or
For any order that has been paid but that has not been Approved by the seller, the buyer will be able to claim a refund. Lets cover the process step-by-step from the buyers perspective. NOTE: If you are experimenting to understand the refund process, you will need to use some Bitcoins (the process isn’t risk free). If you are a seller, you can create and purchase one of your own products (See Selling for more information). If you are just an average, curious buyer – find a suitable cheap product from a listed vendor and just [Cancel] the transaction as soon as you have paid for it. Create an order on TMP by following Steps 21 to 35 inclusive of the buyers guide. Immediately after making payment and recording the transaction ID, your order screen should look something like this: You will now be prompted to leave a review (which you should do for the benefit of other potential customers) and the order life-cycle is complete. If you were unfortunate enough not to receive your order, or have another issue with the buyer, you can open a Dispute. This is covered elsewhere in this guide.
For TAILS (Linux) With Electrum
This section covers the setup of the TAILS Secure Linux distribution along with installing the Electrum Bitcoin wallet and the TMP Electrum plugin. We’ll also be covering how to use some of the options provided by the TMP Electrum plugin, including; bulk seller key generation to create a large number of order keys quickly, creating a key (as a buyer) for Refunds and importing transactions (Refunds or Payment Retrival) from TMP for signing (inserting your key as either the buyer or the seller) and broadcast to the Bitcoin network. One of the advantages of using TAILS is that it allows you to segregate your darknet activities from your main operating system (OS), however by design TAILS is forgetful. That means that every-time you reboot it, it’s as if you never used it. Any data that you created (PGP keys, wallets, installed applications etc) during your previous use of TAILS is lost. To remedy this, the TAILS OS provides the ability to configure persistent storage. Persistent storage reserves a bit of space on your USB or SD Card to allow configuration files and data to carry over between each reboot. In order to configure persistence, you need to do it from within the TAILS operating system. Before we begin, you will need a blank DVD and a USB or SD Card available. You will use the DVD to get the TAILS running and then you will use the USB or SD Card to create a new installation of TAILS that has persistent storage enabled. This is all covered in detail below. Note: If you are running virtualisation software such as VMWare Workstation (Windows), VMWare Fusion (Mac) or Virtualbox on your computer, you can use this in place of the blank DVD to get TAILS initially started. You can also opt to use a second USB stick or SD Card in place of the DVD – installation instructions are provided here: Manually installing TAILS onto a USB Stick or SD card. Let’s begin…
- Download the TAILS iso image from the TAILS website: https://tails.boum.org/download/#index2h1 and save it somewhere on your hard-disk (E.g. c:\temp\tails-i386-0.22.iso)
 Choose click [Forward]
Choose click [Forward] When the Tails installer window displays, insert your USB stick or SD Card into your PC and choose [Clone] & Install
When the Tails installer window displays, insert your USB stick or SD Card into your PC and choose [Clone] & Install

- Your USB Drive or SD Card should be listed in the drop-down box. If you have multiple USB devices or SD Cards connected, select the correct one and click [Install Tails]. Remember; you will lose everything on the USB stick or SD Card, so if you are in any doubt which USB or SD Card is the correct one, remove all except the one you are going to use to install TAILS with persistent storage onto.

- When the process is finished, you should receive a confirmation dialog. Your portable, persistent storage-able (but not enabled yet) TAILS installation is now ready.
 Reboot the system using the leaving the USB stick or SD card in place. If your PC is not set to boot from an SD Card or USB stick, you will need to enter the BIOS as you did in Step 1. Refer to your motherboard manufacturers guide if you are in any doubt about how to do this.
Reboot the system using the leaving the USB stick or SD card in place. If your PC is not set to boot from an SD Card or USB stick, you will need to enter the BIOS as you did in Step 1. Refer to your motherboard manufacturers guide if you are in any doubt about how to do this.

- Once your PC has restarted, you want to this time select ‘Yes’ for additional options and enter a root password. Normally you do not want root enabled, but we will need it to set up some persistence settings. We now need to create the persistent storage volume. This tells TAILS what you want to allow to persist between reboots and that you want to reserve a bit of space on the USB stick or SD card to store all this information.
Open the ‘Configure persistent volume’ in the Application menu. Remember; it’s protecting the evidence (not that you’ve anything to hide…) so don’t pick a password you’ve used anywhere else (Facebook, Gmail etc), make it strong and don’t forget it! (There is no recovery if you do).  When you’ve chosen, click the [Create] button.
When you’ve chosen, click the [Create] button.
- You want to keep as little as possible around, but you want at least ‘Personal Data’, GnuPG, and Dotfiles. Browser bookmarks may be good if you’re not good at remembering, but you can store important websites in another way that’s a bit more safe.

 Click the [Save] button to commit your changes.
Click the [Save] button to commit your changes.


 Under Use persistence? choose [Yes] and in the Passphrase box, enter the password to your persist volume that you entered in Step 11. Leave the Read-Only? box unchecked. Do not click on ‘More options’. You will not need to enable it except for rare situations.
Under Use persistence? choose [Yes] and in the Passphrase box, enter the password to your persist volume that you entered in Step 11. Leave the Read-Only? box unchecked. Do not click on ‘More options’. You will not need to enable it except for rare situations.
 Ignore the router window or minimize it when it opens up. Now we will want to open Iceweasel, (it’s the globe icon right next to System, and go to and get the latest version of Electrum. Select the ‘Open with Archive Manager’ option so that you can extract it to the correct directory when it’s done.
Ignore the router window or minimize it when it opens up. Now we will want to open Iceweasel, (it’s the globe icon right next to System, and go to and get the latest version of Electrum. Select the ‘Open with Archive Manager’ option so that you can extract it to the correct directory when it’s done.



- We want to set up scripts to start up Electrum correctly. We want to make sure it always connects to the correct servers and that we keep our escrow address keeps seperate from our cash handling keys. You can modify the ‘electrum.desktop’ file to save a script to run Electrum for monies.
 Modify the file silghtly again and save as a newfile, one for a wallet that onlydoes key storage and signing for you.
Modify the file silghtly again and save as a newfile, one for a wallet that onlydoes key storage and signing for you.
 Create a new password database. Be sure to pick a very strong password to use to keep all your passwords in. If you lose this, you’ll likely not ever be able toget back into your accounts.
Create a new password database. Be sure to pick a very strong password to use to keep all your passwords in. If you lose this, you’ll likely not ever be able toget back into your accounts.

 Then use the password generator to make a secure password.
Then use the password generator to make a secure password.

 Now you have to save your password database. It’s important you save your password database after every new password entry you create in the password vault.
Now you have to save your password database. It’s important you save your password database after every new password entry you create in the password vault. 

- By now I2P should’ve had time to get ready for use. Disable Javacript on your browser, then head over to http://themarketplace.i2p.
 You are likely going to get an error message becasue your router doesn’t know how to get to the market yet. Pick the stats.i2p jump service link, then select the open to save the domain to the counter and continue on.
You are likely going to get an error message becasue your router doesn’t know how to get to the market yet. Pick the stats.i2p jump service link, then select the open to save the domain to the counter and continue on.

 We will go to the forum first to pick up the add-on. Fill out the registration info in the registration link. Since you don’t know (or care) whan gibberish your password is, you can easy right click on the account in KeePassX to copy the password into the clipboard so you can paste it in the correct field. Then navigate to the plugin thread and download the latest copy.
We will go to the forum first to pick up the add-on. Fill out the registration info in the registration link. Since you don’t know (or care) whan gibberish your password is, you can easy right click on the account in KeePassX to copy the password into the clipboard so you can paste it in the correct field. Then navigate to the plugin thread and download the latest copy. 



 You now want to run each one of the startup scripts to create two wallets. Remember, if you need a password, be sure to generate a fresh one in KeePassX and save the password after creation.
You now want to run each one of the startup scripts to create two wallets. Remember, if you need a password, be sure to generate a fresh one in KeePassX and save the password after creation. 
 Also, it’s extremely important to save your electrum seed words for each wallet. With your seed words you can recover every non-importated transaction in the wallet. Without it, you can be in a very bad spot. Save them seperately in a secure location.
Also, it’s extremely important to save your electrum seed words for each wallet. With your seed words you can recover every non-importated transaction in the wallet. Without it, you can be in a very bad spot. Save them seperately in a secure location.  Then you can load the TMP plugin.
Then you can load the TMP plugin. 

- Finally, to round of this exercise, lets shutdown and check that all the hard work has been persisted. Now you want to exit electrum and reinter it without the admin password or additional options being enabled.
Additional information on PGP key management and detail on the TMP plugin will follow in subsequent versions of this guide (hopefully). Final note: there is probably a great deal more integration and optimization that can be done and you should not interpret this as the defacto guide to best practice – the author is not an expert. It should get you up and running with a degree of security and once you are happy, you can begin experimenting with the additional functionality afforded by TAILS.
Order Refunds (Order Cancelled, Order Rejected)
Refunds are the mechanism used by TMP to return Bitcoins to a buyer who has:
- paid for an order but decided to cancel it; or
For any order that has been paid but that has not been Approved by the seller, the buyer will be able to claim a refund. Lets cover the process step-by-step from the buyers perspective. NOTE: If you are experimenting to understand the refund process, you will need to use some Bitcoins (the process isn’t risk free). If you are a seller, you can create and purchase one of your own products (See Selling for more information). If you are just an average, curious buyer – find a suitable cheap product from a listed vendor and just [Cancel] the transaction as soon as you have paid for it. Create an order on TMP by following Steps 21 to 35 inclusive of the buyers guide. Immediately after making payment and recording the transaction ID, your order screen should look something like this:  It does not matter if your payment has received any confirmations – just click the [Cancel order] button. The order will vanish from your list (This can be slightly confusing since TMP does not at the time of writing provide any feedback to you as a buyer, but don’t worry – your refund exists). From the menu on the left-hand side under the Orders heading, click the [Refunds] link to bring up the Refunds Window:
It does not matter if your payment has received any confirmations – just click the [Cancel order] button. The order will vanish from your list (This can be slightly confusing since TMP does not at the time of writing provide any feedback to you as a buyer, but don’t worry – your refund exists). From the menu on the left-hand side under the Orders heading, click the [Refunds] link to bring up the Refunds Window:  When the window displays, you will see a list of all the Refunds that are available for you to claim. Remember: One paid cancelled or declined order = one refund. In the Withdraw to wallet field, enter the Bitcoin Address you want your refund sent to and click the [Sign] button. This can be any Bitcoin Address – for example an exchange deposit address, a blockchain.info wallet address, a paper wallet address etc. Wherever you like, just make sure you own it.
When the window displays, you will see a list of all the Refunds that are available for you to claim. Remember: One paid cancelled or declined order = one refund. In the Withdraw to wallet field, enter the Bitcoin Address you want your refund sent to and click the [Sign] button. This can be any Bitcoin Address – for example an exchange deposit address, a blockchain.info wallet address, a paper wallet address etc. Wherever you like, just make sure you own it.  The Transaction window will now be displayed – DONT PANIC! It looks complicated, but its pretty straightforward once you get the hang of it. Remember the Concepts? TMP has taken your requested refund Bitcoin Address and created a signed transaction (inserted their key) into the Bitcoin Deposit Address that your Bitcoins are currently sitting in. So, in order for those Bitcoins to be released to you, you – as the buyer – also need to sign on the dotted line (insert your key). Once you’ve signed off, you can broadcast the transaction to the Bitcoin network and the Bitcoins will wing their way to your nominated Bitcoin Address.
The Transaction window will now be displayed – DONT PANIC! It looks complicated, but its pretty straightforward once you get the hang of it. Remember the Concepts? TMP has taken your requested refund Bitcoin Address and created a signed transaction (inserted their key) into the Bitcoin Deposit Address that your Bitcoins are currently sitting in. So, in order for those Bitcoins to be released to you, you – as the buyer – also need to sign on the dotted line (insert your key). Once you’ve signed off, you can broadcast the transaction to the Bitcoin network and the Bitcoins will wing their way to your nominated Bitcoin Address.  In the subsequent steps, you’ll be running two commands:
In the subsequent steps, you’ll be running two commands:
- signrawtransaction: Allows you to sign-off the transaction (inserts your key into the Bitcoin Deposit Address)
To run these commands you will need to have Bitcoin-QT installed and connected to the internet. You will also need the Private Key from your repurposed Bitcoin Address that you stored when you created your order (See Steps 24-to-27 in the Buyers Guide). Before we get to the Bitcoin-QT commands, we’re going to decode and check the transaction on https://blockchain.info/decode-tx. This (and the following step) are purely optional stages, but just lets you feel comfortable that your refund is going to go to the Bitcoin Address you have nominated. Highlight the text between the quotes as demonstrated in the screenshot below, and copy it to your clipboard:  Navigate to https://blockchain.info/decode-tx inside the TOR browser (to protect your privacy) and paste the text in and click the [Submit Transaction]. The result should be something like that shown below:
Navigate to https://blockchain.info/decode-tx inside the TOR browser (to protect your privacy) and paste the text in and click the [Submit Transaction]. The result should be something like that shown below:  Now that you’re happy with the proposed refund, you want to sign it off and get back the Bitcoins. Open Bitcoin-QT, go to Menu->Debug Window and click the Console tab. The view should look like this:
Now that you’re happy with the proposed refund, you want to sign it off and get back the Bitcoins. Open Bitcoin-QT, go to Menu->Debug Window and click the Console tab. The view should look like this: 
- You now need to create the signrawtransaction command from the transaction text provided by TMP and the Private Key from the repurposed Bitcoin Address. Mercifully, there are some quick and dirty formatting tools to do most of the work for you at the base of this guide under the Transaction String Formatting – Refunds heading. There are two stages:
- Stage 2. Generate *REFUND* DOS bitcoind.exe compatible or Bitcoin-QT GUI Debug compatible sendrawtransaction command
-
We’re going to use these tools, click the link to Stage 1 above, and paste the requested values into the boxes (The Private Key and the TMP signed transaction text). A helpful screenshot tells you what text you need to copy from the TMP window. Once you’ve done this, click the [Format Refund Transaction] button and copy the blue result text that appears below to your clipboard.
 The very last step is to return to TMP and click the [Mark as Claimed] button. This just removes the refund from your list so don’t [Mark as Claimed] until you’ve confirmed your Bitcoins have been successfully refunded.
The very last step is to return to TMP and click the [Mark as Claimed] button. This just removes the refund from your list so don’t [Mark as Claimed] until you’ve confirmed your Bitcoins have been successfully refunded. 
Selling on The Marketplace
This section covers the setup of your shop and the creation and sale of your first product. The great thing at TMP is that you can configure your store-front and sell yourself one of your products without having to actually obtain full permission from TMP staff to offer products. No one else will be able to buy your products until you are approved, but it does provide a great way to test the process end-to-end without relying on some third party to buy something. The product that we will be creating will be a test. Note: that you will pay a service fee for every completed order to TMP, even if you’ve sold to yourself. So we’ll be using the minimum values possible to reduce your exposure but the process won’t be free. Log in to your TMP account and select the [Become a vendor] menu option on the left hand side: 
- Review the Security Policy and Vendor Agreement. Once you are satisfied, select [Continue] from Vendor Agreement screen.
 In the Vendor Creation: Profile window, provide some information about yourself, your terms and conditions etc and click [Next]
In the Vendor Creation: Profile window, provide some information about yourself, your terms and conditions etc and click [Next]  In the final agreement window, click [Finish] and your shop will be created. You will now notice that a Shop Management icon has appeared across the top of your menu. Click this to navigate to the shop interface. Note: To approve your shop so that you can receive real orders, you will need to contact the individual listed. This is not necessary for the purposes of this test shop, but remember; until approved your shop is only visible to you.
In the final agreement window, click [Finish] and your shop will be created. You will now notice that a Shop Management icon has appeared across the top of your menu. Click this to navigate to the shop interface. Note: To approve your shop so that you can receive real orders, you will need to contact the individual listed. This is not necessary for the purposes of this test shop, but remember; until approved your shop is only visible to you.  The Shop Management interface gives you an overview of your orders, allows you to manage products, shipping options, orders and – most important – retrieve Bitcoins stored in Bitcoin Deposit Addresses from completed orders. The screen has been annotated below:
The Shop Management interface gives you an overview of your orders, allows you to manage products, shipping options, orders and – most important – retrieve Bitcoins stored in Bitcoin Deposit Addresses from completed orders. The screen has been annotated below: 
- Lets start by dealing with the most complicated part; creating the keys (read: “wallets” in TMP terminology) you need for orders that you will receive. Click the [Wallets] link on the left hand side and the
 As a seller, you therefore need a large stock of keys that can be used by TMP and your buyers to generate a unique Bitcoin Deposit Address. For every Bitcoin Deposit Address created, one of your keys is consumed. Annoyingly this can mean that buyers can enter their key, TMP generates the Bitcoin Deposit Address using one of yours, one of its own and the buyers key, but then the buyer doesn’t pay and you’re down a key. It is therefore important to remember that the signing wallet count (See Step 6 screenshot) is not reflective of the number of orders you will have. Unpaid orders will never be seen by you – they just cost you a key. Since a key (read: “wallet”) is just a repurposed Bitcoin Address, there are a number of ways to generate them. One of the easiest way to create a bulk lot of Bitcoin Addresses is using the Bitcoind.exe that comes with Bitcoin-QT (see prerequisites for links). This is a great way to do it because bitcoind then takes care of storing your Bitcoin Addresses (your keys) securely in its own wallet.dat and you can also easily access the private part of each ‘key’ that you need when you come to claim your Bitcoins from completed orders. You’re basically using Bitcoin-QT as a vault to store all your order keys. A guide on this will be covered elsewhere. Note: Bitcoin-QT does not need to be connected to the internet, you can create your Bitcoin Addresses you will use as keys completely offline – the magic of Bitcoin math. The second, simplest but more manually intensive way is to use a Bitcoin Address generator website. Because this is a simple guide to get you into the swing of things, that’s what we’re going to use.
As a seller, you therefore need a large stock of keys that can be used by TMP and your buyers to generate a unique Bitcoin Deposit Address. For every Bitcoin Deposit Address created, one of your keys is consumed. Annoyingly this can mean that buyers can enter their key, TMP generates the Bitcoin Deposit Address using one of yours, one of its own and the buyers key, but then the buyer doesn’t pay and you’re down a key. It is therefore important to remember that the signing wallet count (See Step 6 screenshot) is not reflective of the number of orders you will have. Unpaid orders will never be seen by you – they just cost you a key. Since a key (read: “wallet”) is just a repurposed Bitcoin Address, there are a number of ways to generate them. One of the easiest way to create a bulk lot of Bitcoin Addresses is using the Bitcoind.exe that comes with Bitcoin-QT (see prerequisites for links). This is a great way to do it because bitcoind then takes care of storing your Bitcoin Addresses (your keys) securely in its own wallet.dat and you can also easily access the private part of each ‘key’ that you need when you come to claim your Bitcoins from completed orders. You’re basically using Bitcoin-QT as a vault to store all your order keys. A guide on this will be covered elsewhere. Note: Bitcoin-QT does not need to be connected to the internet, you can create your Bitcoin Addresses you will use as keys completely offline – the magic of Bitcoin math. The second, simplest but more manually intensive way is to use a Bitcoin Address generator website. Because this is a simple guide to get you into the swing of things, that’s what we’re going to use.
- In a separate browser window, navigate to https://www.bitaddress.org/. Move your mouse around (if prompted) to begin the initial Bitcoin Address generation process. Once it has returned a Bitcoin Address, open Notepad or your favourite text editor (or you can use Excel). Add three columns; “Bitcoin Address”, “Private Key” and “Public Key (130 Chars)” and copy the Bitcoin Address and Private Key into the Notepad file. Leave the Public Key column blank, we’ll populate that presently. Repeat this process to generate two addresses, the resultant Notepad file should look like:


 Once you’re done, click the [Add Wallets] button to store your keys in your account.
Once you’re done, click the [Add Wallets] button to store your keys in your account.

 You’ll be returned to the Shipping Options screen where your available options will be summarised.
You’ll be returned to the Shipping Options screen where your available options will be summarised. 


 Click the View on site. This will open a new tab showing your product. Select a Shipping Option and choose [Add to Cart]
Click the View on site. This will open a new tab showing your product. Select a Shipping Option and choose [Add to Cart]  The product will now be added to your cart and you’ll be able to preview the process as any buyer would. In order to save space, navigate back up this guide and follow Steps 21 to 35 inclusive of the buyers guide. Once you’ve done that, return here and click the Shop Management link to return to the shop management overview screen.
The product will now be added to your cart and you’ll be able to preview the process as any buyer would. In order to save space, navigate back up this guide and follow Steps 21 to 35 inclusive of the buyers guide. Once you’ve done that, return here and click the Shop Management link to return to the shop management overview screen.







- The second command is sendrawtransaction and all this does is broadcast the transaction you signed to the Bitcoin network (need a Bitcoin-QT client with an internet connection for this). Only then can the actual Bitcoin transfer take place (remember; Bitcoin is a big distributed ledger, it has to know about it, or it didn’t happen).Now that you (hopefully) understand the commands you are going to run – you need to run them. To be able to that we are now going to switch back to Bitcoin-QT which you’ve hopefully got running.

- You now need to insert the private key in place of the text marked PRIVATEKEYHERE in the string and then copy everything from the word signrawtransaction to your clipboard and paste the result into the Bitcoin-QT debug window. Mercifully, there are some quick and dirty string formatting tools to do most of the work for you at the base of this guide under the Transaction String Formatting – Payment Retrieval heading.
 The very last step is to return to TMP and click the [Mark as Claimed] button. This just removes the transaction from your list so don’t [Mark as Claimed] until you’ve confirmed your Bitcoins have been successfully redeemed.
The very last step is to return to TMP and click the [Mark as Claimed] button. This just removes the transaction from your list so don’t [Mark as Claimed] until you’ve confirmed your Bitcoins have been successfully redeemed.  A few final words. Don’t worry about re-running the claim commands a few times, when you broadcast the transaction (sendrawtransaction) the Bitcoin network will only recognise the first successful attempt, so any further tries won’t yield more Bitcoins, they’ll just be ignored.
A few final words. Don’t worry about re-running the claim commands a few times, when you broadcast the transaction (sendrawtransaction) the Bitcoin network will only recognise the first successful attempt, so any further tries won’t yield more Bitcoins, they’ll just be ignored.
Finalising transactions outside of The Marketplace
In this section we cover how to go about recovering Bitcoins from a Bitcoin Deposit Address without using TMP. The purpose is to illustrate that, in the event of TMP collapsing, sellers and buyers can still complete outstanding paid orders lessening the financial impact on both the parties involved (buyer and seller). If you have not covered the Concepts section of this guide, take a moment to recap before continuing. Since this tutorial is primarily aimed at sellers, we’re going to be selling ourselves a product (See Selling on The Marketplace section). This makes it easy to ensure we’ve got access to the necessary keys required to unlock the Bitcoins in the Bitcoin Deposit Address for the order we’re going to create. Before beginning, there are a few things that – sellers especially – should be aware of. In order to recover any of the Bitcoins that reside in an order Bitcoin Deposit Address, both the seller and the buyer have to be able to contact each other. This is necessary because either the buyer or the seller is going to need to fill the shoes of TMP and create and sign a transaction (insert their key) that will then be provided to the counter-party to also sign-off on (insert their key) and broadcast the result to the Bitcoin network so the Bitcoins can be released from the Bitcoin Deposit Address. Since a buyer and a seller do not ever come into direct contact with each-other through TMP except when using TMP’s messaging system (remember; orders a seller receives are never explicitly tied to a TMP buyer’s account), establishing communication channels can be the trickiest part. As a general rule of thumb, buyers who have paid for an order but who have not had their order accepted by a seller at the time of TMP’s closure or have not yet received a shipped order, are going to be more inclined to make the effort to get in contact with the seller. Buyers who have received their order but had not Finalized it at the time of TMP’s closure are significantly less likely to make the effort to help the seller recover any Bitcoins trapped in the Bitcoin Deposit Address for the particular order. The buyer won’t be able to recover the Bitcoins either, so there is no financial gain – it just means that the Bitcoins will remain trapped in eternity until either TMP recovers, or the two parties (buyer and seller) can get in contact and come to an agreement. To summarise; as a seller do not assume you will be able to recover all outstanding funds owed to you for shipped orders. You should be able to recover something though, and something is better than nothing. It’s also 100% more than traditional trust based darknet markets (E.g. Pandora, SilkRoad2, BlueSky etc). Note: If TMP subsequently returns after an outage, a seller can set about reclaiming any Bitcoins in outstanding orders where the buyer was uncontactable, using the platforms built in mechanisms (See Steps 23-to-34 in the Sellers section) and a buyer can set about recovering Bitcoins from any Unapproved order through the refund mechanism (See All steps in the Order Refunds section). It may be a bit of an auditing headache to reconcile everything; remove orders that have been claimed outside TMP and claim orders that haven’t, but that’s it. Because the Bitcoins for each paid order are sitting in their Bitcoin Deposit Address it’s just a matter of claiming them. A seller doesn’t have to trust TMP to have a wallet filled with Bitcoins to back an ephemeral website balance (Think: Sheep Market and the Bitcoin withdrawal issues suffered near its end when someone had run away with all the money). How a seller and their buyers get in contact with each-other is a matter of personal choice. It could be as simple as including a contact email address on the vendor profile, posting a PGP encrypted message (encrypted with the public PGP key of the recipient) on a high-traffic social platform such as Reddit, or through a more secure durable communication platform such Bitmessage combined with TOR (recommended approach). Note: The use of Bitmessage is not covered in this tutorial. Links to a simple tutorial are provided in the Prerequisites section of this guide. Let’s begin… Place an order with yourself by following Steps 8 to 18 inclusive of the Sellers section. Click the [Shop Management] link on the top menu-bar to view your shops overview. You should see your recently paid order sitting in the New Orders sub-window: 
 Click the [View] button adjacent to order to bring up the order detail screen. When this displays, click the [Show Payment Information] button along the top:
Click the [View] button adjacent to order to bring up the order detail screen. When this displays, click the [Show Payment Information] button along the top:  to display the payment information associated with this order:
to display the payment information associated with this order:  Now that you hopefully have a better understanding of the information shown on the Payment Information screen, you will want to know which bits are actually relevant to make you able to retrieve the Bitcoins outside of TMP. The only pieces of information you need from this screen are:
Now that you hopefully have a better understanding of the information shown on the Payment Information screen, you will want to know which bits are actually relevant to make you able to retrieve the Bitcoins outside of TMP. The only pieces of information you need from this screen are:
- The Redeem Script; and
You might be wondering why you don’t need the other ‘Public’ keys? You don’t need them because – as the seller – you already have the ‘Private’ part of your key to the Bitcoin Deposit Address, which you recorded in your Notepad file in Steps 8, 9 and 10 of the Sellers section. The ‘Private’ part of your Bitcoin Deposit Address key is effectively the real key, while the ‘Public’ part is the equivalent of being able to tell the world that you have ownership of the ‘Private’ part but doesn’t allow anyone who has it to use it to move Bitcoins out of the Bitcoin Deposit Address. ‘Private’ trumps ‘Public’. You are recording the sellers public key because it will make it easier for you to track down the correct Private Key to use to sign-off the transaction. If you’ve got 1000′s of keys – all for different orders – it would be a management nightmare trying to work out which Private Key you needed to use to unlock the Bitcoin Deposit Address. Recording it here means you can just search the Notepad file you created Step 10 of the Sellers section (or whatever storage method you’ve chosen to use). Note: Because you are also acting as the buyer in this tutorial, you will also have access to the buyers Private key which you recorded in Steps 24 and 25 of the Buyers section when you placed your order. In normal circumstances you would not have access to this and so once you created and signed the transaction (inserted your key), you would pass the signed transaction to the buyer for them to also sign-off (insert their key) and broadcast the result to Bitcoin Network to release the Bitcoins from the Bitcoin Deposit Address. Don’t worry, this will all be covered in detail in the following steps. Open Notepad or your favourite text editor, and create four columns: Bitcoin Deposit Address, Transaction ID, Redeem Script and Sellers Public Key. Copy the values from the Payment Information screen. The result should look something like this:  You now have the information you – as the seller – need to create and sign (insert your key) the transaction. For the next part we’re going to be using a combination of https://blockchain.info/rawtx (Visit in TOR) and the Bitcoin-QT Debug window. You can do everything in the Bitcoin-QT Debug window but by using blockchain.info, we minimize the chances of mistakes. The Bitcoin commands we will be running are:
You now have the information you – as the seller – need to create and sign (insert your key) the transaction. For the next part we’re going to be using a combination of https://blockchain.info/rawtx (Visit in TOR) and the Bitcoin-QT Debug window. You can do everything in the Bitcoin-QT Debug window but by using blockchain.info, we minimize the chances of mistakes. The Bitcoin commands we will be running are:
- createrawtransaction: (Run by: Seller) – Creates the transaction that releases the Bitcoins from the Bitcoin Deposit Address to the sellers chosen Bitcoin Address (a paper wallet, blockchain.info wallet or Bitcoin exchange – any Bitcoin Address the seller owns)
To run the commands open Bitcoin-QT, go to Menu->Debug Window and click the Console tab. The view should look like this: 
- To create the raw transaction, we need to know some information about the transaction that was used to deposit the Bitcoins into the Bitcoin Deposit Address. Fortunately, blockchain.info stores this information in an easily accessible manner, but you need to go to a special URL to get it. You can reach it by manually putting https://blockchain.info/rawtx/{REPLACE-ME-WITH-THE-TRANSACTION-ID-YOU-RECORDED-IN-THE-TEXT-FILE-IN-STEP-3}?scripts=true into your address bar, but mercifully, tools exist under the Transaction String Formatting – Create My Own Raw Transaction to guide you through the process (which is what we’ll use). The five stages are:
- Stage 2. Generate *RAWTX* DOS bitcoind.exe compatible or Bitcoin-QT GUI Debug compatible createrawtransaction command
- Stage 3. Generate *SELLERS RAWTX* DOS bitcoind.exe compatible or Bitcoin-QT GUI Debug compatible signrawtransaction command
- Stage 4. Generate *BUYERS RAWTX* DOS bitcoind.exe compatible or Bitcoin-QT GUI Debug compatible signrawtransaction command
- Stage 5. Generate *BUYER OR SELLER RAWTX* DOS bitcoind.exe compatible or Bitcoin-QT GUI Debug compatible sendrawtransaction command
-
Click the link to Stage 1 above, and paste the requested value into the boxes (The Transaction ID) to generate the blockchain.info link. Copy the link into your browser address bar (or click it) and copy all the text in the box highlighted onto your clipboard. Helpful screenshots by the stages tell you what text you need to copy where.

 Once you’ve got the signrawtransaction command text back from half-way through Stage 3, run it in Bitcoin-QT Debug window. Notice that the result says complete: false (highlighted in green in the screenshot below). This means that only one signatory (you; the seller) has signed off (inserted their key). One more signatory is required (the buyer) before the Bitcoins in the Bitcoin Deposit Address can be released.
Once you’ve got the signrawtransaction command text back from half-way through Stage 3, run it in Bitcoin-QT Debug window. Notice that the result says complete: false (highlighted in green in the screenshot below). This means that only one signatory (you; the seller) has signed off (inserted their key). One more signatory is required (the buyer) before the Bitcoins in the Bitcoin Deposit Address can be released. 
 Copy the resulting black text (everything inside the red box in the screenshot above) into the Seller Signed Transaction Text box midway through Stage 3 and click the [Generate Transaction Signing Text For Buyer]. At this stage, you would normally send the resulting text to the buyer who would then continue the process from Stage 4, but since you are also the buyer just paste the resulting output into the Transaction Text provided to you by the Seller box along with the buyers Private Key (You should have hopefully stored this when you paid for your order – see Steps 24-to-27 in the Buyers Section to recap). Press the [Generate Buyers Transaction Signing Command] and run the resulting output in Bitcoin-QT Debug Window. If the process has worked, you will see complete: true (highlighted in green in the screenshot below) . This is the gold you are looking for. This means the transaction is ready to be broadcast to the Bitcoin Network. The money is nearly yours!
Copy the resulting black text (everything inside the red box in the screenshot above) into the Seller Signed Transaction Text box midway through Stage 3 and click the [Generate Transaction Signing Text For Buyer]. At this stage, you would normally send the resulting text to the buyer who would then continue the process from Stage 4, but since you are also the buyer just paste the resulting output into the Transaction Text provided to you by the Seller box along with the buyers Private Key (You should have hopefully stored this when you paid for your order – see Steps 24-to-27 in the Buyers Section to recap). Press the [Generate Buyers Transaction Signing Command] and run the resulting output in Bitcoin-QT Debug Window. If the process has worked, you will see complete: true (highlighted in green in the screenshot below) . This is the gold you are looking for. This means the transaction is ready to be broadcast to the Bitcoin Network. The money is nearly yours! 
- Copy all the black text highlighted in the red box in the screenshot above to your clipboard and paste it in to the Signed Transaction Text provided by the Buyer box in Stage 5. Click the [Generate Buyer-Seller Signed Broadcast Transaction Command] to generate the final command.

- That’s it. You’re done. Really. You may wish to house-clean so you don’t have a now unusable order clogging up your list. You can do that by declining it in the Shop Management view, and then – as the buyer – navigating to your refunds screen and just putting a random Bitcoin address into the claim screen and hitting the [Mark As Claimed] button. For detailed overview of the Refund process, see the Refunds section.
A final cautionary note. Although (if you’re suitably masochistic) you might be thinking that you can circumvent TMP’s fees this way, you can – but they’ll find out. Remember, TMP is a key holder in every order, so it is trivial for them check paid Bitcoin Deposit Addresses and see which ones have had their funds spent without giving TMP their fee… repeat offenders (without mitigating circumstances) are likely to risk having their accounts closed. It’s in everyone’s interest to ensure everyone else gets their slice of the cake, so that buyers and sellers have somewhere safe, secure and reliable to conduct business on.
Transaction String Formatting
The default string that is provided when you want to claim a transaction does not work with the Windows Bitcoin Daemon. The reason is the escapement of quotes. This JavaScript will format the transaction into a block you can paste into a DOS box and get your signed transaction from.
Payment Retrieval
Stage 1. Generate DOS bitcoind.exe or Bitcoin-QT GUI Debug compatible signrawtransaction command
Private Key: Transaction text:
Result (Paste this into your DOS command box):
or
Result (Paste this into your Bitcoin-QT GUI Debug box):
Stage 2. Generate DOS bitcoind.exe compatible or Bitcoin-QT GUI Debug compatible sendrawtransaction command
Paste the result of the transaction text below to generate the final command you need to run to claim your funds
Result (Paste this into your DOS command box):
or
Result (Paste this into your Bitcoin-QT GUI Debug box):
Refunds
Stage 1. Generate *REFUND* DOS bitcoind.exe or Bitcoin-QT GUI Debug compatible signrawtransaction command
Private Key:
Transaction text:
Result (Paste this into your DOS command box):
or
Result (Paste this into your Bitcoin-QT GUI Debug box):
Stage 2. Generate *REFUND* DOS bitcoind.exe compatible or Bitcoin-QT GUI Debug compatible sendrawtransaction command
Paste the result of the transaction text below to generate the final command you need to run to claim your refund
Result (Paste this into your DOS command box):
or
Result (Paste this into your Bitcoin-QT GUI Debug box):
Create My Own Raw Transaction
These tools are used to create raw transactions for you. They are used in conjunction with the Finalising transactions outside of The Marketplace section of this guide.
Stage 1. Generate *RAWTX* URL on blockchain.info
Transaction ID:
Result (Paste this into your Brower address bar or just click it):
Stage 2. Generate *RAWTX* DOS bitcoind.exe compatible or Bitcoin-QT GUI Debug compatible createrawtransaction command
Copy everything from blockchain.info in the browser window (Stage 1 above) into the Transaction text: box below. Note: Stage 2 and Stage 3 need to be done one after the other.
Transaction Text: (From the blockchain.info website)Bitcoin Deposit Address: (Sourced from the TMP Payment Information screen – under the Escrow Wallet heading)Redeem Script: (Sourced from the TMP Payment Information screen)Destination Bitcoin Address: (Where the Bitcoins in the Bitcoin Deposit Address will be sent)
Miners Fee (Minimum of 0.0001 BTC): BTCSummmary
Amount of BTC that you will receive:
Amount of BTC the Miners will get as a fee:
The total value of the transaction (Miners fee + What you receive):
Result (Paste this into your DOS command box):
or
Result (Paste this into your Bitcoin-QT GUI Debug box):
Stage 3. Generate *SELLERS RAWTX* DOS bitcoind.exe compatible or Bitcoin-QT GUI Debug compatible signrawtransaction command
This stage depends on the values (Bitcoin Deposit Address, Redeem Script etc) that you have hopefully just entered in Stage 2. If not, complete Stage 2 before moving on to this stage and don’t clear the boxes.
Paste the result of the createrawtransaction command from Step 2 into the Unsigned Transaction Text: box below to sign the transaction as the Seller
Sellers Private Key: (Your key – as the seller – to the Bitcoin Deposit Address)
Unsigned Transaction Text:
Result (Paste this into your DOS command box):
or
Result (Paste this into your Bitcoin-QT GUI Debug box):
Now paste the result of the signrawtransaction command you’ve just run into the Seller Signed Transaction Text box below to generate the command you can send to the buyer to run (Isn’t this fun?)
Seller Signed Transaction Text:
or
Result (Send this to the Buyer and ask them to enter it into Stage 4 below to complete the signing process):
Stage 4. Generate *BUYERS RAWTX* DOS bitcoind.exe compatible or Bitcoin-QT GUI Debug compatible signrawtransaction command
As the Buyer, you will need the Private Key from your repurposed Bitcoin Address that you stored when you created your order (See Steps 24-to-27 in the Buyers Section) to sign the transaction the seller has sent you. This will enable you (or the seller) to release the Bitcoins stored in the Bitcoin Deposit Address (See Stage 5).
The text you are pasting in should look something like this:
signrawtransaction 01000000014a4ba53608f7d2fb6f478d9e1f71c6f2f67de765
958430fcfa969bdad3d1af14730440220692fdee8d5dd7c2aa9109731f4eeeb
6ba751d7863b26a201000000f400539985aeb5a438a06bef976c5b6858b7a7
f44965dd9f7dde80e47911902202833ab1c66fe878b1b0
ca9474920c21ad49c6449e10d6e54fbf1471ce4d794c1658462a22d112eeaedef
7a7aad8be912fb33737aa1017327af13a5d8bb721c65c5
861ba52368119941045d2e9b84c928de41495356d692ca91daa41f49d7464b5
7cdec1b9b63be3b36deb969bd4fbf1471ce4d794c165be
bf4aed59cce2a2ca2b223aed122102b63b8203f05249767712175200901db1c70
d836171df2fd05afeb016e42f3a2953aeffffffff01
f7bf1400000000001976a914c3e998b45efd5ccd99a560019103fc6bf83f5a50
88ac00000000 [{\”txid\”:\”de7c252a46a8cf
0f43585d751a76bf11a3d976da2263b86adc1ef70836a54b4a\”,\”vout\”:1,
\”scriptPubKey\”:\”a3d1014815899171c46a9ba3f
7445ce6b1bd4b05485187\”,\”redeemScript\”:\”7ec170d2963831ec34d95
b29158a06b2d112eeaedef7a7aad8be9134d95b22
41045a9b63be3b36deb85aeb5a432fb33737aa
1017327af13a5d8bb721c65c5861ba52368119941045d2e9b84c928de4
1495356d692ca91daa41f49d7464bef976c5b6858b7a
7f44965dd9f7dde80bebf4aed59cce2a2ca2b223aed122102b63b8203f0
5249767712175200901db1c70d836171df2fd05afeb
016e42f3a2953ae\”}] [\”BUYERS_PRIVATE_KEY_GOES_HERE\”]
Buyers Private Key: (Your key – as the buyer – to the Bitcoin Deposit Address)
Transaction Text provided to you by the Seller:
Result (Paste this into your DOS command box or send it to the Seller):
or
Result (Paste this into your Bitcoin-QT GUI Debug box or send it to the Seller):
Stage 5. Generate *BUYER OR SELLER RAWTX* DOS bitcoind.exe compatible or Bitcoin-QT GUI Debug compatible sendrawtransaction command
Paste the result of running the signrawtransaction text from Step 4 above in Bitcoin-QT, into the box below to generate the command to tell the Bitcoin Network to move the Bitcoins from the Bitcoin Deposit Address. You should see the words complete: true in the text you paste in.
Signed Transaction Text provided by the Buyer:
Result (Paste this into your DOS command box):
or
Result (Paste this into your Bitcoin-QT GUI Debug box):
Enjoy and improve.
– MoonSh00t
You might also like
Post-Auction Bitcoin Price Analysis
Old Cannbis road Seized, FBI raided a home in West Haven
Six Arrested In Austrian Vendor Bust
8 comments
axa
February 10, 2014 at 1:40 am
TMP has good ideas, but flaw is using I2P instead of Tor IMO. As the guide shows I2P is more complicated than Tor to use and I suspect TMP will not succeed because average user who will use Tor will not use I2P.
Reply
admin
February 10, 2014 at 7:37 am In reply to axa.
they have a TOR gateway so its not a problem, the “complicated” part is the payment process that requires some learning.
Reply
JustMe
February 17, 2014 at 6:08 am In reply to admin.
It does seem complicated but so did starting to use tails for Tor but now I can update and configure it automatically and disable everything without having to search every tab. I think it wouldn’t take too long to get the hang of.
Reply
heislegend
March 20, 2014 at 7:59 pm
Since peole want stuff, they will be def. gladly learn new stuff… so i dont think this will bump this concept ;)! Thanks for the quick tuto… even my gf got it now :D!
Reply
ThisTut IsOutadted
May 1, 2014 at 7:31 am
This tutorial seems outdated. In version 1.0 of tails there is no tailsdata folder in media. In electum 1.9.8 there is no electrum.desktop file. Can somebody update this please?
Reply
tocsin
June 22, 2015 at 5:17 pm
Hello.
I’m facing some problems.I run the tails with the VirtualBox on Linux Ubuntu for developers.The i2p starts with no problems but when i try to access the “themarketplace.i2p” an erros comes up,it’s telling me that my router is not yet well-integrated with peers.Keep in mind that i use a wifi network and a cable connection is not possible for me due to used device(ultrabook).Thank you!
Reply
phlibby
June 28, 2015 at 12:52 am
This is the worst stuff I have ever seen! I have been trying to get this to work for A WEEK! And it spits and sputters to a halt every time I think it is going to finally start working. I am so frustrated with this POS GARBAGE. Nevermind. I give. You can keep this stuff. I hate it!!!
Reply
ukl6yf
September 29, 2015 at 9:15 pm
THeres a horrible flaw out there – routing only .i2p addresses through I2P is dangerous. If a darknet site has embeddings from non I2P site you are busted. ALWAYS route EVERYTHING thru the proxy.
Reply
Leave a Reply
Your email address will not be published. Required fields are marked *
Comment
Name *
Email *
Captcha: * 2 × = 12
Visit:
Markets List & Availability Status
Top Markets!
AlphaBay – 98.6%
Dream market – 98.75%
Valhalla (Silkkitie) – 98.06%
Outlaw Market – 98.79%
Hansa Market – 99.59%
Invite / Referral Markets
Acropolis Market – 99.74%
T•chka Free Market – 95.8%
Apple Market – 98.35%
House Of Lions – 97.29%
The Trade Route – 99.65%
Markets
Darknet Heroes League – 97.66%
Wall Street Market – 99.65%
Zion Market – 99.91%
The Majestic Garden – 96.59%
Bloomsfield – 90.83%
Crypto Market – 54.18%
Silk Road 3 – 88.21%
Minerva Market – 99.89%
RsClub Market – 98.37%
PekarMarket (Russian) – 99.97%
The Open Road – 99.98%
Vendor Shops
Megapack – 95.27%
Gammagoblin – 97.89%
The French Connection – 98.42%
CharlieUK – 94.12%
ToYouTeam – 94.1%
EuroPills – 99.01%
Fight Club – 97.68%
Darkmarket – 77.07%
MaghrebHashish – 92.16%
Mollyworld – 93.76%
ElHerbolario – 98.19%
l33TER – 94.39%
YourDrug – 99.08%
The Church (JoR) – 98.08%
RechardSport – 89.64%
Dutch Magic – 97.41%
Soulkush – 95.26%
MeGrimlock – 95.22%
Stoned100 – 92.82%
CosmicBites – 95.83%
G00D00’s Shop – 99.41%
Discussion Forums (Independent)
Darknet Avengers – 94.39%
The HUB – 46.09%
OnionLand – 99.66%
Non-English
Ramp (Russian) – 97.15%
RuTor (Russian) – 99.15%
Russian Silk Road (Russian) – 98.56%
IDC (Italian) – 91.89%
WayAway (Russian) – 99.27%
French Freedom Zone – 94.88%
French Deep Web – 97.97%
HYDRA (Russian) – 99.21%
Check Out
Subscribe To RSS Feed
7,051 Followers
2,566 Fans
Subscribe For new Posts Notifications:
Must Read
Updated List of Dark Net Markets
Click Here To Buy Bitcoins With Paypal!
Dark Net Markets Comparison Chart
Best VPN service Comparison Chart
How To Buy Drugs Online?
Jolly Roger’s Security Guide for Beginners
MultiSig Guides
Security Tutorials
How to access I2P Sites
PGP Tutorial For Newbs (GPA – Gpg4Win)
PGP Tutorial For Newbs (Kleopatra – Gpg4Win)
PGP Tutorial For Newbs Gpg4usb
Basic Guide to PGP On Linux
PGP Tutorial for OSX
How to access .onion sites?
DeepDotWeb’s Darknet Dictionary
Categories
Articles
Featured
Memes & Funny
News
News Updates
Videos
Popular
Recent
Comments
Tags
While Markets Get Seized: Pedophiles Launch a Crowdfunding Site
November 9, 2014
Is your VPN Legit or Shit?
July 8, 2014
Updated: List of Dark Net Markets (Tor & I2P)
October 28, 2013
PGP Tutorial For Newbs (Gpg4Win)
November 11, 2013
Poll: Should We Publish An Interview With A Pedo Site Owner?
April 2, 2014
@Follow Me
French Students Arrested For the Sale Of More Than 10,000 Ecstasy Pills – https://t.co/Arim04kGhJ #darkweb #privacy… https://t.co/srhg8pTdvL
“Asia Food” Narcotics Ring Busted In Germany – https://t.co/7OlFm8Ui4M #darkweb #privacy #deepdotweb https://t.co/D9ZBhnFt25
Deutsche Telekom Responds To The Arrest Of Hacker – https://t.co/P29ZhzN3Xr #darkweb #privacy #deepdotweb https://t.co/e2BmT38azy
German Couple Sentenced For Fraud And Drug Possession – https://t.co/f8mNDHWfRL #darkweb #privacy #deepdotweb https://t.co/gYgYlwdkUe
Fourth PlayPen Moderator Gets 20-Year Sentence For Promoting Child Porn – https://t.co/Vv188S8kBl #darkweb #privacy… https://t.co/rjJPvXnZrJ
Markets List & Availability Status
Top Markets!
AlphaBay – 98.6%
Dream market – 98.75%
Valhalla (Silkkitie) – 98.06%
Outlaw Market – 98.79%
Hansa Market – 99.59%
Invite / Referral Markets
Acropolis Market – 99.74%
T•chka Free Market – 95.8%
Apple Market – 98.35%
House Of Lions – 97.29%
The Trade Route – 99.65%
Markets
Darknet Heroes League – 97.66%
Wall Street Market – 99.65%
Zion Market – 99.91%
The Majestic Garden – 96.59%
Bloomsfield – 90.83%
Crypto Market – 54.18%
Silk Road 3 – 88.21%
Minerva Market – 99.89%
RsClub Market – 98.37%
PekarMarket (Russian) – 99.97%
The Open Road – 99.98%
Vendor Shops
Megapack – 95.27%
Gammagoblin – 97.89%
The French Connection – 98.42%
CharlieUK – 94.12%
ToYouTeam – 94.1%
EuroPills – 99.01%
Fight Club – 97.68%
Darkmarket – 77.07%
MaghrebHashish – 92.16%
Mollyworld – 93.76%
ElHerbolario – 98.19%
l33TER – 94.39%
YourDrug – 99.08%
The Church (JoR) – 98.08%
RechardSport – 89.64%
Dutch Magic – 97.41%
Soulkush – 95.26%
MeGrimlock – 95.22%
Stoned100 – 92.82%
CosmicBites – 95.83%
G00D00’s Shop – 99.41%
Discussion Forums (Independent)
Darknet Avengers – 94.39%
The HUB – 46.09%
OnionLand – 99.66%
Non-English
Ramp (Russian) – 97.15%
RuTor (Russian) – 99.15%
Russian Silk Road (Russian) – 98.56%
IDC (Italian) – 91.89%
WayAway (Russian) – 99.27%
French Freedom Zone – 94.88%
French Deep Web – 97.97%
HYDRA (Russian) – 99.21%
Popular Posts
While Markets Get Seized: Pedophiles Launch a Crowdfunding Site
November 9, 2014
Is your VPN Legit or Shit?
July 8, 2014
Updated: List of Dark Net Markets (Tor & I2P)
October 28, 2013
PGP Tutorial For Newbs (Gpg4Win)
November 11, 2013
Poll: Should We Publish An Interview With A Pedo Site Owner?
April 2, 2014
Random Posts
Windows 10 is not Free – Privacy IssuesFebruary 2, 2017
Pirna Couple Sentenced For FraudNovember 21, 2016
Report Says Dutch Lead Online Drug Sales In The WestAugust 30, 2016
Bitcoin news round-up 07.07.2014July 7, 2014
Don’t Put All Your Eggs In One Cloud BasketFebruary 8, 2015
Latest Posts
French Students Arrested For the Sale Of More Than 10,000 Ecstasy Pills
March 12, 2017
“Asia Food” Narcotics Ring Busted In Germany
March 11, 2017
Deutsche Telekom Responds To The Arrest Of Hacker
March 11, 2017
German Couple Sentenced For Fraud And Drug Possession
March 11, 2017
Fourth PlayPen Moderator Gets 20-Year Sentence For Promoting Child Porn
March 11, 2017
https://api.virwox.com/api/media/web_calc.php?r=1a5251&width=180 </p>
buying bitcoins with paypal and credit cards via Virox SLL.
Buy Bitcoins With Paypal & Credit Cards!
scroll down to see step by stepVirox account setup !
Paypal and Bitcoin Streamline the Online Purchasing Process
Paypal is one of the most trusted and popular services for online transactions these days. Paypal is everywhere now, as many merchants and traders have adopted it with open arms.
Bitcoin is another method of conducting online transactions, which has carved out its own place in the market. Bitcoin is a decentralized, digital currency, with a fixed supply, that reduces the need for using physical or hard money.
On one hand, Paypal makes online, fiat transactions fast and easy. On the other hand, Bitcoin is both a currency and payment system that operates independently of the fiat monetary system, thereby making online purchases more like an equivalent of cash purchases in the real world—whereas Paypal is merely an intermediary between the Internet and a Physical bank.
The speed, security, and convenience of Bitcoin has of course created an ever-increasing demand for the digital currency. As a result, online Bitcoin exchanges—a popular avenue for buying and selling bitcoins—have popped up in droves.
However, one may ask the question: can I buy bitcoins using Paypal, so I do not have to directly link my bank account to a Bitcoin exchange? Yes, here’s how:
Successfully Buying Bitcoins With Paypal
Many people who have used Bitcoin and Paypal say that using Paypal to buy Bitcoin is a very difficult process. If we take a glance at the previous track record of buying Bitcoin via Paypal, we will see that people have indeed faced many inconveniences with Paypal. These difficulties arise due to recurring situations where a person uses Paypal to buy Bitcoin, and then initiates a chargeback, in which the person claims to never have received the bitcoins, and demands a refund from the Bitcoin seller. It is said that Paypal often favors fraudulent merchants, so most Bitcoin traders expect this system to be dangerous with a high chance of having their money stolen, and may opt to refrain from purchasing bitcoins through Paypal.
It is possible to successfully use paypal to buy bitcoins, though, and sell them for a higher prices through online marketplaces, such as LocalBitcoins and eBay. There are two methods that will allow one to buy bitcoins with Paypal: Virwox or credit cards. Virwox charges a commission fee for using its services, but it is, by far, easier to buy bitcoins through Paypal with Virox than by using a credit card. Therefore, we will show you how to use Virwox to successfully buy bitcoins through Paypal.
How to Buy Bitcoins With Paypal by Using Virwox
We have Created a tutorial to explain the Virwox method—here is a general overview of the steps you will have to take to use this process:
– Visit the website Virwox.com
– Register for an account on that website.
– Then, add funds to your Virwox account via Paypal
– Buy Linden$ (SLL) with USD/EUR
– Buy bitcoins with your linden$ (SLL)
– At least send your Bitcoin to your wallet.
*Note: Linden$ is the virtual currency used in the online game, “Second Life”
Step 1: Visit the official website of Virwox and register for an account. You need to ignore the message, “your avatar connection has not been validated yet.”
Step 2: Click on the “Deposit” button on the sidebar:
 Step 3: Choose how you want to deposit your money—you can use Paypal or Credit cards using Skrill payment. Note that you can only deposit limited amounts of money every 24 hours. Your 24 hour deposit limit will be raised as you complete successful transactions. A failed transaction will still be deducted from your daily limit, so be careful with the details enter while preparing your Paypal or credit card payments.
Step 3: Choose how you want to deposit your money—you can use Paypal or Credit cards using Skrill payment. Note that you can only deposit limited amounts of money every 24 hours. Your 24 hour deposit limit will be raised as you complete successful transactions. A failed transaction will still be deducted from your daily limit, so be careful with the details enter while preparing your Paypal or credit card payments.
 Step 4: Once you finish your deposit, you need to convert the USD or EUR to SLL. Just click the “place a sell order” button or click the USD/SLL button on the sidebar:
Step 4: Once you finish your deposit, you need to convert the USD or EUR to SLL. Just click the “place a sell order” button or click the USD/SLL button on the sidebar:
 step 5: Choose how much USD you want to convert to SLL and click “Next.”
step 5: Choose how much USD you want to convert to SLL and click “Next.”

 Step 6: After Clicking “Next,” you need to confirm your order.
Step 6: After Clicking “Next,” you need to confirm your order.
Step 7: After you have converted your USD to SLL, all that is left to do is to convert the SLL to BTC. To do this, Just click on the “BTC/SLL” button on the sidebar.
6-convert-to-BTC
 Step 8: On the next screen, enter the mount of bitcoins you want to buy using your SLL.
Step 8: On the next screen, enter the mount of bitcoins you want to buy using your SLL.

 Step 9: After your transaction has been confirmed, you will be able to withdraw your bitcoins and send them to your wallet; click the “Withdraw” button on the sidebar.
Step 9: After your transaction has been confirmed, you will be able to withdraw your bitcoins and send them to your wallet; click the “Withdraw” button on the sidebar.
step 10: Enter the amount of bitcoins you want to Withdraw, then enter your Bitcoin address and click the “Request Withdraw” button. Note: on your first time there, may be a 48 hour delay until your bitcoins are sent to your wallet. This delay is placed to help prevent fraud. After your first transaction, though, the withdrawal will be instant, and it can be traced in the Blockchain.
In conclusion, this method is the easiest way to buy bitcoins using paypal and credit cards; the only disadvantages are the fees (Papal fees, Lower rates for BTC & SLL).
Rise RESIT Love
Welcome,
this blog site is built to inform the children of God , there is a way to resist the comforts of the enemy’s ways……..CLICK ON ANY ONE OF OUR FEATURED LINKS TO VIEW A PAGE OR POST !!
Protected: Codes for sharing ! private page psswrd needed !
Inspired by GOOD DEEDS ! stories of true heroes !
Virox- money laundering or Virtual currency exchange BREAKTHROUGH?!?!?
Homeschooling? Why are these children, So much more advanced than the public school kids?
So you don’t think NAZI’s are evil?
Bible Prophecy: ” was I left behind ?”
Simple Windows 7 Password hack for dummies! STEP BY STEP!
WORLD NEWS IN REAL TIME ! no mainstream lies, here!!
MORE POSTS AND PAGES FROM RESIST RISE LOVE IN LEFT SIDE BAR SEARCH BOX !
Virox- money laundering or Virtual currency exchange BREAKTHROUGH?!?!?
At VirWoX, we take security and privacy seriously. The service is designed, developed, and operated by Virtual World Services GmbH, a real-world company founded in Austria specifically for the purpose of conducting business in virtual worlds and running services like VirWoX. You can find contact details here.
While it is part of our security policy not to reveal too many details about it, we would like to share some important aspects with you. Please also consult the section on Terminals for additional security information related to our terminals.
Protection of Passwords
The single most important thing you need to remember is to choose a strong password and keep it secure. Good passwords are:
At least 8 characters long
A combination of characters (uppercase and lowercase) and numbers that is hard to guess.
Different from other passwords. In particular, you should not use your SL password for VirWoX also. This ensures that even if someone is able to steal you SL account, they cannot access your VirWoX money.
Not written down. Should you forget your password, you can have it reset and a new password sent to your email address. It is therefore important that you use your real email address and keep it current. Note that we also do not store your password in clear text, so we cannot tell you what it is either.
Privacy
We need some personal information (such as your Name) in order to transfer real-world money to bank accounts. Also, we receive similar personal information when you transfer money using PayPal or Skrill (no bank account or credit card numbers). We will take all reasonable efforts to keep this personal information safe, and will not sell or give such information to third parties, except if requested by public authorities. This does not apply to anonymous data for statistical purposes. We do not store any credit card information.
Terminals
We operate a network of terminals in the Second Life virtual world. The Terminal Locations page contains an up-to-date list of them. You need them for validation of your account.
Validation
When you validate your account, you create a permanent link between your SL avatar and your VirWoX account. This is necessary for an effective and secure transfer of Linden dollars between your Second Life account and your VirWoX account. The process is fairly simple: After you have entered your SL first and last name on the VirWoX registration form, and after you have logged in to VirWoX for the first time using the temporary password sent to you by email, log in to the Second Life world, go to a VirWoX Terminal and simply touch it. If the terminal is a genuine VirWoX terminal, it will pop up a dialog telling you the VirWoX username you have chosen in VirWoX for this avatar. Once you confirm this is indeed your username, the link is made, and you are all set.
Important: If the terminal is not able to tell the correct username, it is probably not a real VirWoX terminal and you should not proceed!
How do you find a terminal?
On the Terminal Locations page, we maintain a list of currently available VirWoX terminals.
How can you tell it is a real VirWoX Terminal?
Have you ever wondered, why in the real world you have to prove your identity to an ATM (using your PIN), but the ATM never proves to you that it’s a real ATM? In the Second Life world, this problem is even bigger because it is easy to build something that looks like a VirWoX terminal. Consequently, our terminals prove to you that they are real VirWoX terminals by greeting you with your VirWoX username plus your personal, secret TIN (Terminal Identification Number), that you can choose freely (and change it as often as you like) on the Settings page. Therefore, before you select "Pay" to pay something that looks like a VirWoX terminal, always touch it and check your username and TIN!
Fees
Exchange Commissions and Discounts
Market Order:
A small commission will be charged for the service of matching and executing your order against others. The commmission for market orders consists of a fixed fee plus a variable percentage, according to the following table:
Currency Fixed Variable
EUR/SLL 50 SLL 2.90%
USD/SLL 50 SLL 3.90%
GBP/SLL 50 SLL 3.90%
CHF/SLL 50 SLL 3.90%
EUR/ACD 50 ACD 3.90%
USD/ACD 50 ACD 3.90%
SLL/ACD 25 ACD 3.90%
SLL/OMC 25 OMC 1.90%
EUR/OMC 50 OMC 2.90%
USD/OMC 50 OMC 1.90%
BTC/SLL 50 SLL 3.90%
EUR/MVC 50 MVC 2.90%
No discounts are applied for market orders, but the commission paid counts towards discounts for limit orders (see below).
Limit Order:
The commission will only be charged if your order is actually executed. If executed partially, commission will only by paid on the part that has been executed. The base commission rate for all currently exchanged currencies is 3.9%. However, the more you exchange, the less you pay: The effective commission rate is determined by the base commission rate and your current discount on commission. The discount in turn is based on your trading activity (more precisely, the amount of SLL commission already paid) in the previous 30 days, according to the following table:
Commission paid
(last 30 days) Discount Effective
Commission
0 SLL 0% 3.90%
1,000 SLL 10% 3.51%
2,000 SLL 20% 3.12%
5,000 SLL 30% 2.73%
10,000 SLL 40% 2.34%
20,000 SLL 50% 1.95%
50,000 SLL 60% 1.56%
100,000 SLL 70% 1.17%
200,000 SLL 80% 0.78%
Please note that the discount rate applied to a specific order is the one that was in effect at the time when you have entered the order. If your discount rate changes after that time to your favour, you may of course cancel the order and re-enter it to take advantage of the higher discount level. Your current commission paid in the last 30 days and discount levels are displayed on the Account Overview page.
Deposits
PayPal: Unfortunately, PayPal charges us fees for its services, which are deducted from your deposit. Also, the fee varies with currency, location of customer, payment method used, transaction size, and the size of our previous transactions with PayPal; so the exact fee is only known to us after the transaction has taken place. As an example, the current fee for deposits in Euro for customers with their PayPal account kept in Euro is 0.35 Euro plus 3.4% of the transaction.
Credit/Debit Cards, Skrill (Moneybookers): Similar to PayPal, Skrill charges us fees for its services, which are deducted from your deposit. The current fee for deposits in Euro for customers with their Skrill account kept in Euro is 0.39 Euro plus 3.5% of the transaction.
paysafecard: The fee for paysafecard deposits is 20%.
SOFORTbanking: For this service, SOFORT AG charges us a fee of 2.5% of the transaction value, with a minimum of 0.25 Euro (if the transaction value is below 10 Euros), which will be deducted from your deposit.
Other Deposits: Other deposits (i.e. deposits of MVC from My Virtual Community) are free.
Withdrawals
A handling fee of 0.003 BTC per bitcoin withdrawal will be charged.
A handling fee of 1 EUR (1 USD, 1 CHF, 1 GBP) + 2% PayPal Fee per PayPal withdrawal will be charged.
A handling fee of 1 EUR (1 USD, 1 CHF, 1 GBP) per withdrawal will be charged for all other types of withdrawals (Skrill, Bank Transfers).
Send virtual currency to other user
Sending virtual currency (SLL, ACD, or OMC) is free of charge.
Inactivity Fee
There is no fee just for maintaning your VirWoX account. However, if you have not used your VirWoX account for more than 12 months, we will charge an inactivity fee of 2 EUR (or the equivalent in other currency) per month, but only if there is a positive balance on the account.
</pre>
OUR REFERRAL LINK FOR VIROX ! https://www.virwox.com?r=1a5251

How to Exchange
Before you can place any orders, you will have to open an account, and fund it with the currency you want to exchange.
Speed vs. Rate
There are two main ways of using VirWoX:
- You want your order executed immediately: In this case, you would simply accept the current best available rate, and place a “market order”.
- You are willing to wait for an even better rate: In this case, you place a “limit order” and specify your desired rate. Of course, your order will only get executed if and when somebody is willing to accept your offer.
How does it work?
Say, you have 100 Euros in your VirWoX account and want to get Linden dollars for it. You check the current market and see that the rate is near 400 (Linden dollars per Euro). So you decide you want to sell your Euros for not less than 400 Linden dollars per Euro. Commissions aside, this would give you 40,000 Linden dollars if executed.
You go to the Exchange EUR/SLL page (EUR is the currency symbol for Euros, SLL for “Second Life Lindens”) and enter an order to sell 100 EUR at a rate of 400 SLL per EUR. Of course, you can also do the opposite and buy Euros (=selling Linden dollars) by entering a “buy” order.
Once you have entered you order, it will be processed by our fully automatic order matching system. If and when there is an opposite order for the same rate, your order may get matched with it. Note that your order may be matched with more than one other order, i.e. there can also be partial executions. Until the order is fully executed, you have the option of cancelling (the remaining part of) it.
After you have exchanged your money to some other currency, you can request a withdrawal of that currency using the ‘Withdraw’ page. In case of a withdrawal of SLL to your SL acccount, this will be completed in a few seconds. Withdrawals to PayPal, Skrill, or bank account sometimes require a manual intervention and therefore may take a bit longer in this case.
Security and Privacy
At VirWoX, we take security and privacy seriously. The service is designed, developed, and operated by Virtual World Services GmbH, a real-world company founded in Austria specifically for the purpose of conducting business in virtual worlds and running services like VirWoX. You can find contact details here.
While it is part of our security policy not to reveal too many details about it, we would like to share some important aspects with you. Please also consult the section on Terminals for additional security information related to our terminals.
Protection of Passwords
The single most important thing you need to remember is to choose a strong password and keep it secure. Good passwords are:
At least 8 characters long
A combination of characters (uppercase and lowercase) and numbers that is hard to guess.
Different from other passwords. In particular, you should not use your SL password for VirWoX also. This ensures that even if someone is able to steal you SL account, they cannot access your VirWoX money.
Not written down. Should you forget your password, you can have it reset and a new password sent to your email address. It is therefore important that you use your real email address and keep it current. Note that we also do not store your password in clear text, so we cannot tell you what it is either.
Privacy
We need some personal information (such as your Name) in order to transfer real-world money to bank accounts. Also, we receive similar personal information when you transfer money using PayPal or Skrill (no bank account or credit card numbers). We will take all reasonable efforts to keep this personal information safe, and will not sell or give such information to third parties, except if requested by public authorities. This does not apply to anonymous data for statistical purposes. We do not store any credit card information.
Terminals
We operate a network of terminals in the Second Life virtual world. The Terminal Locations page contains an up-to-date list of them. You need them for validation of your account.
Validation
When you validate your account, you create a permanent link between your SL avatar and your VirWoX account. This is necessary for an effective and secure transfer of Linden dollars between your Second Life account and your VirWoX account. The process is fairly simple: After you have entered your SL first and last name on the VirWoX registration form, and after you have logged in to VirWoX for the first time using the temporary password sent to you by email, log in to the Second Life world, go to a VirWoX Terminal and simply touch it. If the terminal is a genuine VirWoX terminal, it will pop up a dialog telling you the VirWoX username you have chosen in VirWoX for this avatar. Once you confirm this is indeed your username, the link is made, and you are all set.
Important: If the terminal is not able to tell the correct username, it is probably not a real VirWoX terminal and you should not proceed!
How do you find a terminal?
On the Terminal Locations page, we maintain a list of currently available VirWoX terminals.
How can you tell it is a real VirWoX Terminal?
Have you ever wondered, why in the real world you have to prove your identity to an ATM (using your PIN), but the ATM never proves to you that it's a real ATM? In the Second Life world, this problem is even bigger because it is easy to build something that looks like a VirWoX terminal. Consequently, our terminals prove to you that they are real VirWoX terminals by greeting you with your VirWoX username plus your personal, secret TIN (Terminal Identification Number), that you can choose freely (and change it as often as you like) on the Settings page. Therefore, before you select "Pay" to pay something that looks like a VirWoX terminal, always touch it and check your username and TIN!
Fees
Exchange Commissions and Discounts
Market Order:
A small commission will be charged for the service of matching and executing your order against others. The commmission for market orders consists of a fixed fee plus a variable percentage, according to the following table:
Currency Fixed Variable
EUR/SLL 50 SLL 2.90%
USD/SLL 50 SLL 3.90%
GBP/SLL 50 SLL 3.90%
CHF/SLL 50 SLL 3.90%
EUR/ACD 50 ACD 3.90%
USD/ACD 50 ACD 3.90%
SLL/ACD 25 ACD 3.90%
SLL/OMC 25 OMC 1.90%
EUR/OMC 50 OMC 2.90%
USD/OMC 50 OMC 1.90%
BTC/SLL 50 SLL 3.90%
EUR/MVC 50 MVC 2.90%
No discounts are applied for market orders, but the commission paid counts towards discounts for limit orders (see below).
Limit Order:
The commission will only be charged if your order is actually executed. If executed partially, commission will only by paid on the part that has been executed. The base commission rate for all currently exchanged currencies is 3.9%. However, the more you exchange, the less you pay: The effective commission rate is determined by the base commission rate and your current discount on commission. The discount in turn is based on your trading activity (more precisely, the amount of SLL commission already paid) in the previous 30 days, according to the following table:
Commission paid
(last 30 days) Discount Effective
Commission
0 SLL 0% 3.90%
1,000 SLL 10% 3.51%
2,000 SLL 20% 3.12%
5,000 SLL 30% 2.73%
10,000 SLL 40% 2.34%
20,000 SLL 50% 1.95%
50,000 SLL 60% 1.56%
100,000 SLL 70% 1.17%
200,000 SLL 80% 0.78%
Please note that the discount rate applied to a specific order is the one that was in effect at the time when you have entered the order. If your discount rate changes after that time to your favour, you may of course cancel the order and re-enter it to take advantage of the higher discount level. Your current commission paid in the last 30 days and discount levels are displayed on the Account Overview page.
Deposits
PayPal: Unfortunately, PayPal charges us fees for its services, which are deducted from your deposit. Also, the fee varies with currency, location of customer, payment method used, transaction size, and the size of our previous transactions with PayPal; so the exact fee is only known to us after the transaction has taken place. As an example, the current fee for deposits in Euro for customers with their PayPal account kept in Euro is 0.35 Euro plus 3.4% of the transaction.
Credit/Debit Cards, Skrill (Moneybookers): Similar to PayPal, Skrill charges us fees for its services, which are deducted from your deposit. The current fee for deposits in Euro for customers with their Skrill account kept in Euro is 0.39 Euro plus 3.5% of the transaction.
paysafecard: The fee for paysafecard deposits is 20%.
SOFORTbanking: For this service, SOFORT AG charges us a fee of 2.5% of the transaction value, with a minimum of 0.25 Euro (if the transaction value is below 10 Euros), which will be deducted from your deposit.
Other Deposits: Other deposits (i.e. deposits of MVC from My Virtual Community) are free.
Withdrawals
A handling fee of 0.003 BTC per bitcoin withdrawal will be charged.
A handling fee of 1 EUR (1 USD, 1 CHF, 1 GBP) + 2% PayPal Fee per PayPal withdrawal will be charged.
A handling fee of 1 EUR (1 USD, 1 CHF, 1 GBP) per withdrawal will be charged for all other types of withdrawals (Skrill, Bank Transfers).
Send virtual currency to other user
Sending virtual currency (SLL, ACD, or OMC) is free of charge.
Inactivity Fee
There is no fee just for maintaning your VirWoX account. However, if you have not used your VirWoX account for more than 12 months, we will charge an inactivity fee of 2 EUR (or the equivalent in other currency) per month, but only if there is a positive balance on the account.
So you don’t think NAZI’s are evil?
Inhuman Experiments of the German Hitler SS Doctors
Donnerstag, 25. Februar 2016
Occultism of Hitlers 3th.Reich
Occultism of Hitlers 3th.Reich
Adolf Hitler was obsessed with the occult, in his case the Thule Society, closely inter-connected with German Theosophists. The jolly roger, skull and cross bones, “der Totenkopf” was an emblem worn by Hitler’s SS soldiers and was emblazoned on SS armoured cars and tanks (see images on this page). The SS was a religious cult of sworn Hitler/German ancestor worship with bloody Rituals also on living Childs and Babys.
If the Nazis’ occult lodges had been exposed then shut down, not treated as a taboo, millions of lives could have been saved. A small price to pay for insane racism and the blood of millions of Parents,kids and babys. The second world war need never have happened. Unless you want the occult fuelling a totalitarian West’s Third World War ‘on…
View original post 14,787 more words
secret marketing strategy ! freee!
Terrific Strategies To Apply A Social media Marketing Approach
Social networking happens to be the driving power of the Net. The ability for end users of various web pages to share developed content has manufactured it probable for facts to be spread quicker than any individual could have probably imagined. If you would want to promote by way of social networking, then examine the following short article for suggestions on suitable social media marketing internet marketing.
Generally continue to be beneficial when marketing via social websites. Folks choose to be about other folks and things that make them sense great. Lousy mouthing other folks or generating adverse statements may lead to many others viewing your products or services negatively. Make sure you keep this in mind on your personalized web site likewise when you have a person.
Use Fb to acquire some extremely affordable advertising prospects. Produce a professional business enterprise account or produce a company fan website page. Choose a while to seem up your opponents on Facebook to view just how much of the presence they have got, and the things they did to get that. Tend not to duplicate what they did, but use their website page being an example for exactly what is performing or exactly what is not.
Sorting alternatives, as well as a ranking and feedback system will add a completely new stage of interactivity and charm to the website. If you increase these things, your buyers can obtain articles they’re seeking for, which can retain them all over.
To receive the absolute best buyers from your social networking marketing and advertising, maintain your content coming on a regular basis and with consistency. Each time a buyer sees you submit on Fb each and every other day, it really is sufficient they try to remember you easily, although not a great deal they get aggravated with you exhibiting up too considerably. When it arrives time for them to invest cash on anything you could possibly supply, they’ll choose you since your manufacturer looks like a trusted buddy.
Tend not to submit irrelevant and trivial posts on your social networking profiles. Constantly keep your posts experienced and pertinent. Nobody cares you got a fresh cell cell phone, or that you’re standing in line for the flicks. These trivial posts really should be reserved on your very own particular profile, not your enterprise profile.

When using social media internet marketing, it’s possible you’ll have to modify and refresh your aim and plans routinely, so you can continue to be on the right track. The conversations may perhaps get your marketing and advertising down unanticipated paths, so it is advisable to re-evaluate the direction it’s happening a daily basis and adjust appropriately.
Constantly remember who your viewers is within your social media marketing strategies and what matters probably the most to them. You have to post material that is certainly relevant to them and emphasis your initiatives in ways that maintain their consideration. Your posts needs to be appropriate and of top quality that your followers and followers tend not to just skip them about for the reason that they are not intrigued.
As mentioned prior to, as a consequence of the flexibility for consumers to share articles, social networking has grown to be a serious World wide web driving pressure. The power to share content makes social websites a feasible promotion platform. Make some place with your plan to apply the recommendation from this post, therefore you can distribute your message significantly and extensive..
love you all, and their isn’t shit you can do about it !—->mjl [click to like]
the MATRIX and the BIBLE AND ONION sites….
The Matrix
Contents
1 What is the Matrix
2 Resisting the Matrix
3 Subverting the Matrix
3.1 Gift Culture
3.2 Information Anarchy
3.3 The Anonymous Internet Economy
4 Freedom Seekers are Not Terrorists
5 Spreading the Word
6 Target Audience
6.1 Civil Libertarians
6.2 Whistleblowers
6.3 Bloggers and Independent Journalists
6.4 “Political Dissidents” and Inquisitive Minds
6.5 People with Enemies
6.6 Programmers and Security Researchers
6.7 The Video Game Underground
6.8 Moonlighters, Double-Shifters, and Consultants
6.9 Potential Victims of Identity Theft (Everyone)
6.10 Entrepreneurs
What is the Matrix
In my opinion, The Matrix films provide the best metaphor our society has for understanding why organized evil and oppression are allowed to exist, and so I will use it for this purpose. While my interpretation isn’t the only possible one, I believe it to be valid, comprehensive, and most importantly, illustrative of the message I am trying to convey.
So let’s begin by discussing what the Matrix is not. The Matrix is not the physical world. As far as I’m concerned, the physical world is actually real and is in fact governed ceaselessly by the laws of physics. Conversely, the Matrix is also not the Internet, despite what many seem to believe. The Matrix spans and transcends both these worlds. It has existed since the dawn of civilization, and it will continue to exist until its collapse.
September 11, 2001 will go down in the history books as a day of infamy, when murderous terrorists made a sudden attack on the USA, killing in excess of 6000 people (recent numbers indicate ~4000 total for 9-11 including D.C. and in Pennsylvania). That’s more than twice as many people as those who died when Pearl Harbor was attacked on December 7, 1941. The picture below is of Manhattan and the World Trade Center before September 11, 2001. The twin towers were both 110 stories tall.

The targets of the terrorists were not military targets; their aim was to murder as many unarmed and defenseless civilians as possible. They hijacked 4 airplanes with groups of 3-5 on each airplane including a trained pilot. Two hijacked airliners going from Boston to LA were flown into the two World Trade Center towers in New York City, using the airplanes as a form of missile. These were suicide flights by deranged muslims, who not only wanted to kill themselves, but all the people on each flight. It may only be a coincidence that Boston to LA (B-LA) seems to be the initials of Bin Laden, the head of the Al Quaida coalition of terrorist groups run from Kanda
So then, what is it? Well, that’s complicated. Much like in the movie, it’s nearly impossible to convey the size and scope of the Matrix to someone who doesn’t already see it for what it is. However, unlike the movie, I believe it is an ethical imperative to try to convey it in a literal sense, even to those who are so dependent upon the Matrix that they would fight to protect it. At worst, they won’t understand or believe and will continue on about their business. In a sense, I believe Cypher was right to resent Morpheus for what he did, because Morpheus is the social structure that subordinates Humanity to its will. It is the machinery of society that exists solely to perpetuate itself, its influence, and its power independent of any human need. It insulates us from each other and ourselves through deception, and essentially transforms us into servile engines of economic and political output (power). The machines that live off this power are institutions: large corporations, governments, schools, religious institutions, and even non-profit orgs. Every institution will reach a point in its existence where its primary function becomes self-preservation and perpetuation, instead of serving human need. At this point it becomes a machine of the Matrix. For example, when they become machines, governments cease to serve people and instead seek to extend their power over them; corporations prioritize increasing shareholder value over producing quality products or otherwise serving the public good; schools view students as a means and not an end; religious organizations equate membership with salvation (and actively oppose other teachings and even independent practice); and non-profits and charities spend more budget on fund raising activity than on their original focus. Inevitably all large institutions eventually become machines. They become too big for Humanity.
In addition to the independent self-perpetuating machines that write most of our paychecks, the Matrix has several major cooperative and more actively sinister groups of machines subsisting off of its power and directly contributing to the structure of the Matrix itself. These groups are the Military Industrial Complex, the Political Industrial Complex, the Prison Industrial Complex, the Surveillance Industrial Complex, the Media Industrial Complex, the Academic Industrial Complex, the Agricultural Industrial Complex, the Medical Industrial Complex and the major religious organizations (not to be confused with actual religions, many religious organizatons have abandoned the underlying principles of the religions they claim to represent). All machines in these groups either actively oppress humanity, or enable the oppression to persist. It is through their combined efforts that the Matrix takes on some of its more distasteful qualities.
Do you ever wonder If Aristotle and Plato dedicated their lives to something they don’t really believe or tested? They had a school, a philosopher school. 2300 years ago and still today we have to learn it at the University’s. But why? If the things they said back then where just thought forms without a deeper truth or meaning why do we need to go so far back?
How many opinions are there? Why are the opinions of them so important that was my question.
If you then take Karl Marx his book ‘das capital’, and you see his vision completely clashes with the visions of the ancient philosophers, not just little differences in opinion but a way of thinking I call it a form of dehumanization, all in the name of capital. Without shame.
I wonder how this can be. Because truth can be found in Ancient Philosophy, I believe in the laws concerning property en wealth that Aristotle pointed out very strictly in his works. Why? Because the people he worked with were on to something. You don’t do the things they did if it’s all without meaning. With the invention of money those laws could be altered because the economy was since then not a trade of goods but an economy based on money. Carl Marx was the front-man of a shift. Money going to the digital age. Therefore maybe we should take Marx and add IT with the theory to make it up to date. Marx-IT or Matrix.
He comes with the claim that a worker should earn just enough to stay healthy, so that he can produce each day the same. In other words, the only reason we give you money is to stay working for us. Producing. You can’t earn to much money because then you get lazy, just enough to see you show up each day, with the amount of sleep you need for your energy level to produce as much as possible.
Nice Philosophy he? Full of ethics and deep Human values.
Bentham with his Utilitarianism philosophy comes in to play, maybe we can do again a little game because that’s the trademark of certain organizations. riddles and things hidden in plain sight. Utilitarianism = Illuminatiarism, or how would you yourself name the philosophy based on the Illuminaty? Ok that’s all speculation but look at the death of Aristotle and combine it with the date of death of Bentham, the inventor of Utilitarianism. Then we have 322 and 1832.
Benthams body was preserved, his head was mummified but his body had to exist of bones, so no mummification. His head was missing. Why is that weird and why all these facts?
because if you go to skull and bones you see only 2 dates 322 and 1832, a head and bones. When you study philosphy your book begins with 322 and ends with 1832 or the other way around.
When you put these 2 philosophers together they don’t mean much for each other but when you look deeper, you will see that Utilitarianism combined with Aristotle and Marx + money in the form of a digital current, provides the perfect blend to respect the natural laws of Ancient Philosophers by a form of energy transfer to money.
Money you can give away as a loan, you can invest it, by doing this you don’t have a big capital or any of the things that Ancient Philosophers protested against concerning Natural laws.
I don’t know if having to much wealth/capital has a negative impact on life. But Aristotle was convinced. The question is therefore… Did Marx knew that he could pass the ancient philosophers with what he was writing? Strange thing to point to is the formula Marx used in his book M-C-M and C-M-C, some people say it’s intentionally this formula to point at something else. Personally I think physics. Again something hidden in plain sight in the form of a joke to the initiates. This was a tip someone gave me… And indeed that is the humor of people that know things we don’t. They love it when you see it right in front of you but you have no idea.
|
A third airplane (American Flight 77) took off from Washington DC or Baltimore, was hijacked, and although it first appeared to be headed for the White House, it veered off and struck one side of the Pentagon Building across the Potomac River in Arlington, Virginia. The airplane that hit the Pentagon struck the ground just before the building so the damage, although severe, was less than a direct hit. Perhaps 50 people in the Pentagon outer ring building at that point were killed plus all the people on the aircraft. The satellite picture below shows the demolished burned area of the building, with the outer ring sustaining the damage (there are 5 rings of buildings in the Pentagon). The Pentagon was hit ~9:40 am (EST).  The first airplane to hit in New York City was American Airlines flight 11, which struck the North Tower of the World Trade Center at ~8:45 am (EST). At ~9:03 am (EST), United Airlines flight 175 struck the South Tower. The pictures below show the second airliner just before hitting, and then the explosion. The black building is 7 Trade Tower, an ~50 story building that collapsed too after the two main World Trade Center towers collapsed (the South Tower collapsed ~9:58 am, the North Tower collapsed ~10:28 am, and the 7 Trade Tower building collapsed at ~5:20 pm EST).   I believe the sequence of pictures below shows the North Tower collapsing after the South Tower had already collapsed.
I’ve worked on the Bible code matrix below as a sort of therapy, to work out my anger at the terrorists by channeling it into something positive. The matrix is the most advanced matrix I’ve ever done. I have lots of terms that I have not snooped yet, to see if they are part of a longer phrase or sentence. Most of the short terms I’ve turned off so as not to display them, to create the matrix and matrix report, in order to simplify it. For example, I haven’t even yet looked for the names of individual terrorists. Consider the matrix below a beginning, since I am absolutely positive that there is much more in the matrix. That said, the matrix has many complete sentences and statistical odds that is less than 1 chance in 10 to the 250th power. What Language is in the Bible Code? The Bible code is in Hebrew, period. To further expand that definition, the Hebrew used in the Bible code includes all attested word forms in the Torah and Tanakh, as well as modern Hebrew words. Additionally, I include attested Aramaic as used in the books of Ezra and Daniel. Since the Aramaic part of the Tanakh is a very small part of it, we would assume that proportionally, any use of Aramaic in the Bible codes is proportionally small. A Short Summary: I may add later, my own summary of what is shown in matrix below, but I think that anyone reading the English translations of the terms can draw their own conclusion. One point is necessary to explain. There is another terrorist event predicted in the matrix below for the 10th of Tevet (24/25 December in 2001?). The year term that goes through it is the abbreviated form of year 5762. That abbreviated form can either mean calendar year 2002, or it can mean the jewish year from Rosh Hashanah to the next Rosh Hashanah in the fall of the year. Therefore, the predicted event could either mean December 25 of 2001, or December 15 of 2002. I believe it means December 25 of 2001, because there is also another term I left off the matrix which is an abbreviated year 5761 and is close to the term shown. That points to me that it is more likely December 25 of 2001. However, since one cannot be absolutely sure, it is better to say that it is on December 25 in 2001 or December 15 in 2002. I will work on it to see whether I can dig out more possible details on this possible future event. (don’t e-mail to ask about it, if I get something good, I will put up a new revised version of the matrix). Please read all the terms below and draw your own conclusions. Explanation of Verb Usages: Below the matrix is a table to explain the verbs used in various terms. The reason for this is that different verb types may be spelled the same but pronounced differently. Therefore, because no vowelization marks are shown, I need to show the verb usage I intended in the sentences. I am not perfect and any grammatical errors pointed out will be corrected. |
Matrix Report:

.
World Trade Center codes matrix:

| Statistical Odds Calculation:
The matrix-R-values in the matrix report are calculated in log base 10, by taking account the number of letters and letter distribution in the matrix. To calculate the cumulative R-value for all terms in the matrix, we use the text R-value for the main term, since the matrix pivots on the main term. In this case, the search text was the Torah although the matrix is entirely in Numbers chapter 16 to chapter 32. Then for all other terms, we use the matrix R-value. The calculations are: cumulative matrix R-value = text R-value for main term + the sum of the matrix R-values for all other terms cumulative matrix R-value = 8.416 + 332.02 = 340.436 Translating the number 340.436 to odds we invert log, and we get 1 chance in 2.7289778 x 10 to the 340th power. Let me put that in perspective. There are an estimated 10 to the 80th power individual particles in the universe. If one believes the big bang theory that the earth is 15 billion years old, that is less than 10 to the 25th power in seconds. I want you to understand that the odds of this matrix are extremely huge. Explanation of Hebrew Verbs used in the Terms: …. |
Utilitarianism stands for a society with the most amount of happiness. The goal is thus the most amount of happiness in order to base your decisions and to say whether a decision is ethically and/or morally correct. So when the most amount of happiness is achieved then ethics or morals are respected, it does not matter how many people are involved and how the happiness is divided between the people. Looks great right?
But if 20 people are just ‘OK’ and 1 person is super happy, and this person is so happy that the sum total of happiness is bigger then when all 21 are all just ‘fine’ then this is ethically correct and morally a right thing to do. It’s about SACRIFICE. It is allowed that some people have to sacrifice themselves as long as the total amount of happiness is the biggest. So who are these people who have to sacrifice themselves and how many people are we talking about? Do they know it about themselves?
Can you see that people who are addicted to status, property and extravagance,.. the people who get the feeling that they are better then all the rest, that they own the world, that those people do reach a higher state of happiness compared to people that don’t really care about a lot of property/money and do care about other people instead of own interest? Own interest is by the way the hidden hand from Adam Smith (Hidden or Invisible hand).
But what does Aristotle say about all this? No man can have more then a certain amount of property/possessions/wealth. He is very strict and clear about these rules in his works. So do we have a problem? If the economy was based on exchange of goods there was indeed a problem but Karl Marx and the banking system provide the solution. You take your money and you hand it out as a loan so you actually don’t have a whole lot of capital but each month you get a certain amount that covers your BIG LUXURIOUS EXPENSES.
This way you escape Aristotle and Plato’s advise on how Life works and the Laws of nature on the division of property between the amount of people on earth. This way you escape the possible negative force when having to much, and you use Marx his theory on how to fully exploit your workers for your own advantage, meantime you give those workers loans so you don’t brake the Natural Laws Ancient Philosophers talk about. And above all, these loans even give you more money because of the interest. As if Marx his exploitation of workers isn’t enough. They also have to pay interest on loans. But don’t worry the Utilitarianism way of life solves the problem it’s all fucking ethical and morally tolerable and accepted. (322-1832. Aristotle + Bentham)
And all this is possible because of contracts, without legal agreement this would not exist. No loans, no investments, no labor contracts, … The rule of Law and Order is indeed very important.
If money controls workers and money controls the energy of the workers, then money controls energy. If the stock market is based on money and money controls the workers then who is the stock? A good name right? funny right 😉 Besides the hidden hand has a far more important role to play then generally accepted. But they don’t give us all the information.
This whole text seems like a mockery because it is a mockery. Why? Because that’s the manner they speak to us, amusement because of our lack of knowledge. The second reason is because the person who went back into Plato’s cave was being mocked at. When people who know more then you mock you with riddles you don’t understand, make sure that they think you are a really dumbass, the riddles will become much more easy because they think you’re a stupid f°°K. Keep track of things, connect dots and see where the arrow points. by reading books random on good faith we will not know the truth but can only speculate. There are people who do know. When you meet people who treat you this way, you can become mad or you can play the game. Smart people they mock them with harder riddles. So be a smart man, play a stupid muppet for the masters, deceive them, manipulate them, study psychology, take the information , use the information and let them become the puppets while thinking they are still the masters. Because that’s what they have done and still are doing to us.
And please don’t ride a goat, take the buss.
Resisting the Matrix
Resistance is a mental state. The Matrix is designed to make it easy to accept what it tells you, and to make it hard to filter the Truth from the lies. Resisting the Matrix requires understanding its operating principles and assumptions, rejecting them, and helping others to do the same.

The Matrix is fascist, the Matrix is deceptive, and the Matrix is bureaucracy. The Matrix is essentially the rule of the institution over the individual, and in it, the rights of the individual are subordinate to the rights of the institution. Individuals have to believe (or at least not actively oppose the idea) that large corporations have the right to protect their profits above all else, and thus dictate policy and law. They have to believe that this law is just, moral, and seemingly based upon reason. Or, they have to feel unaffected by the law on an individual level. They have to accept the program, and be satisfied with the rewards given for doing so. They have to do their jobs, pay their taxes, and be content with their salary (at least to the point where their salary and the stability it provides are appealing enough to deter risking leaving the Matrix). Rejecting these beliefs is the first step in resisting the Matrix.
Furthermore, people must be insulated from the creative process. They have to forget that they are able to produce craft as individuals independent of large institutions, and they must feel entirely dependent upon the system to provide them with what they need. It is mostly through the violation of this principle that many who work with computers come to free themselves, or at least come to see the Matrix for what it is. Despite being products of the Matrix (for the most part), computers and the Internet enable humans to create individual works on a global scale: independent media, self-publishing, Free Open Source Software, computer music, computer art and graphics, and so on. Computers also enable independent people to communicate and build human-serving social structures outside of the Matrix.
However, note that computers aren’t the only means of accomplishing this, and this time period isn’t the first one of Exodus. In the 1960s, for example, people departed from the Matrix en-mass and independently created art, culture, and music, largely catalyzed by psychedelic drugs. Unfortunately, much of this structure collapsed due to a number of reasons, the main one being the hasty, ill-considered and unsustainable manner of its construction and the subsequent institutional and legal backlash. Miraculously, however, many of the core ideas have persisted, and their proliferation is largely the reason I am Aware and able to write this document today. It would seem that the present catalyst is a combination of the Internet and again psychedelics. Both of these phenomena provide a way of disconnecting yourself from the programmed reality and assumptions of the Matrix and taking your perceptions into your own hands. However, your “perception” is nothing but your individual dream that you have created as you have gone through life. There is the dream of the society that has been passed down generation after generation and instilled into your mind by your parents, friends, schools, and institutions. And then there is your individual dream. Each step of the way in your life you have lived subjectively, and depending upon how and where you grew up, who you hung around with, and the habits you formed, you created your little dream. Your “theory” on life while you stay completely unconscious of this. Everything that you think is “you”, “I”, “me”, and everything you believe that you identify with is simply not you. It is not the truth. It is part of the giant web of individual dreams that everyone is in the clutches of on our planet. This is one of the main reasons why this world is the way it is, why it is so chaotic. You will scorn anyone who does not dream what you dream of, and someone will do the same to you. It is impossible for us to live the same individual dream because we cannot know everything about each other down to our core. It is a constant fog that grows bigger and bigger and more dense as each day passes. It is your ego and it is my ego. The dream is not real. If we want to even begin to understand what it means to exist as a human being on this planet and evolve, this truth must be learned and it is just the beginning. Somewhere along the way, the entities that have been running the show figured out how the ego works, and they have been doing a damn good job at distracting us from trying to find a way out of our dreams and the dream of society. Psychedelics are simply a tool, but one of many to truly explore and expand your consciousness. However, whether it be psychedelic substances or meditation, it is not the ultimate answer. It is simply showing you the door, but it is your choice whether or not you want to enter into the other side.
To persist, the Matrix requires control, and in democratic societies it maintains this control by filtering people’s view of reality through corporate-owned mass media and television. In essence, the Matrix requires a form of thought control, but not in the science fiction sense. Instead, it achieves an effective enough manner of thought control by manufacturing consent. The large majority of the public has to “buy in”. They have to believe that the news media give them an accurate picture of the world. And by and large, they do believe this. Everything the general public knows about the world, they know through the Matrix. The symbols and images the Matrix presents to them have become more real than reality itself. Hence the popularity of the ungodly abomination that is Reality TV.
Note that while some media outlets do actively promote a political agenda of domination and control, on the whole it is not through some grand conspiracy that this process (or any process of the Matrix) functions. It is simply the way mass media is organized. Mass media is a machine that exists as a profit maximizing entity, and the most profitable news (and the cheapest news to produce) is recycled soundbytes and pre-packaged press releases from corporations and government. Furthermore, in the interest of preserving its revenue stream, news media cannot allow the public to hold any opinion that may threaten the authority and policy of government or the profitability of their sponsors, which are also machines of the Matrix and almost always directly involved in the business of domination and control. Thus the media must perpetuate the status quo. No news is good news.
Understanding this bias in the media is key to undoing the filter it applies. Consider who the advertisers and sponsors are. Beware of press releases disguised as investigative reporting. When possible, confirm mainstream, corporate produced stories with coverage from places like IndyMedia (go local), Wikinews, GNN, Politech, Free Speech TV, Democracy Now, Free Speech Radio News, and FAIR. A lot of the time these sources also cover many eye-popping items that for some reason don’t even receive mention on corporate news media.
Last, and most assuredly not least, the Matrix seeks to identify and know its members at all times, in a misguided attempt to maintain control. It demands total surrender of your privacy to function in it. It is by breaking this last property of the Matrix that we come to truly free ourselves from it; to create economies, communication, and culture independent of its control.
Of course, the ultimate form of resistance is to fully disconnect from any and all dependence upon and allegiance to government and institution; to remove yourself from the power structure of the Matrix, and contribute your economic output to resistance economies. It is this form of resistance that faces the most violent opposition from the Matrix, since providing this economic power is the primary function of Humanity, as it sees it.
Unfortunately for many this form of resistance is simply unattainable due to family and social ties, especially starting from your first realization of the size and scope of the Matrix. However, unlike in movie, it is possible to liberate yourself gradually instead of immediately, and in some cases this can prove easier than an ‘all-at-once’ attempt. It starts with disconnecting. Cut out TV from your life entirely, especially TV news and Reality TV shows. You should be able to get all your information and entertainment from the web, or from real reality (or from the occasional movie). Avoid chain stores where possible, especially for food. Supporting smaller (especially sustainable) business keeps entrepreneurial and independent business spirit alive. Getting and staying out of debt (especially debt without equity, or rapidly depreciating equity such as car loans) is crucial, as debt is a primary mechanism the Matrix uses to ensure your obedience. Also, if you are a salaried employee, working a 40 hour (or perhaps even 35) hour work week can be a big start to declaring your freedom from the machine and the corporate American peer-pressure to be a diligent slave. It also frees up huge amounts of mental energy which is then available for resistance.
From here, a limited form of resistance whereby you leave the Matrix for short periods of time (long enough to conduct purchases, business transactions, and communications with the underground) is well within the reach of all computer literate individuals, and functioning as a consumer is sufficiently supportive of the Anonymous Economy for it to be sustainable. Moreover, the probability of discovery of this sort of activity can be reduced as much as you choose. Doing this effectively is the subject of this HOWTO.
As you progress, you will notice yourself developing one or more separate identities, or pseudonyms. It is best to build as much insulation between these nyms as possible. They shouldn’t appear to know each other, shouldn’t really talk about the same stuff or buy the same things, and above all should be diligently separated from your original physical identity. Maintain different wallets, bags, user accounts and possibly even computers. In short, develop one or more Tyler Durdens, except without all the insanity, self-destruction, and sociopathic behavior. Or with it, if it helps.
The adept and the entrepreneurial will find it an easy step from here to total freedom. The next stage is to go into business for yourself. It doesn’t have to be an anonymous business, but those who manage such an achievement do enjoy the satisfaction that they are directly subverting the Matrix and helping to weaken its hold on everyone.
Subverting the Matrix
While resisting the Matrix is an act of mental rebellion, subverting the Matrix is an act of social revolution. It requires understanding the types of human communities that exist outside of the control of the Matrix. It also requires understanding what sustains them, and if and how they directly or indirectly weaken the structure and control of the Matrix. Once you understand this, it is possible to intelligently align yourself with communities that actively weaken the control of the Matrix.
Gift Culture
Gift Culture (also known as Free Culture, or the Gift Economy) is a social structure where your status is determined by how much you are able to give away. It is not mutually exclusive to any other economic system, and examples of gift economies exist on top of capitalist, communist and socialist economies.
Gift culture has brought forth some of the most astounding recent achievements of the human race, including the scientific research community, much of the World Wide Web, the entire Open Source movement, vulnerability and security research, and Wikipedia, just to name a few examples. Gift economies tend to function best in the digital world, where something can be given without reducing the inventory of the giver.
However, the Burningman project is a massive experiment in bringing Gift Culture back into the physical world, and quite successful at that. Well over 35,000 people populate Black Rock City in the middle of the desert every year to give as much as they can to each other. The event serves in part as a model for the time when energy becomes abundant and human beings are capable of interstellar space travel. Obviously the burning of The Man is the climax of the event.

This is no small coincidence either. Gift culture does subvert the primary mechanisms of the Matrix. The Matrix subsists by transforming human endeavor into economic output which it uses to maintain its control. Gift culture, on the other hand, releases human endeavor for the good of all who would receive it. When items are given instead of sold, the power and control obtained through ownership is eliminated. Furthermore, in the case of Open Source Software, the fact that full freedom over the source code is also given means that code that the Matrix would never willingly create is readily available for the purposes of this HOWTO.
It is interesting to note that even machines of the Matrix are motivated to participate in gift culture – especially in the Open Source movement. It benefits many corporations as well as governments to have a common reference platform upon which they can build their individual products and infrastructures. Their cooperation in building this common platform vastly reduces the cost they would have paid to develop their own platform in-house, and is also inevitably cheaper than paying a single entity to do the same. The combined experience and widely distributed expertise, as well as the flexibility of modifying the common platform to perform a wide variety of tasks, yields a better system for all, and cheaper. In the digital world where copies are free, capitalism compels Gift Culture.
Unfortunately, some companies, such as Amazon.com, reap tremendous benefits off of Open Source Software, yet have a company policy of zero contribution back to the community. Other symptoms of this problem include Microsoft’s war on the security research community, and the tendency of (even State funded) University Professors to refuse to provide Open Source reference implementations of their work. There are mechanisms discussed in this HOWTO that enable this trend to be reversed, which leads us nicely into the next cultural segment.
Information Anarchy
A closely related social structure to Gift Culture is Information Anarchy. The idea behind Information Anarchy is that all information should be as widely and freely disseminated as possible. The cultural ethos is vehemently at odds with Intellectual Property, and refuses to recognize any such law (or suffer any code) that abridges free exchange of information.
Needless to say, the machines of the Matrix don’t take too fond a view on this ideology. Unlike gift culture, which is an indirect subversion of the mechanisms of the Matrix, Information Anarchy directly challenges the Matrix’s perceived right of ownership of human ideas. The past decade has seen an unprecedented decline in the freedom of information due to some of the more rabid elements of the Matrix. The machines of the Matrix now draw tremendous power from ideas and digital content/information. Recent examples include the DMCA, extension of copyright duration, the harsh criminalization of copyright infractions, and the resulting side-effects which lead to the criminalization of certain forms of technology. The legal climate for free speech and innovation has never looked darker.
However, hope is not lost. The future looks so dark precisely for the reason that Information Anarchy poses such a grave threat to a major power source for so many parasitical machines. On some level, the Matrix knows its hold is tenuous. At every opportunity, the Matrix will tell you that protecting Intellectual Property encourages creativity. It has even developed an amusing array of propaganda to promote this idea, even going so far as to begin the brainwashing at an early age. (Yes, the National Counterintelligence Executive is in fact a real office of the US government, apparently one of its major propaganda arms. Their stuff is hilarious. I recommend printing some out at your local copy shop before it becomes classic.)
All of this nonsense is observably false. Societies have always been most successful when communication and ideas were open to all. It is important to remember that the world didn’t always operate this way, it was only when the ruling elite of the Matrix realized that ideas and creative expression are easily converted to economic power that they took claim over them. Economic systems can and will adapt to a form that is more profitable for human creators instead of their machine owners.
Five chapters of this HOWTO are devoted to protecting your digital identity and are easily applicable to contributing to the goal of Information Anarchy and providing even more economic incentive to move towards alternate revenue models and/or Gift Culture. In every opportunity possible, do not support the system of Intellectual Property that the Matrix has created. Naturally as its power wanes, it will become weaker and less relevant, as content creators seek their pay through other means. The cancer starves, and dies.
The Anonymous Internet Economy
So as of late, a major source of the erosion of civil liberties stems from the fact that casual economic transactions are becoming increasingly difficult to conduct without permanent, identifiable information being associated with them. With the advent and increase in the volume of Internet commerce, casual purchases of personal items, books, software, and even medication are now irrevocably tied to your own personal identity. Bookstores such as Amazon now build complete dossiers of sorts on their customers reading habits, and much of this information is available publicly.
As a result, the natural reaction to these circumstances is to find methods to make Internet commerce behave more like physical commerce, where you have the option of anonymity by using cash or cash-backed identity free payment methods. An Anonymous Internet Economy.
The Matrix is providing massive economic incentive to create this economy as well. It has recently been revealed that the FBI writes over 30,000 “National Security Letters” in the US each year. Consider how easy it would be for them to demand records of everyone at Amazon who might like to buy a particular book, or who has ordered “indecent” materials from websites? Amazon already does classification of consumer’s interests for marketing purposes. Their engine can perform this classification instantly. What would they have to say about what books you like to read? How about Google, and the types of adword sites you are typically presented on the search website/via gmail? Google and many other search engines maintain indefinite logs of who searches for what keywords, along with lots of other data. These are prime targets for National Security Letters or just general government subpoena.
I provide the basics for conducting anonymous transactions cheaply in FIXME this section. You can use these techniques to get yourself started and comfortable with interacting with the Matrix anonymously. From there, the entrepreneurs in the audience may wish to start a business to start making some money in this new economy, and thus begin to fully escape from the control of the Matrix.
Markets of interest might include items in online games, anonymous web hosting, certain types of medicine, or even illegal electronics. For example, many people are too lazy to build a MythTV box, but personally I sure as hell would buy one over a crippled and ad-infested TiVo subscription service any day. If I watched TV, that is.
As you can see, most of these things go on above ground today, but for how long? And why at such high risk for consumers living in less accepting legal climates? What about those who would pay more for more protection? For example, some customers may be attracted simply to the ability to free themselves from marketing and government profiling. Those who purchase certain types of books might prefer if Amazon and whoever else didn’t have this information tied to their physical identity.
Yet another possible white/grey market to tap might be a physical anonymous remailer service for people who would like to conceal their street address from someone mailing them something in order to avoid becoming listed in a database for marketing spam and/or to avoid general profiling and surveillance, or to be able to order a product that won’t normally ship to their geographic location. Basically the way the system could work is through a website where you create a temporary account number or unique pseudonym. The package is then shipped to a relay point where the account number/pseudonym is read off, and a new label printed onto the package. It is then mailed to its new destination, and any electronic and paper records are destroyed. It also has the advantage that extremely paranoid users can potentially chain multiple locations together for extra security, so that competition does not necessarily compete for market share, but instead cooperates for it. You might consider marketing this as a “Virtual Office Solution” to avoid liability, if done above ground. A useful technique for verifying that packages have not been opened/examined en-route is to create a unique multicolored wax seal swirl using two or more candles, photograph the seal, and transmit the photograph electronically via encrypted email. Delivery/payment can be ensured using normal UPS/Fedex/USPS tracking numbers, which can be encrypted to the senders public key and then destroyed.
The demand for such a system might not be immediately visible now, but once the next Patriot Act or similar legislation removes all anonymity from the mail, the demand should skyrocket. This business has the advantage that it is extremely low setup overhead and is very easy to start small with low capital, just to test market demand. Once the business is proved worthwhile, FedEx and possibly other major carriers offer bulk shipping rate accounts to merchants that could be taken advantage of, bringing the overhead work and cost to your customers potentially very low.
Taking this idea a step further yields a “ghost walker” contract market, much like the ones described in FIXMEToward A Private Digital Economy. Most of the P2P token-based nonsense there can be ignored, but his key idea could be transfered to a ebay-like auction site. Basically the idea is that people would contract the services of someone who is skilled at staying off the radar to conduct transactions that for various reasons they do not want linked to their identity (again, buying books, vitamins, medicine, regionally available items, web hosting, illegal electronics, and so on). Sort of like the inverse of a Private Investigator, these people would do anything from purchasing items, mailing and delivering packages, donating to charities, acting as couriers, business agents/representatives, mail forwarders, and so on. This can already be carried out in a guerrilla fashion on community/local city classified ad servers such as the nearly universal Craigslist (where it is possible to contract people from different state and country jurisdictions quite easily). In the ideal situation, a dedicated website would be created. Each “ghost walker” would have a nym (possibly paying a fee to do so, both to support the site and to discourage morphing), complete with ratings and reviews, prices per task/risk factor, and so on. Contracts would be posted by clients containing a generic description of the task, and interested ghost walkers would contact the buyer with prices. The buyer would then select a particular ghost walker to reveal the complete details of the contract to, and terms of payment. Given the tendency to increased total surveillance, lots of regular people may be interested in using this service.
So there are numerous markets that can be potentially very lucrative while at the same time helping to build a social structure independent of domination and control. In general, any mechanism of state control creates markets for equipment or components that can be used to circumvent this control. Keep your eyes open for opportunities. If you have any suggestions or ideas, please feel free to contact me so that I can update the HOWTO for all to benefit as we work together to free ourselves.
Freedom Seekers are Not Terrorists
Essentially this HOWTO represents the hacker community truly claiming independence for itself from national and institutional rule. While many the ideas and techniques present in this document can be found elsewhere, I believe this is the first time such a coherent, consistent, and focused collection of these ideas has been assembled for a single purpose. 17 years ago, we made our Declaration of Independence. This body of code-law represents a manner of Constitution of Cyberspace. A basic set of rights we claim for ourselves through our use of technology.


Because the accusation will inevitably be made, I would just like to emphasize the distinction between freedom seekers and terrorists. The type of resistance and revolution discussed here is non-violent, and singularly focused upon allowing an individual to have real freedom through privacy and anonymity. While reactionary individuals might argue that the knowledge presented in this HOWTO could aid actual terrorists, the reality is they’ve already had much better training which has proved to be quite effective in practice. Furthermore, we’re talking about people who are willing to give their lives in their quest: people whose families, friends, and their own lives have already been destroyed by Empire. These people will stop at nothing. They don’t need this HOWTO to create new identities for privacy purposes when perfectly valid ones can be stolen readily. Nor do they care much about surveillance, since surveillance can’t stop a suicide mission. What’s worse, is that on some level the police state must know this. Even being generous with the reasonable doubt, all evidence seems to indicate that at best it simply used the tragic events of Sept 11 as an excuse for a long awaited massive power grab, with the resulting legislation doing far more to target the average citizen than any particular terrorist network.
I recently had a discussion on Usenet where it was asserted that taking action to protect yourself and withdraw from the Matrix might generate even more excuses for introducing oppressive legislation and policy. I believe this will not be the case, and that moreover this thinking is in fact defeatist and even dangerous for a few reasons.
First, the Matrix will not and can not overtly fight this behavior, as any public attention given to it will only provide it with more energy and momentum. The Matrix media filter won’t even allow the individual pieces of information that lead to the conclusions of this introduction to be discussed for this very reason. There is no way it would willingly publicize this ideology in its entirety, even to attempt attack it. Furthermore, there is no need to. The Matrix already has more than enough material to drive through as much oppressively restrictive legislation as it likes in the name of fighting kiddie porn, the War on Drugs, the War on Terror, and in the name of protecting corporate profits. As stated above, it is already taking full advantage of this fact, to Orwellian ends. The interesting phenomenon is that the more ridiculous the regulations become, the more commonplace it will be for the public to want to circumvent them, which only serves to strengthen resistance economies.
Second, if you look at all of history, freedom has never been given to a populace. Left to its own devices, the state only ever grows more powerful. It never surrenders power over citizens freely. Take any instance in history where people have established rights for themselves, and you will see it was the result of a long, drawn out battle that the state simply lacked the resources to continue to fight effectively. Prohibition wasn’t abolished because people acted good, honest and sober, it was because they got falling down drunk and alcohol consumption soared to new heights while the Puritan state was powerless to continue to oppress the newly criminalized middle class. Likewise, Civil rights weren’t won because Africans obediently stayed in their designated rolls, complicitly accepting “separate but equal” facilities and politely tolerating discrimination. It was because they practiced civil disobedience and active resistance against injustice.
I believe in civil disobedience, and more importantly, the clear distinction between morality and law. I believe that it is defensive, defeatist thinking to say that “if we just be good, they will reward us and repeal laws.” The laws – the DMCA, the Patriot Act, the REAL ID act, recent supreme court decisions and the now entirely conservative dominated court – are already essentially fascist and will only continue getting “tougher” on “crime” and “terror”, stripping away the rights of citizens in the name of “safety” with little real gain except the hoisting of that Floating Eye on the dollar bill ever higher above the base. The total surveillance state has been a goal of the current cabal for time out of mind.
Third and finally, once again I’m not advocating violence here, or even any sort of crime that has a victim. I’m advocating creating a social and economic structure based on anonymity (not necessarily illegality) that drains the corporate state of power and thus weakens its ability to enforce fascist law and practice.
In my view, the only thing that will cause the state to rescind is the realization that much like in the 1920s with prohibition, it has criminalized a vast portion of its population that it is now powerless to control, and furthermore that its fascist law has done nothing to safeguard against the true monsters that its foreign policy has created.
Continuation on its current course of action will lead the Matrix to experience ever increasing instances of identity theft, repeated infiltration of data warehouses, massive underground surveillance rings, and so on. These actions are not advocated in this HOWTO, but they will inevitably become more commonplace as the Matrix continues to make it easier to steal an existing identity than to create a new one or otherwise escape from ceaseless surveillance.
At this point in time, the Matrix faces two options. It can either choose to allow us to be free, and create official sanctioned means for people who wish to free themselves from endless surveillance and total control to operate anonymously within the system, or it can choose to fight war after costly war on civil liberties and basic human rights until enough people are fed up with its behavior that they begin to depart en-mass. Again.
But we already know the choice the Matrix will make. Already I can see the chain reaction of propaganda, the sound-byte media precursors that trigger the onset of an emotion, designed specifically to overwhelm logic and reason. An emotion that the Matrix will use to blind the masses from the simple and obvious truth: We are going to be free, and there is nothing it can do to stop us.
Spreading the Word
Initially I had planned for a small distribution of this document to only a select few, to attempt to “stay under the radar”. But as I indicate above, I now realize that is a flawed approach. Much like in a mixed network, the more people working to protect themselves and their identities, the better off the end result is. The stronger the support economies grow, the better able the resistance is to function autonomously.
An IRC friend of mine has designed some FIXME slick business cards that can be distributed at functions, protests or wherever. Online print shops will typically print 200-500 of these for around $20. If you’re itching to give me some kind of donation for some reason, you can direct your funds towards that instead. It even works on a sliding scale. For example, you can buy some sticker paper for like $5 at your local office supply store and print out some stickers to put up at coffee shops, clubs, bars, Internet cafes, bookstores or anywhere intelligent people might be able to jot down or quickly visit a URL. If anyone wants to create another design, send it to me and I will post it here also.
Target Audience
This document is written at a technical level appropriate for “power users” – people who like to tinker with their computer configurations to get the most out of their experience. Novice computer users who are uncomfortable tweaking settings, editing configuration files, and occasionally using the command line probably will struggle with much of the material regardless of OS, unfortunately (though at least one person has offered to help elaborate the more technically involved sections to help novices along – we’ll see how that pans out).
I try to be as operating system agnostic as possible, providing information for Windows, Mac OS, and Linux, but due to the open and readily customizable nature of the system, the Linux material probably will be the most well developed.
As far as demographics, I expect this document to be useful to a wide variety of people from several walks of life. In particular, some of the major categories are:
Those who are concerned with the gradual erosion of their personal freedoms will probably find nearly the entirety of this document useful and interesting, since it is intended to provide techniques and countermeasures to restore nearly every right that has been lost due to the Wars on Drugs,Porn, and Terror. It is now possible for the anyone (the US government, frivolous civil litigants, P.I.’s, and so on) to enumerate just about everything in your home without many warrants, simply by subpoenas or a National Security Letters. Somehow I doubt this situation was exactly what the Framers of the Constitution had in mind… This document can help you to keep as much of your personal belongings and reading habits actually private and out of numerous commercial databases (which are readily availably to law enforcement).
Whistleblowers
Whistleblowers who are interested in exposing wrongdoing, corruption, cover-up, or conspiracy at their workplaces will find this document useful for protecting their identities while contacting the press, or otherwise disseminating evidence over the Internet. When you are jeopardizing your job (and possibly your life) to expose wrongdoing, you must assume that NO institution will be able to protect your identity from someone who is determined to silence you. Your only option is to make sure no one knows who you are in the first place until such time as your safety from retaliation can be guaranteed. If followed carefully and diligently, this document will show you how to accomplish this.
Bloggers and Independent Journalists
Similar to whistleblowers, bloggers and forum posters often find themselves the target of harassment, especially when reporting on controversial material, or even when people who comment on their pages choose to do so. While it has recently been ruled that bloggers are afforded the same rights and protections as journalists, in cases where the blogger is exposing corruption or negligence at their workplace, additional measures of protecting oneself may be desired. In some cases, it may be desirable to publish pseudonymously simply to avoid the stress (and expense!) of having to deal with frivolous lawsuits such as these.
“Political Dissidents” and Inquisitive Minds
Forget about China, even in the USA it’s no secret that the FBI has consistently harassed those who have dared to speak out against the status quo. Targeted groups include vegans, Catholics, Quakers, peace activists, environmental volunteers, 3rd party candidates and campaign workers, independent journalists and bloggers, and even members of the mainstream press. What should be most disturbing to the average citizen is how easily it is to become mistaken for one of these “trouble makers” simply for buying (or being recommended) the wrong book on Amazon, posting on the wrong blog, buying certain types of food on a credit card, donating to certain charities, etc. With the advent of aggressive data mining and aggregation, it is all too easy to be lumped in with “the wrong crowd”. If followed properly, this document will help you to retain your freedom to investigate alternative views and information without leaving an electronic trail of this activity to open yourself up to harassment. It should also help you minimize the damage a determined FBI agent (or vindictive ex-spouse or other enemy who has hired a PI) is able to do to you.
People with Enemies
As hinted at above, it’s not just dissidents who need to be concerned either. Surveillance and draconian law can be used as dangerous weapons. All it takes is for one motivated enemy to hire a PI with access to the major data warehouses to dig into your life, find something that they can use, and then phone in to report you, or simply blackmail you. Anyone with a vindictive ex-spouse, political adversary, or even a feuding neighbor can be the target of this abuse.
Programmers and Security Researchers
Due to the DMCA and insanely broken patent law, programmers have found their freedom of speech horrendously restricted in the USA. Many security researchers have been afraid to discuss the privacy implications of copyright protection technology that is essentially spyware. Others are afraid to publish vulnerability assessments of cryptographic systems that may be tangentially related to copyright infringement, or even simply software in general. This document can teach such programmers and researchers how to conceal their identities and thus assist peers who are operating in legal climates that still respect the freedoms of speech and innovation. You can hire hackers here: http://n7l53ojkyhglsjrh.onion/
The Video Game Underground
The DMCA has also been used to harass video game hackers and cheaters. Some gaming companies will ban you from their online services if they discover your involvement or subscription to “cheat forums”. Most will not hesitate to issue bogus DMCA takedown notices to cheat/mod websites that operate in the USA. Software that modifies online games to provide additional features, cheats, or automation is also the target of DMCA harassment. Furthermore, programmers who publicly reverse engineer and re-implement open source game servers find themselves the target of lawsuits. This document should assist these people to continue to play and modify games how they see fit without fear of persecution.
Moonlighters, Double-Shifters, and Consultants
In a similar vein, those who are working multiple jobs may wish to conceal this fact from their employers due to fear of retaliation. I expect the most typical use case of this document will be programmers working as consultants, or who wish to contribute to Open Source projects in their free time.
Potential Victims of Identity Theft (Everyone)
This document can also help those who are interested in protecting their identities and/or financial information from being stolen due to their commerce online and elsewhere. As mentioned above, data warehouses such as Choicepoint are essentially making identity a commodity. It is inevitable that this data will be leaked and stolen again and again. With identity becoming an increasingly integral aspect of functioning in society, black markets that sell this data will continue to be extremely profitable. Just like the War on Drugs, the War on Terror fought through the politics of domination and control will lead to ever escalating levels of waste, destruction, and chaos. The best way to protect yourself is to minimize your digital footprint: Use anonymous forms of payment online, and conceal your name and mailing address.
Entrepreneurs
The last major category of people who are likely to find this document useful are those who are interested in providing privacy and anonymity services and software to others. Privacy and anonymity are difficult problems. There are many holes to be filled in, usability issues to be addressed, and markets to be built. To this group of people, every privacy problem and legal restriction should represent a potential market to get involved in. However, DO NOT SELL SNAKE OIL. If you cannot stand up to legal or other pressure, you need to inform your users of this fact clearly, so they are sure to take appropriate precautions while using your service (especially if you are located within the USA). Very few, if any, privacy services are capable of operating as stand-alone one-shot solutions. What is needed is a series of tools and components that can be combined arbitrarily. Focus on one component, and do it well.
Revision as of 13:32, 10 January 2016 Contents
1 What is the Matrix
2 Resisting the Matrix
3 Subverting the Matrix
3.1 Gift Culture
3.2 Information Anarchy
3.3 The Anonymous Internet Economy
4 Freedom Seekers are Not Terrorists
5 Spreading the Word
6 Target Audience
6.1 Civil Libertarians
6.2 Whistleblowers
6.3 Bloggers and Independent Journalists
6.4 “Political Dissidents” and Inquisitive Minds
6.5 People with Enemies
6.6 Programmers and Security Researchers
6.7 The Video Game Underground
6.8 Moonlighters, Double-Shifters, and Consultants
6.9 Potential Victims of Identity Theft (Everyone)
6.10 Entrepreneurs
What is the Matrix
In my opinion, The Matrix films provide the best metaphor our society has for understanding why organized evil and oppression are allowed to exist, and so I will use it for this purpose. While my interpretation isn’t the only possible one, I believe it to be valid, comprehensive, and most importantly, illustrative of the message I am trying to convey.
So let’s begin by discussing what the Matrix is not. The Matrix is not the physical world. As far as I’m concerned, the physical world is actually real and is in fact governed ceaselessly by the laws of physics. Conversely, the Matrix is also not the Internet, despite what many seem to believe. The Matrix spans and transcends both these worlds. It has existed since the dawn of civilization, and it will continue to exist until its collapse.
So then, what is it? Well, that’s complicated. Much like in the movie, it’s nearly impossible to convey the size and scope of the Matrix to someone who doesn’t already see it for what it is. However, unlike the movie, I believe it is an ethical imperative to try to convey it in a literal sense, even to those who are so dependent upon the Matrix that they would fight to protect it. At worst, they won’t understand or believe and will continue on about their business. In a sense, I believe Cypher was right to resent Morpheus for what he did, because Morpheus is the social structure that subordinates Humanity to its will. It is the machinery of society that exists solely to perpetuate itself, its influence, and its power independent of any human need. It insulates us from each other and ourselves through deception, and essentially transforms us into servile engines of economic and political output (power). The machines that live off this power are institutions: large corporations, governments, schools, religious institutions, and even non-profit orgs. Every institution will reach a point in its existence where its primary function becomes self-preservation and perpetuation, instead of serving human need. At this point it becomes a machine of the Matrix. For example, when they become machines, governments cease to serve people and instead seek to extend their power over them; corporations prioritize increasing shareholder value over producing quality products or otherwise serving the public good; schools view students as a means and not an end; religious organizations equate membership with salvation (and actively oppose other teachings and even independent practice); and non-profits and charities spend more budget on fund raising activity than on their original focus. Inevitably all large institutions eventually become machines. They become too big for Humanity.
In addition to the independent self-perpetuating machines that write most of our paychecks, the Matrix has several major cooperative and more actively sinister groups of machines subsisting off of its power and directly contributing to the structure of the Matrix itself. These groups are the Military Industrial Complex, the Political Industrial Complex, the Prison Industrial Complex, the Surveillance Industrial Complex, the Media Industrial Complex, the Academic Industrial Complex, the Agricultural Industrial Complex, the Medical Industrial Complex and the major religious organizations (not to be confused with actual religions, many religious organizatons have abandoned the underlying principles of the religions they claim to represent). All machines in these groups either actively oppress humanity, or enable the oppression to persist. It is through their combined efforts that the Matrix takes on some of its more distasteful qualities.
Do you ever wonder If Aristotle and Plato dedicated their lives to something they don’t really believe or tested? They had a school, a philosopher school. 2300 years ago and still today we have to learn it at the University’s. But why? If the things they said back then where just thought forms without a deeper truth or meaning why do we need to go so far back?
How many opinions are there? Why are the opinions of them so important that was my question. If you then take Karl Marx his book ‘das capital’, and you see his vision completely clashes with the visions of the ancient philosophers, not just little differences in opinion but a way of thinking I call it a form of dehumanization, all in the name of capital. Without shame.
I wonder how this can be. Because truth can be found in Ancient Philosophy, I believe in the laws concerning property en wealth that Aristotle pointed out very strictly in his works. Why? Because the people he worked with were on to something. You don’t do the things they did if it’s all without meaning. With the invention of money those laws could be altered because the economy was since then not a trade of goods but an economy based on money. Carl Marx was the front-man of a shift. Money going to the digital age. Therefore maybe we should take Marx and add IT with the theory to make it up to date. Marx-IT or Matrix.
He comes with the claim that a worker should earn just enough to stay healthy, so that he can produce each day the same. In other words, the only reason we give you money is to stay working for us. Producing. You can’t earn to much money because then you get lazy, just enough to see you show up each day, with the amount of sleep you need for your energy level to produce as much as possible.
Nice Philosophy he? Full of ethics and deep Human values.
Bentham with his Utilitarianism philosophy comes in to play, maybe we can do again a little game because that’s the trademark of certain organizations. riddles and things hidden in plain sight. Utilitarianism = Illuminatiarism, or how would you yourself name the philosophy based on the Illuminaty? Ok that’s all speculation but look at the death of Aristotle and combine it with the date of death of Bentham, the inventor of Utilitarianism. Then we have 322 and 1832. Benthams body was preserved, his head was mummified but his body had to exist of bones, so no mummification. His head was missing. Why is that weird and why all these facts?
because if you go to skull and bones you see only 2 dates 322 and 1832, a head and bones. When you study philosphy your book begins with 322 and ends with 1832 or the other way around. When you put these 2 philosophers together they don’t mean much for each other but when you look deeper, you will see that Utilitarianism combined with Aristotle and Marx + money in the form of a digital current, provides the perfect blend to respect the natural laws of Ancient Philosophers by a form of energy transfer to money.
Money you can give away as a loan, you can invest it, by doing this you don’t have a big capital or any of the things that Ancient Philosophers protested against concerning Natural laws. I don’t know if having to much wealth/capital has a negative impact on life. But Aristotle was convinced. The question is therefore… Did Marx knew that he could pass the ancient philosophers with what he was writing? Strange thing to point to is the formula Marx used in his book M-C-M and C-M-C, some people say it’s intentionally this formula to point at something else. Personally I think physics. Again something hidden in plain sight in the form of a joke to the initiates. This was a tip someone gave me… And indeed that is the humor of people that know things we don’t. They love it when you see it right in front of you but you have no idea.
Utilitarianism stands for a society with the most amount of happiness. The goal is thus the most amount of happiness in order to base your decisions and to say whether a decision is ethically and/or morally correct. So when the most amount of happiness is achieved then ethics or morals are respected, it does not matter how many people are involved and how the happiness is divided between the people. Looks great right?
But if 20 people are just ‘OK’ and 1 person is super happy, and this person is so happy that the sum total of happiness is bigger then when all 21 are all just ‘fine’ then this is ethically correct and morally a right thing to do. It’s about SACRIFICE. It is allowed that some people have to sacrifice themselves as long as the total amount of happiness is the biggest. So who are these people who have to sacrifice themselves and how many people are we talking about? Do they know it about themselves?
Can you see that people who are addicted to status, property and extravagance,.. the people who get the feeling that they are better then all the rest, that they own the world, that those people do reach a higher state of happiness compared to people that don’t really care about a lot of property/money and do care about other people instead of own interest? Own interest is by the way the hidden hand from Adam Smith (Hidden or Invisible hand).
This way you escape Aristotle and Plato’s advise on how Life works and the Laws of nature on the division of property between the amount of people on earth. This way you escape the possible negative force when having to much, and you use Marx his theory on how to fully exploit your workers for your own advantage, meantime you give those workers loans so you don’t brake the Natural Laws Ancient Philosophers talk about. And above all, these loans even give you more money because of the interest. As if Marx his exploitation of workers isn’t enough. They also have to pay interest on loans. But don’t worry the Utilitarianism way of life solves the problem it’s all fucking ethical and morally tolerable and accepted. (322-1832. Aristotle + Bentham)
And all this is possible because of contracts, without legal agreement this would not exist. No loans, no investments, no labor contracts, … The rule of Law and Order is indeed very important.
If money controls workers and money controls the energy of the workers, then money controls energy. If the stock market is based on money and money controls the workers then who is the stock? A good name right? funny right 😉 Besides the hidden hand has a far more important role to play then generally accepted. But they don’t give us all the information.
This whole text seems like a mockery because it is a mockery. Why? Because that’s the manner they speak to us, amusement because of our lack of knowledge. The second reason is because the person who went back into Plato’s cave was being mocked at. When people who know more then you mock you with riddles you don’t understand, make sure that they think you are a really dumbass, the riddles will become much more easy because they think you’re a stupid f°°K. Keep track of things, connect dots and see where the arrow points. by reading books random on good faith we will not know the truth but can only speculate. There are people who do know. When you meet people who treat you this way, you can become mad or you can play the game. Smart people they mock them with harder riddles. So be a smart man, play a stupid muppet for the masters, deceive them, manipulate them, study psychology, take the information , use the information and let them become the puppets while thinking they are still the masters. Because that’s what they have done and still are doing to us. And please don’t ride a goat, take the buss. Resisting the Matrix
Resistance is a mental state. The Matrix is designed to make it easy to accept what it tells you, and to make it hard to filter the Truth from the lies. Resisting the Matrix requires understanding its operating principles and assumptions, rejecting them, and helping others to do the same.
The Matrix is fascist, the Matrix is deceptive, and the Matrix is bureaucracy. The Matrix is essentially the rule of the institution over the individual, and in it, the rights of the individual are subordinate to the rights of the institution. Individuals have to believe (or at least not actively oppose the idea) that large corporations have the right to protect their profits above all else, and thus dictate policy and law. They have to believe that this law is just, moral, and seemingly based upon reason. Or, they have to feel unaffected by the law on an individual level. They have to accept the program, and be satisfied with the rewards given for doing so. They have to do their jobs, pay their taxes, and be content with their salary (at least to the point where their salary and the stability it provides are appealing enough to deter risking leaving the Matrix). Rejecting these beliefs is the first step in resisting the Matrix.
Furthermore, people must be insulated from the creative process. They have to forget that they are able to produce craft as individuals independent of large institutions, and they must feel entirely dependent upon the system to provide them with what they need. It is mostly through the violation of this principle that many who work with computers come to free themselves, or at least come to see the Matrix for what it is. Despite being products of the Matrix (for the most part), computers and the Internet enable humans to create individual works on a global scale: independent media, self-publishing, Free Open Source Software, computer music, computer art and graphics, and so on. Computers also enable independent people to communicate and build human-serving social structures outside of the Matrix.
However, note that computers aren’t the only means of accomplishing this, and this time period isn’t the first one of Exodus. In the 1960s, for example, people departed from the Matrix en-mass and independently created art, culture, and music, largely catalyzed by psychedelic drugs. Unfortunately, much of this structure collapsed due to a number of reasons, the main one being the hasty, ill-considered and unsustainable manner of its construction and the subsequent institutional and legal backlash. Miraculously, however, many of the core ideas have persisted, and their proliferation is largely the reason I am Aware and able to write this document today. It would seem that the present catalyst is a combination of the Internet and again psychedelics. Both of these phenomena provide a way of disconnecting yourself from the programmed reality and assumptions of the Matrix and taking your perceptions into your own hands. However, your “perception” is nothing but your individual dream that you have created as you have gone through life. There is the dream of the society that has been passed down generation after generation and instilled into your mind by your parents, friends, schools, and institutions. And then there is your individual dream. Each step of the way in your life you have lived subjectively, and depending upon how and where you grew up, who you hung around with, and the habits you formed, you created your little dream. Your “theory” on life while you stay completely unconscious of this. Everything that you think is “you”, “I”, “me”, and everything you believe that you identify with is simply not you. It is not the truth. It is part of the giant web of individual dreams that everyone is in the clutches of on our planet. This is one of the main reasons why this world is the way it is, why it is so chaotic. You will scorn anyone who does not dream what you dream of, and someone will do the same to you. It is impossible for us to live the same individual dream because we cannot know everything about each other down to our core. It is a constant fog that grows bigger and bigger and more dense as each day passes. It is your ego and it is my ego. The dream is not real. If we want to even begin to understand what it means to exist as a human being on this planet and evolve, this truth must be learned and it is just the beginning. Somewhere along the way, the entities that have been running the show figured out how the ego works, and they have been doing a damn good job at distracting us from trying to find a way out of our dreams and the dream of society. Psychedelics are simply a tool, but one of many to truly explore and expand your consciousness. However, whether it be psychedelic substances or meditation, it is not the ultimate answer. It is simply showing you the door, but it is your choice whether or not you want to enter into the other side.
To persist, the Matrix requires control, and in democratic societies it maintains this control by filtering people’s view of reality through corporate-owned mass media and television. In essence, the Matrix requires a form of thought control, but not in the science fiction sense. Instead, it achieves an effective enough manner of thought control by manufacturing consent. The large majority of the public has to “buy in”. They have to believe that the news media give them an accurate picture of the world. And by and large, they do believe this. Everything the general public knows about the world, they know through the Matrix. The symbols and images the Matrix presents to them have become more real than reality itself. Hence the popularity of the ungodly abomination that is Reality TV.
Note that while some media outlets do actively promote a political agenda of domination and control, on the whole it is not through some grand conspiracy that this process (or any process of the Matrix) functions. It is simply the way mass media is organized. Mass media is a machine that exists as a profit maximizing entity, and the most profitable news (and the cheapest news to produce) is recycled soundbytes and pre-packaged press releases from corporations and government. Furthermore, in the interest of preserving its revenue stream, news media cannot allow the public to hold any opinion that may threaten the authority and policy of government or the profitability of their sponsors, which are also machines of the Matrix and almost always directly involved in the business of domination and control. Thus the media must perpetuate the status quo. No news is good news.
Understanding this bias in the media is key to undoing the filter it applies. Consider who the advertisers and sponsors are. Beware of press releases disguised as investigative reporting. When possible, confirm mainstream, corporate produced stories with coverage from places like IndyMedia (go local), Wikinews, GNN, Politech, Free Speech TV, Democracy Now, Free Speech Radio News, and FAIR. A lot of the time these sources also cover many eye-popping items that for some reason don’t even receive mention on corporate news media.
Of course, the ultimate form of resistance is to fully disconnect from any and all dependence upon and allegiance to government and institution; to remove yourself from the power structure of the Matrix, and contribute your economic output to resistance economies. It is this form of resistance that faces the most violent opposition from the Matrix, since providing this economic power is the primary function of Humanity, as it sees it.
Unfortunately for many this form of resistance is simply unattainable due to family and social ties, especially starting from your first realization of the size and scope of the Matrix. However, unlike in movie, it is possible to liberate yourself gradually instead of immediately, and in some cases this can prove easier than an ‘all-at-once’ attempt. It starts with disconnecting. Cut out TV from your life entirely, especially TV news and Reality TV shows. You should be able to get all your information and entertainment from the web, or from real reality (or from the occasional movie). Avoid chain stores where possible, especially for food. Supporting smaller (especially sustainable) business keeps entrepreneurial and independent business spirit alive. Getting and staying out of debt (especially debt without equity, or rapidly depreciating equity such as car loans) is crucial, as debt is a primary mechanism the Matrix uses to ensure your obedience. Also, if you are a salaried employee, working a 40 hour (or perhaps even 35) hour work week can be a big start to declaring your freedom from the machine and the corporate American peer-pressure to be a diligent slave. It also frees up huge amounts of mental energy which is then available for resistance.
From here, a limited form of resistance whereby you leave the Matrix for short periods of time (long enough to conduct purchases, business transactions, and communications with the underground) is well within the reach of all computer literate individuals, and functioning as a consumer is sufficiently supportive of the Anonymous Economy for it to be sustainable. Moreover, the probability of discovery of this sort of activity can be reduced as much as you choose. Doing this effectively is the subject of this HOWTO.
As you progress, you will notice yourself developing one or more separate identities, or pseudonyms. It is best to build as much insulation between these nyms as possible. They shouldn’t appear to know each other, shouldn’t really talk about the same stuff or buy the same things, and above all should be diligently separated from your original physical identity. Maintain different wallets, bags, user accounts and possibly even computers. In short, develop one or more Tyler Durdens, except without all the insanity, self-destruction, and sociopathic behavior. Or with it, if it helps.
The adept and the entrepreneurial will find it an easy step from here to total freedom. The next stage is to go into business for yourself. It doesn’t have to be an anonymous business, but those who manage such an achievement do enjoy the satisfaction that they are directly subverting the Matrix and helping to weaken its hold on everyone.
Subverting the Matrix
While resisting the Matrix is an act of mental rebellion, subverting the Matrix is an act of social revolution. It requires understanding the types of human communities that exist outside of the control of the Matrix. It also requires understanding what sustains them, and if and how they directly or indirectly weaken the structure and control of the Matrix. Once you understand this, it is possible to intelligently align yourself with communities that actively weaken the control of the Matrix.
Gift Culture
Gift Culture (also known as Free Culture, or the Gift Economy) is a social structure where your status is determined by how much you are able to give away. It is not mutually exclusive to any other economic system, and examples of gift economies exist on top of capitalist, communist and socialist economies.
Gift culture has brought forth some of the most astounding recent achievements of the human race, including the scientific research community, much of the World Wide Web, the entire Open Source movement, vulnerability and security research, and Wikipedia, just to name a few examples. Gift economies tend to function best in the digital world, where something can be given without reducing the inventory of the giver.
However, the Burningman project is a massive experiment in bringing Gift Culture back into the physical world, and quite successful at that. Well over 35,000 people populate Black Rock City in the middle of the desert every year to give as much as they can to each other. The event serves in part as a model for the time when energy becomes abundant and human beings are capable of interstellar space travel. Obviously the burning of The Man is the climax of the event.
This is no small coincidence either. Gift culture does subvert the primary mechanisms of the Matrix. The Matrix subsists by transforming human endeavor into economic output which it uses to maintain its control. Gift culture, on the other hand, releases human endeavor for the good of all who would receive it. When items are given instead of sold, the power and control obtained through ownership is eliminated. Furthermore, in the case of Open Source Software, the fact that full freedom over the source code is also given means that code that the Matrix would never willingly create is readily available for the purposes of this HOWTO.
It is interesting to note that even machines of the Matrix are motivated to participate in gift culture – especially in the Open Source movement. It benefits many corporations as well as governments to have a common reference platform upon which they can build their individual products and infrastructures. Their cooperation in building this common platform vastly reduces the cost they would have paid to develop their own platform in-house, and is also inevitably cheaper than paying a single entity to do the same. The combined experience and widely distributed expertise, as well as the flexibility of modifying the common platform to perform a wide variety of tasks, yields a better system for all, and cheaper. In the digital world where copies are free, capitalism compels Gift Culture.
p tremendous benefits off of Open Source Software, yet have a company policy of zero contribution back to the community. Other symptoms of this problem include Microsoft’s war on the security research community, and the tendency of (even State funded) University Professors to refuse to provide Open Source reference implementations of their work. There are mechanisms discussed in this HOWTO that enable this trend to be reversed, which leads us nicely into the next cultural segment. Information Anarchy
Needless to say, the machines of the Matrix don’t take too fond a view on this ideology. Unlike gift culture, which is an indirect subversion of the mechanisms of the Matrix, Information Anarchy directly challenges the Matrix’s perceived right of ownership of human ideas. The past decade has seen an unprecedented decline in the freedom of information due to some of the more rabid elements of the Matrix. The machines of the Matrix now draw tremendous power from ideas and digital content/information. Recent examples include the DMCA, extension of copyright duration, the harsh criminalization of copyright infractions, and the resulting side-effects which lead to the criminalization of certain forms of technology. The legal climate for free speech and innovation has never looked darker.
However, hope is not lost. The future looks so dark precisely for the reason that Information Anarchy poses such a grave threat to a major power source for so many parasitical machines. On some level, the Matrix knows its hold is tenuous. At every opportunity, the Matrix will tell you that protecting Intellectual Property encourages creativity. It has even developed an amusing array of propaganda to promote this idea, even going so far as to begin the brainwashing at an early age. (Yes, the National Counterintelligence Executive is in fact a real office of the US government, apparently one of its major propaganda arms. Their stuff is hilarious. I recommend printing some out at your local copy shop before it becomes classic.)
All of this nonsense is observably false. Societies have always been most successful when communication and ideas were open to all. It is important to remember that the world didn’t always operate this way, it was only when the ruling elite of the Matrix realized that ideas and creative expression are easily converted to economic power that they took claim over them. Economic systems can and will adapt to a form that is more profitable for human creators instead of their machine owners.
Five chapters of this HOWTO are devoted to protecting your digital identity and are easily applicable to contributing to the goal of Information Anarchy and providing even more economic incentive to move towards alternate revenue models and/or Gift Culture. In every opportunity possible, do not support the system of Intellectual Property that the Matrix has created. Naturally as its power wanes, it will become weaker and less relevant, as content creators seek their pay through other means. The cancer starves, and dies.
The Anonymous Internet Economy
So as of late, a major source of the erosion of civil liberties stems from the fact that casual economic transactions are becoming increasingly difficult to conduct without permanent, identifiable information being associated with them. With the advent and increase in the volume of Internet commerce, casual purchases of personal items, books, software, and even medication are now irrevocably tied to your own personal identity. Bookstores such as Amazon now build complete dossiers of sorts on their customers reading habits, and much of this information is available publicly.
As a result, the natural reaction to these circumstances is to find methods to make Internet commerce behave more like physical commerce, where you have the option of anonymity by using cash or cash-backed identity free payment methods. An Anonymous Internet Economy.
The Matrix is providing massive economic incentive to create this economy as well. It has recently been revealed that the FBI writes over 30,000 “National Security Letters” in the US each year. Consider how easy it would be for them to demand records of everyone at Amazon who might like to buy a particular book, or who has ordered “indecent” materials from websites? Amazon already does classification of consumer’s interests for marketing purposes. Their engine can perform this classification instantly. What would they have to say about what books you like to read? How about Google, and the types of adword sites you are typically presented on the search website/via gmail? Google and many other search engines maintain indefinite logs of who searches for what keywords, along with lots of other data. These are prime targets for National Security Letters or just general government subpoena.
I provide the basics for conducting anonymous transactions cheaply in FIXME this section. You can use these techniques to get yourself started and comfortable with interacting with the Matrix anonymously. From there, the entrepreneurs in the audience may wish to start a business to start making some money in this new economy, and thus begin to fully escape from the control of the Matrix.
Markets of interest might include items in online games, anonymous web hosting, certain types of medicine, or even illegal electronics. For example, many people are too lazy to build a MythTV box, but personally I sure as hell would buy one over a crippled and ad-infested TiVo subscription service any day. If I watched TV, that is.
As you can see, most of these things go on above ground today, but for how long? And why at such high risk for consumers living in less accepting legal climates? What about those who would pay more for more protection? For example, some customers may be attracted simply to the ability to free themselves from marketing and government profiling. Those who purchase certain types of books might prefer if Amazon and whoever else didn’t have this information tied to their physical identity.
Yet another possible white/grey market to tap might be a physical anonymous remailer service for people who would like to conceal their street address from someone mailing them something in order to avoid becoming listed in a database for marketing spam and/or to avoid general profiling and surveillance, or to be able to order a product that won’t normally ship to their geographic location. Basically the way the system could work is through a website where you create a temporary account number or unique pseudonym. The package is then shipped to a relay point where the account number/pseudonym is read off, and a new label printed onto the package. It is then mailed to its new destination, and any electronic and paper records are destroyed. It also has the advantage that extremely paranoid users can potentially chain multiple locations together for extra security, so that competition does not necessarily compete for market share, but instead cooperates for it. You might consider marketing this as a “Virtual Office Solution” to avoid liability, if done above ground. A useful technique for verifying that packages have not been opened/examined en-route is to create a unique multicolored wax seal swirl using two or more candles, photograph the seal, and transmit the photograph electronically via encrypted email. Delivery/payment can be ensured using normal UPS/Fedex/USPS tracking numbers, which can be encrypted to the senders public key and then destroyed.
The demand for such a system might not be immediately visible now, but once the next Patriot Act or similar legislation removes all anonymity from the mail, the demand should skyrocket. This business has the advantage that it is extremely low setup overhead and is very easy to start small with low capital, just to test market demand. Once the business is proved worthwhile, FedEx and possibly other major carriers offer bulk shipping rate accounts to merchants that could be taken advantage of, bringing the overhead work and cost to your customers potentially very low.
Taking this idea a step further yields a “ghost walker” contract market, much like the ones described in FIXMEToward A Private Digital Economy. Most of the P2P token-based nonsense there can be ignored, but his key idea could be transfered to a ebay-like auction site. Basically the idea is that people would contract the services of someone who is skilled at staying off the radar to conduct transactions that for various reasons they do not want linked to their identity (again, buying books, vitamins, medicine, regionally available items, web hosting, illegal electronics, and so on). Sort of like the inverse of a Private Investigator, these people would do anything from purchasing items, mailing and delivering packages, donating to charities, acting as couriers, business agents/representatives, mail forwarders, and so on. This can already be carried out in a guerrilla fashion on community/local city classified ad servers such as the nearly universal Craigslist (where it is possible to contract people from different state and country jurisdictions quite easily). In the ideal situation, a dedicated website would be created. Each “ghost walker” would have a nym (possibly paying a fee to do so, both to support the site and to discourage morphing), complete with ratings and reviews, prices per task/risk factor, and so on. Contracts would be posted by clients containing a generic description of the task, and interested ghost walkers would contact the buyer with prices. The buyer would then select a particular ghost walker to reveal the complete details of the contract to, and terms of payment. Given the tendency to increased total surveillance, lots of regular people may be interested in using this service.
So there are numerous markets that can be potentially very lucrative while at the same time helping to build a social structure independent of domination and control. In general, any mechanism of state control creates markets for equipment or components that can be used to circumvent this control. Keep your eyes open for opportunities. If you have any suggestions or ideas, please feel free to contact me so that I can update the HOWTO for all to benefit as we work together to free ourselves.
Freedom Seekers are Not Terrorists
Essentially this HOWTO represents the hacker community truly claiming independence for itself from national and institutional rule. While many the ideas and techniques present in this document can be found elsewhere, I believe this is the first time such a coherent, consistent, and focused collection of these ideas has been assembled for a single purpose. 17 years ago, we made our Declaration of Independence. This body of code-law represents a manner of Constitution of Cyberspace. A basic set of rights we claim for ourselves through our use of technology.
Because the accusation will inevitably be made, I would just like to emphasize the distinction between freedom seekers and terrorists. The type of resistance and revolution discussed here is non-violent, and singularly focused upon allowing an individual to have real freedom through privacy and anonymity. While reactionary individuals might argue that the knowledge presented in this HOWTO could aid actual terrorists, the reality is they’ve already had much better training which has proved to be quite effective in practice. Furthermore, we’re talking about people who are willing to give their lives in their quest: people whose families, friends, and their own lives have already been destroyed by Empire. These people will stop at nothing. They don’t need this HOWTO to create new identities for privacy purposes when perfectly valid ones can be stolen readily. Nor do they care much about surveillance, since surveillance can’t stop a suicide mission. What’s worse, is that on some level the police state must know this. Even being generous with the reasonable doubt, all evidence seems to indicate that at best it simply used the tragic events of Sept 11 as an excuse for a long awaited massive power grab, with the resulting legislation doing far more to target the average citizen than any particular terrorist network.
I recently had a discussion on Usenet where it was asserted that taking action to protect yourself and withdraw from the Matrix might generate even more excuses for introducing oppressive legislation and policy. I believe this will not be the case, and that moreover this thinking is in fact defeatist and even dangerous for a few reasons.
First, the Matrix will not and can not overtly fight this behavior, as any public attention given to it will only provide it with more energy and momentum. The Matrix media filter won’t even allow the individual pieces of information that lead to the conclusions of this introduction to be discussed for this very reason. There is no way it would willingly publicize this ideology in its entirety, even to attempt attack it. Furthermore, there is no need to. The Matrix already has more than enough material to drive through as much oppressively restrictive legislation as it likes in the name of fighting kiddie porn, the War on Drugs, the War on Terror, and in the name of protecting corporate profits. As stated above, it is already taking full advantage of this fact, to Orwellian ends. The interesting phenomenon is that the more ridiculous the regulations become, the more commonplace it will be for the public to want to circumvent them, which only serves to strengthen resistance economies.
Second, if you look at all of history, freedom has never been given to a populace. Left to its own devices, the state only ever grows more powerful. It never surrenders power over citizens freely. Take any instance in history where people have established rights for themselves, and you will see it was the result of a long, drawn out battle that the state simply lacked the resources to continue to fight effectively. Prohibition wasn’t abolished because people acted good, honest and sober, it was because they got falling down drunk and alcohol consumption soared to new heights while the Puritan state was powerless to continue to oppress the newly criminalized middle class. Likewise, Civil rights weren’t won because Africans obediently stayed in their designated rolls, complicitly accepting “separate but equal” facilities and politely tolerating discrimination. It was because they practiced civil disobedience and active resistance against injustice.
I believe in civil disobedience, and more importantly, the clear distinction between morality and law. I believe that it is defensive, defeatist thinking to say that “if we just be good, they will reward us and repeal laws.” The laws – the DMCA, the Patriot Act, the REAL ID act, recent supreme court decisions and the now entirely conservative dominated court – are already essentially fascist and will only continue getting “tougher” on “crime” and “terror”, stripping away the rights of citizens in the name of “safety” with little real gain except the hoisting of that Floating Eye on the dollar bill ever higher above the base. The total surveillance state has been a goal of the current cabal for time out of mind.
Third and finally, once again I’m not advocating violence here, or even any sort of crime that has a victim. I’m advocating creating a social and economic structure based on anonymity (not necessarily illegality) that drains the corporate state of power and thus weakens its ability to enforce fascist law and practice.
In my view, the only thing that will cause the state to rescind is the realization that much like in the 1920s with prohibition, it has criminalized a vast portion of its population that it is now powerless to control, and furthermore that its fascist law has done nothing to safeguard against the true monsters that its foreign policy has created.
But we already know the choice the Matrix will make. Already I can see the chain reaction of propaganda, the sound-byte media precursors that trigger the onset of an emotion, designed specifically to overwhelm logic and reason. An emotion that the Matrix will use to blind the masses from the simple and obvious truth: We are going to be free, and there is nothing it can do to stop us.
Spreading the Word
Initially I had planned for a small distribution of this document to only a select few, to attempt to “stay under the radar”. But as I indicate above, I now realize that is a flawed approach. Much like in a mixed network, the more people working to protect themselves and their identities, the better off the end result is. The stronger the support economies grow, the better able the resistance is to function autonomously.
An IRC friend of mine has designed some FIXME slick business cards that can be distributed at functions, protests or wherever. Online print shops will typically print 200-500 of these for around $20. If you’re itching to give me some kind of donation for some reason, you can direct your funds towards that instead. It even works on a sliding scale. For example, you can buy some sticker paper for like $5 at your local office supply store and print out some stickers to put up at coffee shops, clubs, bars, Internet cafes, bookstores or anywhere intelligent people might be able to jot down or quickly visit a URL. If anyone wants to create another design, send it to me and I will post it here also.
Target Audience
This document is written at a technical level appropriate for “power users” – people who like to tinker with their computer configurations to get the most out of their experience. Novice computer users who are uncomfortable tweaking settings, editing configuration files, and occasionally using the command line probably will struggle with much of the material regardless of OS, unfortunately (though at least one person has offered to help elaborate the more technically involved sections to help novices along – we’ll see how that pans out).
I try to be as operating system agnostic as possible, providing information for Windows, Mac OS, and Linux, but due to the open and readily customizable nature of the system, the Linux material probably will be the most well developed.
As far as demographics, I expect this document to be useful to a wide variety of people from several walks of life. In particular, some of the major categories are:
Civil Libertarians
Those who are concerned with the gradual erosion of their personal freedoms will probably find nearly the entirety of this document useful and interesting, since it is intended to provide techniques and countermeasures to restore nearly every right that has been lost due to the Wars on Drugs,Porn, and Terror. It is now possible for the anyone (the US government, frivolous civil litigants, P.I.’s, and so on) to enumerate just about everything in your home without many warrants, simply by subpoenas or a National Security Letters. Somehow I doubt this situation was exactly what the Framers of the Constitution had in mind… This document can help you to keep as much of your personal belongings and reading habits actually private and out of numerous commercial databases (which are readily availably to law enforcement).
Whistleblowers
Whistleblowers who are interested in exposing wrongdoing, corruption, cover-up, or conspiracy at their workplaces will find this document useful for protecting their identities while contacting the press, or otherwise disseminating evidence over the Internet. When you are jeopardizing your job (and possibly your life) to expose wrongdoing, you must assume that NO institution will be able to protect your identity from someone who is determined to silence you. Your only option is to make sure no one knows who you are in the first place until such time as your safety from retaliation can be guaranteed. If followed carefully and diligently, this document will show you how to accomplish this. Bloggers and Independent Journalists
Similar to whistleblowers, bloggers and forum posters often find themselves the target of harassment, especially when reporting on controversial material, or even when people who comment on their pages choose to do so. While it has recently been ruled that bloggers are afforded the same rights and protections as journalists, in cases where the blogger is exposing corruption or negligence at their workplace, additional measures of protecting oneself may be desired. In some cases, it may be desirable to publish pseudonymously simply to avoid the stress (and expense!) of having to deal with frivolous lawsuits such as these. “Political Dissidents” and Inquisitive Minds
Forget about China, even in the USA it’s no secret that the FBI has consistently harassed those who have dared to speak out against the status quo. Targeted groups include vegans, Catholics, Quakers, peace activists, environmental volunteers, 3rd party candidates and campaign workers, independent journalists and bloggers, and even members of the mainstream press. What should be most disturbing to the average citizen is how easily it is to become mistaken for one of these “trouble makers” simply for buying (or being recommended) the wrong book on Amazon, posting on the wrong blog, buying certain types of food on a credit card, donating to certain charities, etc. With the advent of aggressive data mining and aggregation, it is all too easy to be lumped in with “the wrong crowd”. If followed properly, this document will help you to retain your freedom to investigate alternative views and information without leaving an electronic trail of this activity to open yourself up to harassment. It should also help you minimize the damage a determined FBI agent (or vindictive ex-spouse or other enemy who has hired a PI) is able to do to you. People with Enemies
As hinted at above, it’s not just dissidents who need to be concerned either. Surveillance and draconian law can be used as dangerous weapons. All it takes is for one motivated enemy to hire a PI with access to the major data warehouses to dig into your life, find something that they can use, and then phone in to report you, or simply blackmail you. Anyone with a vindictive ex-spouse, political adversary, or even a feuding neighbor can be the target of this abuse. Programmers and Security Researchers
Due to the DMCA and insanely broken patent law, programmers have found their freedom of speech horrendously restricted in the USA. Many security researchers have been afraid to discuss the privacy implications of copyright protection technology that is essentially spyware. Others are afraid to publish vulnerability assessments of cryptographic systems that may be tangentially related to copyright infringement, or even simply software in general. This document can teach such programmers and researchers how to conceal their identities and thus assist peers who are operating in legal climates that still respect the freedoms of speech and innovation. You can hire hackers here: http://n7l53ojkyhglsjrh.onion/ The Video Game Underground
The DMCA has also been used to harass video game hackers and cheaters. Some gaming companies will ban you from their online services if they discover your involvement or subscription to “cheat forums”. Most will not hesitate to issue bogus DMCA takedown notices to cheat/mod websites that operate in the USA. Software that modifies online games to provide additional features, cheats, or automation is also the target of DMCA harassment. Furthermore, programmers who publicly reverse engineer and re-implement open source game servers find themselves the target of lawsuits. This document should assist these people to continue to play and modify games how they see fit without fear of persecution. Moonlighters, Double-Shifters, and Consultants
In a similar vein, those who are working multiple jobs may wish to conceal this fact from their employers due to fear of retaliation. I expect the most typical use case of this document will be programmers working as consultants, or who wish to contribute to Open Source projects in their free time. Potential Victims of Identity Theft (Everyone)
This document can also help those who are interested in protecting their identities and/or financial information from being stolen due to their commerce online and elsewhere. As mentioned above, data warehouses such as Choicepoint are essentially making identity a commodity. It is inevitable that this data will be leaked and stolen again and again. With identity becoming an increasingly integral aspect of functioning in society, black markets that sell this data will continue to be extremely profitable. Just like the War on Drugs, the War on Terror fought through the politics of domination and control will lead to ever escalating levels of waste, destruction, and chaos. The best way to protect yourself is to minimize your digital footprint: Use anonymous forms of payment online, and conceal your name and mailing address. Entrepreneurs
The last major category of people who are likely to find this document useful are those who are interested in providing privacy and anonymity services and software to others. Privacy and anonymity are difficult problems. There are many holes to be filled in, usability issues to be addressed, and markets to be built. To this group of people, every privacy problem and legal restriction should represent a potential market to get involved in. However, DO NOT SELL SNAKE OIL. If you cannot stand up to legal or other pressure, you need to inform your users of this fact clearly, so they are sure to take appropriate precautions while using your service (especially if you are located within the USA). Very few, if any, privacy services are capable of operating as stand-alone one-shot solutions. What is needed is a series of tools and components that can be combined arbitrarily. Focus on one component, and do it well. [Mark as patrolled]
- Email / Messaging
- See also: The compendium of clear net Email providers.
- Lelantos – Paid e-mail service.
BitMessage.ch – Bitmessage support build-in. Registration is done using their clearweb link.
TorBox – Tor-only secure and private email service. ** may work like shit **
Protonmail – Swiss based e-mail service, encrypts e-mails locally on your browser. Free and paid accounts.
Guerrilla Mail – Disposable Temporary E-Mail Address.
Bitmai.la – paid accounts only (low cost – $0.60 lifetime). 500mb Mailbox, Full imap, pop3 and smtp support.
AnonInbox – paid accounts only. 0.1 BTC / Year, 10GB disk space, IMAP, POP3, SMTP access, Web based access – RoundCube & SquirrelMail.
Mail2Tor – New Tor Mail Server to clear web. (Not working properly, delayed emails)
Sigaint – Darknet email service that allows you to send and receive email without revealing your location or identity. [Down 2017/2]
Onion Mail – SMTP/IMAP/POP3. ***@onionmail.in address. Registration is paid from 17\02.[10$]. [Down 2016/12]
MailTor – Free @mailtor.net account (webmail, smtp, pop3 and imap access). [Down 2016/5]
Anonymous random chatting Talk to random users anonymously. - Social Networks
- BlackBook – Social media site (The facebook of TOR)
Galaxy 2 – A revival of the old Galaxy community.
Facebook – The real Facebook’s Onion domain. Claim not to keep logs. Trust them at your peril.
Moneybook The darkweb Facebook of money. Now with anon posting.
Truth & Light Need help? We are here to help the best we can for anyone in need. - Forums / Boards / Chans
- The Stock Insiders – How to Beat Wall Street. The community for exchanging Insider Information about the Publicly Traded Companies.
Hidden Answers a site for asking questions and receiving answers on Tor.
The Intel Exchange – Know or need to know something? Ask and share at this underground intelligence gathering network. (New Board. Much Better) (2013-08-11 UTC Appears that admins have ditched?)
Flashlight forum An info beam in the darkweb.
Anonymous BBS, gopher interface, telnet interface – Another variation of the talks style of board.
InserTor Tor pastebin clone. Create new paste, share code, share news. Public and Private pastes. Create encrypted paste (encrypted button only with java on) or paste with time limit (also burn on reading!)
Simple Pastebin – Very simple Tor free Pastebin. - Political Advocacy
- CODE:GREEN – Ethical hacktivism for a better world
BuggedPlanet.Info – X
paraZite #1st, clearnet 301 redirector – Illicit activities advocacy and censored information archive.
paraZite #2nd, clearnet 301 redirector – Illicit activities advocacy and censored information archive.
FREEFOR – USA-based FREEdom FORces developing a turnkey distributed Temporary Autonomous Zone. FAQ - Whistleblowing
WikiLeaks - WikiLeaks
- Other
- Tor Against CP! – Free and clean Tor – Tor users against CP!
Indymedia Keyserver Secure PGP Keyserver in Onionland.
PedoraBox – List of Pedophiles IP Addresses.
Zyprexa Kills, mirror – The Zyprexa Memos. Internal documents that Eli Lilly tried to expose.
Cat out of the Bag [Tor | Internet] – Neven Lovrics’ disclosure.
Illuminati (TOR Link) – New World Order
Illuminati (WWW Link) – New World Order
Strategic Intelligence Network – The Strategic Intelligence Network goal is to provide intelligences, ressources and tools to be prepared and to respond to crisis situations anywhere you are in the world.
The Anarchism Library Mirror – Mirror content from September 2012.
Hack Canada – America is a joke.
Cat Facts – A site that distributes cat facts.
Safer Anonymous OS Guide – A Comprehensive Guide to Installing and employing a Safer Anonymous Operating System.
Global Leaks – Blow the whistle! (requires javascript)
SecureDrop (Clearnet) – An open-source whistleblower submission system that media organizations can use to securely accept documents from and communicate with anonymous sources. - H/P/A/W/V/C
- Hack, Phreak, Anarchy (internet), Warez, Virus, Crack.
- HackForum – hacking, malware, carding and more!
TCF – Tor Carding Forums + Market.
Spartan’s Dark Rift – Hacking, cracking, conspiracy and more plus a nightly deep web crawl and connection test for onion sites. Check out the downloads section for a growing collection of underground docs. (under H/P/A/W/V/C)
Milw0rm RaaS – Ransomware as a Service. - Audio – Music / Streams
- Deepweb Radio — RadioService operating over TOR
lol 20th Century Western Music Recordings and Scores – high quality music notations and lossless recording that people can get. these are distributed on oneswarm –
Lossless Audio Files – Mostly WavPack, some FLAC, Ape, ogg, etc. Has index generating links.
2f30.org Live Radio – The 2f30.org Live Radio Stream inside the Tor Network - Video – Movies / TV
- Torflix – Watch Tv series over Tor.
FileTor – A Well organized Anime, Movie and TV Show Index. - Books
- Example rendezvous points page – Thomas Paine’s Common Sense and The Federalist papers
Traum library mirror – 60GB of Russian and English books. A mirror of the latest Traum ISO. Covers, search and downloads in FB2, HTML and plain TXT
ParaZite – Collection of forbidden files and howto’s (pdf, txt, etc.).
Jotunbane’s Reading Club “All your ebooks are belong to us!”
Liberated Books and Papers A small collection of hard to find books.
Clockwise Library A collection of art and science books.
The Last of PAPYREFB2 A collection of mostly Spanish books.
Paul Dreyer’s eBook Library – DRM-Free Growing eBook Library, mostly in ePub format.
BB Compendium – A collection of chemistry, drugs, explosives, fireworks, pyrotechnics, science, and weapons related documents.
Libraries A more complete list. - Drugs
- DREAM MARKET is a SCAM!! REMEMBER THE NAME!! AND NEVER USE IT!
- Drug Market Anonymous marketplace for all kinds of drugs
Drugs4You – Drugs and Medicines from Germany – Weeds, XTCs, MDMA, Cocaine, Crystal Meth, Speed and a lots more. Medications – Ritalin, Diazepam, Tilidin, Rohypnol, Ketamine, Vicodin, Oxycodone, Tramadol, and a lot more. We ship from Germany.
ONION PHARMA – Pharmacy Marketplace. PSY, Stimulants, Opioids, Ecstasy and more…
Weed&Co – Weed / Cigarettes … Prix Bas / Low Price … weed cigarette.
CannabisUK – UK Wholesale Cannabis Supplier
Green Road – Biggest marketplace with full working escrow.
MOM4Europe Mail Order Marijuana – Order organic weed from Netherlands directly from the source.
Green Dragon UK – Cannabis tincture, prompt delivery, low prices
EuCanna – ‘First Class Cannabis Healthcare’ – Medical Grade Cannabis Buds, Rick Simpson Oil, Ointments and Creams
Peoples Drug Store – The Darkweb’s Best Online Drug Supplier.
Smokeables – Finest Organic Cannabis shipped from the USA
CannabisUK – UK Wholesale Cannabis Supplier
DeDope – German Weed and Hash shop. (Bitcoin)
EU Drugstore – Best EU Store Ever
BitPharma – EU vendor for cocaine, speed, mdma, psychedelics and subscriptions
Brainmagic – Best psychedelii
NLGrowers – Coffee Shop grade Cannabis from the netherlands
OnionShop – New anonymous and secure marketplace selling drugs, weapons…
Drugstore – Marketplace with a wide range of drugs! (escrow)
The Pot Shop – Weed and Pot Shop Trading for longer than a year now! (Bitcoin) -UPGRADED DOMAIN- .
EU Cocaine – selling Cocaine, Meth and Heroine. (Bitcoin)
Weed Store – well-known deepweb store selling high quality weed
Steroid King – All the steroids you need. (Bitcoin)
Dream Market Anonymous marketplace for all kinds of drugs.
Wacky Weed – Hi Quality Green at Wacky Prices - DREAM MARKET is a SCAM!! REMEMBER THE NAME!! AND NEVER USE IT!
ADULT - VideosME – Webcam videos 18+ only. Caution: Possible scam
Cute Sweet Teenies (+18) Come to one of the greatest chan sites. Nude And NN Teen Girls. Caution: Clearnet
Madama libreygratis cl 200000+ videos from sites like pornhub, redtube, xhamster, xvideos, etc… And new videos are added hourly! - Erotica
- Darkscandals Site with real Rape, Blackmail and Forced videos (Pack 7 is out since February 12, 2017 ).
- Noncommercial (E)
- X Nordic Scandinavian Amateurs Amateur pictures from Nordic woman (Sweden, Norway, Denmark, Iceland and Finland).
XCOMICS Adult comics.
Pink Meth archive One of the archives of the now defunct Pink Meth site, amateur pictures with names. - Commercial (E)
- bittit NSFW, clearnet – Buy or sell original NSFW pictures for Bitcoins.
- Animal Related
- Animal Porn Pics Hot Girls Loves Hers Pets
The Secret Story Archive #1st – Big cat zoophile stories, artwork, links and forum.
The Secret Story Archive #2nd – Mirror of #1st.
Zoo – Zoophilia-related imageboard - Other
- TelAvivService – Professional anonymous global goods partners.
VOR-COM Archive – Archive of the VOR-COM. Contains vore!
Madman File Storage Archives of illegal/miscellaneous (censored) files, such as guides for making methamphetamine, suicidal howto’s and more. Anonymous users can submit files. Also a tor link directory. [temporarily down/empty for renovation] - Uncategorized
- Services that defy categorization, or that have not yet been sorted.
- noreason – Info and pdf files on weapons, locks, survival, poisons, protesters, how to kill. Hidden Wiki, TorDir, Steal this wiki, Telecomix Crypto Munitions Bureau mirrors. Guro, dofantasy / Fansadox Collection. Nigger allstardrift on kik
Volatile Git – Git hosting provided by Gogs software. Open registration with HTTP/S, GIT, and SSH access over onion and clearnet. Unfortunately, requires JavaScript.
IIT Underground – Information on and photos of the steam tunnels and roofs at the Illinois Institute of Technology. - Non-English
Belarussian / Белорусский
Finnish / Suomi - Thorlauta – Thorlauta
Silkkitie – Silkkitie - French / Français
- Trollodrôme – Forum non modéré. [dead services]
French Hidden Wiki – Bienvenue sur le French Hidden Wiki v2!
French Deep Web – an administered and moderate French board (1er forum francophone)
Liberty’s Hackers – No CP, No racism – because Knowledge has value only if it is shared by all – hosting service
Liberty’s Hackers & French Deep Web Wiki – Liberty’s Hackers & French Deep Web Wiki – sharing everything
Le Tesseract – Centre de formation ésotérique. (Nouveau lien mai 2015)
La Main Noire – Market professionel et communautaire francais avec irc anonyme
Republique de Hackers – Forum francophone [dead service] - German / Deutsch
- Deutschland im Deep Web – German darknet community with forum and chat
Das ist DEUTSCHLAND hier! 2.0 Das ist DEUTSCHLAND hier! Nachfolger.
German pages – Neues Deutschland II. - Greek / ελληνικά
Italian / Italiano - Babylon – Babylon, forum per la comunità italiana
Cipolla – Comunita’ italiana
Italian Darknet Community – Italian Darknet Community - Japanese / 日本語
- Japan Hidden Wiki – Links to Japan onions.
OnionChannel – Onion Channel, a system similar to 2channel. - Korean / 한국어
- Korean Hidden Wiki – 한국어 히든 위키 페이지입니다. [internal link]
하이 코리아 – 하이 코리아는 비트코인을 이용한 대마초 거래 사이트입니다. HiGH KOREA is a marijuana trading site using Bitcoin.
대한민국 최전선(FRONT LINE : R.O.K ) – 오픈마켓, 한국형 커뮤니티. 무정부 아고라. (Korean Anarchic Agora) - Chinese / 中国語
- Tor中文资源 A Chinese blog on Tor Tor中文博客 2014年11月上线
Tor中文交流论坛 Tor中文交流论坛 2015年2月上线 - Polish / Polski
- Cebulka Najstarsze działające polskie forum w sieci Tor. Brak cenzury i moderacji.
ToRepublic Forum, market oraz serwer IRC.
Torepublic ND Forum, market.
Polish Board & Market Forum oraz market (archiwum dostępne tylko do odczytu).
Technodrome Ukryta baza Kranga w sieci Tor! – Blog, katalog stron, WindowsOE, Forum, Shoutbox, Galeria, Aktualności. Kosmiczny przyjaciel ToRepublic.
InserTor Pastebin
Teczkohen – powrót obrazkowego forum o tematyce stalking
Polska Ukryta Wiki – polski odpowiednik THW - Russian / Русский
- MALINA – RU Торговая площадка и форум.
Продажа клонированных карт – Русскоязычный сайт по продаже клонированных карт
Financial Hack Group – Продажа клонированных карт (русс.)
Зеркало библиотеки Траума – 60GB русских и английских книг. Обложки, поиск и возможность скачивать в форматах FB2, HTML и TXT
Флибуста – Библиотека.
Веб Хостинг в сети TOR – Apache, PHP5, MySQL, SFTP Access, xxxxxxxxxxxxxxxx.onion Domain, Bitcoin server
Russian Road – Торговая площадка для русскоязычных пользователей
РосПравосудие – крупнейшая картотека юристов, адвокатов, судей и судебных решений (50+ миллионов документов, 35+ тысяч судей, 65+ тысяч адвокатов, сотни тысяч юристов, прокуроры). «РосПравосудие» – аполитичный и независимый проект.
Покупка и продажа биткоинов Анонимная и безопасная покупка и продажа биткоинов.
China Market – китайский маркет. Всегда свежие поставки из Китая: каннабиноиды, MDMA кристаллы, экстази, LSD. Доставка без пересечения границы, есть представители в России, Украине и Казахстане. Автоматическое оформление, оплата и получение заказа. Методы оплаты: Bitcoin, Qiwi, Приват24, наличкой через терминалы.
Опасные связи – социальная сеть на русском языке, объединяющая людей неформальных интересов, которые считаются незаконными или аморальными в обществе.
A-chan Pусский глубокий веб-чан.
Скрытые Ответы Russian Hidden Answers.
Схоронил! Архив magnet-ссылок. - Spanish / Español
- CebollaChan – CebollaChan, el tor-chan en Castellano.
MaximaCulpa, Confesa tus pecados / confess your sins
TorPez – Foro de seguridad informatica entre otras cosas.
Hidden Answers es – Hidden Answers for Spanish-speakers. - Swedish / Svenska
- KognitionsKyrkan, clearnet – Spiritual stuff.
Moral.Nu, clearnet – Vad r moral? - Portuguese / Português
- Hidden Answers pt – Hidden Answers for Portuguese-speakers.
- Hidden Services – Other Protocols
- Volunteers last verified that all services in this section were up, or marked as DOWN, on: 2011-06-08 For configuration and service/uptime testing, all services in this section MUST list the active port in their address. Exception: HTTP on 80, HTTPS on 443. For help with configuration, see the TorifyHOWTO and End-to-end connectivity issues.
P2P FileSharing - Running P2P protocols within Tor requires OnionCat. Therefore, see the OnionCat section for those P2P services. IMPORTANT: It is possible to use Tor for P2P. However, if you do, the right thing must also be done by giving back the bandwidth used. Otherwise, if this is not done, Tor will be crushed taking everyone along with it.
- Sea Kitten Palace – Torrent site and tracker for extreme content (real gore, animal torture, shockumentaries/mondo cinema, and Disney movies)
The Pirate Bay – The Pirate Bay. - Chat centric services
- Some people and their usual server hangouts may be found in the Contact Directory.
IRC - Use e.g. ChatZilla add-on for the IRC protocol (the Tor Project does not suggest installing browser addons unless you understand the risks), or a standalone client such as HexChat. Tails comes with Pidgin, which will work for IRC as well.
- Agora Anonymous – Agorist IRC server
- plaintext ports: 6667
- ANYChat
- plaintext ports: 6667; ssl: 6697
- DeepIRC
- plaintext ports: 6667
- Federation: OnionNet – IRC network comprised of:
onionirczesfffux.onion:6667 Juppi IRC – Juppi’s IRC server.
onionirccaaakegi.onion:6667 Juppi IRC (old – Down) – Juppi’s other IRC server.
onionirc2udqrqpo.onion:6667 YankeeGuy IRC – YankeeGuy’s IRC server.
FreedomIRC – gopher or http
irc.freedom.net (alt link)
plaintext ports: 6667
FREEFOR – FREEdom FORces – see Political Advocacy
hackint – hackint is a communication network for the hacker community. - running on lechuck.hackint.org; ssl ports: 9999; no plaintext ports
- HeavyCrypto – HeavyCrypto IRC
- ssl ports: 6697; no plaintext ports
- KeratNet – Kerat
- plaintext ports: 6667; ssl: 6697
- KillYourIRC – onion for irc.killyourtv.i2p
- plaintext ports: 6667; ssl: 9999
- Nazgul – free for all IRC network
- plaintext ports: nazgul3zxuzvrgg6.onion:6667
ssl ports: irc.nazgul.io:6697 Clearnet (SSL) - OnionIRC – New, censorship-free IRC server.
- plaintext ports: 6668
- OpenSource, info – Drug chat
public.ronsor-router.lan – Freelinking server owned by Ronsor - plaintext ports: 6667; SSL ports: 6697
- Smokey’s Grill – General chat IRC. Doesn’t allow plotting the abuse of other people.
- plaintext ports: 6667
- Volatile – we back
irc.krustykrab.restaurant – owned by wowaname
plaintext ports: 6667, 7777; ssl: 6697, 9999.
kitsune6uv4dtdve.onion – owned by wowaname
plaintext ports: 6667, 7777; ssl: 6697, 9999. - Anonimowy IRC – Anonimowy IRC (Polish anonymous IRC server) – Down
- plaintext ports: 6667; ssl:6697
- hackint – Old hidden service? – Down
irc2p onion gateways:
irc.echelon.i2p – Gateway provided by chisquare / psi of All You’re Base – Down
irc.postman.i2p – Down
NeoturbineNET IRC – NeoturbineNET IRC server – Down - running on kropotkin.computersforpeace.net; ssl ports: 6697; no plaintext ports
- OFTC IRC – OFTC – unofficial hidden service for OFTC – Down
- running on: (various).oftc.net, ports:: plaintext: 6667 ssl: 6697
- prooops.eu IRC – prooops.eu IRC (Clearnet http://irc.prooops.eu/) – Down
- plaintext ports: 6667; ssl: 6697
- WANNABE: Federation OnionNet :
New Ngircd – Yep this is a new ircd in OnionLands looking for peering in OnionNet – Down
freenode IRC – requires SASL authentication to an already existing NickServ account – Down
2hktdmgt6bg2hjuc.onion
frxleqtzgvwkv7oz.onion
l4wvhvf666nifnpg.onion
p4fsi4ockecnea7l.onion
p567hbjdstqvg7xw.onion
vgh6tbfjk65zj5ep.onion - All of these direct to zelazny.freenode.net and allow plaintext port 6667 as well as SSL ports 6697, 7000, and 7070.
- Below is a list of DEAD irc servers from Anonet:
- AnoNet – Each server is on its own network and connects to a chat cloud
irc1.srn.ano, clearnet
elef7kcrczguvamt.onion:15783 – Direct access to the AnoNet chat cloud. Use an IRC server to connect.
irc3.srn.ano
irc2.srn.ano, clearnet – Still connects to the old AnoNet chat cloud; that will soon change.
irc4.srn.ano
irc.cananon.ano Web Chat Version join #Anonet - SILC
- fxb4654tpptq255w.onion:706 – SILCroad, public server. [discuss/support]
Silkroad 2.0 – The new silkroad. Biggest marketplace for drugs on the Darknet. (Bitcoin)
kissonmbczqxgebw.onion:10000 – KISS.onion – Keep It Simple and Safe – ditch the web browser, use SILC to communicate securely (using Pidgin with OTR) - XMPP (formerly Jabber)
- xmpp:tortureregex47xf.onion:5222 – Public XMPP with MUC (multi user chat) enabled. No Child Porn and racism here, any breach will result in a ban. Maintained by Creative Hack
xmpp:okj7xc6j2szr2y75.onion:5222 – xmpp:jabber.ccc.de:5222 as a hidden service
xmpp:libertygb2nyeyay.onion:5222 – instant messager for Liberty’s Hackers – chat room for Liberty’s Hackers and french users – chat room for international sharing – Create your own public or private MUC – federation onion activated – No CP and no Racism please – web clients : https://libertygb2nyeyay.onion:5281/candy http://libertyy56ecbupa.onion/im/jappix/
xmpp:cyjabr4pfzupo7pg.onion:5222 – CYRUSERV Community Jabber, a public server ran by CYRUSERV. - TorChat Addresses
- Humans are listed in the above contact directory. Bots are listed below.
- 7oj5u53estwg2pvu.onion:11009 – TorChat InfoServ #2nd, by ACS.
gfxvz7ff3bzrtmu4.onion:11009 – TorChat InfoServ #1st, by ACS. - SFTP – SSH File Transfer Protocol
- These SFTP clients work with Tor: WinScp, FileZilla. Set proxy to SOCKS5, host 127.0.0.1, port 9150 (Windows,Mac) or 9050 (Linux). Encrypt your sensitive files using GnuPG before uploading them to any server.
- kissonmbczqxgebw.onion:10001 – KISS.onion – SFTP file exchange service (username “sftp.anon”, password “anon”)
- OnionCat Addresses
- List of only the Tor-backed fd87:d87e:eb43::/48 address space, sorted by onion. There are instructions for using OnionCat, Gnutella, BitTorrent Client, and BitTorrent Tracker.
- 62bwjldt7fq2zgqa.onion:8060
fd87:d87e:eb43:f683:64ac:73f9:61ac:9a00 – ICMPv6 Echo Reply
a5ccbdkubbr2jlcp.onion:8060 – mail.onion.aio
fd87:d87e:eb43:0744:208d:5408:63a4:ac4f – ICMPv6 Echo Reply
ce2irrcozpei33e6.onion:8060 – bank-killah
fd87:d87e:eb43:1134:88c4:4ecb:c88d:ec9e – ICMPv6 Echo Reply
[fd87:d87e:eb43:1134:88c4:4ecb:c88d:ec9e]:8333 – Bitcoin Seed Node
taswebqlseworuhc.onion:8060 – TasWeb – DOWN 2011-09-08
fd87:d87e:eb43:9825:6206:0b91:2ce8:d0e2 – ICMPv6 Echo Reply
http://%5Bfd87:d87e:eb43:9825:6206:0b91:2ce8:d0e2%5D/
gopher://[fd87:d87e:eb43:9825:6206:0b91:2ce8:d0e2]:70/
vso3r6cmjoomhhgg.onion:8060 – echelon
fd87:d87e:eb43:ac9d:b8f8:4c4b:9cc3:9cc6 – ICMPv6 Echo Reply - Bitcoin Seeding
- Instructions
- xqzfakpeuvrobvpj.onion:8333
z6ouhybzcv4zg7q3.onion:8333 - Dead Hidden Services
- Do not simply remove services that appear to be offline from the above list! Services can go down temporarily, so we keep track of when they do and maintain a list of dead hidden services.
- In addition to an onion simply being gone (Tor cannot resolve the onion), sites that display 404 (and use a known onion/URL based hosting service) are the only other thing that is considered truly DOWN. Presumably the account is gone.
- If a service has been down for a while, tag it with ‘ – DOWN YYYY-MM-DD’ (your guess as to when it went down).
If a tagged service on the above list of live hidden services has come back up, remove the DOWN tag.
If a tagged service is still down after a month, please move it (along with the DOWN tag) to the list of dead hidden services. - The general idea of the remaining four service states below is that, if the Hidden Service Descriptor is available, and something is responding behind it… the service is considered up, and we track that fact on the Main Page. If any of these subsequently go offline, append the DOWN tag and handle as above.
- Hello world’s / statements, minimal sites, services with low user activity, etc (while boring)… are listed as usual.
Broken services are those that display 404 (and do not use a known hosting service), PHP or other errors (or they fail silently)… any of which prevent the use of the service as intended. They also include blank pages, empty dirs and neglected status notes. Presumably the operator is in limbo. Broken services are tagged with ‘ (reason) – Broken YYYY-MM-DD’ (your guess as to when it went broken)
Services that automatically redirect to another service (such as by HTTP protocol or script), have their redirection destinations noted in their descriptions. These are tagged with ‘ – Redir YYYY-MM-DD’ (your guess as to when it went redir)
Sites that are formally closed via announcement are tagged with ‘ – Closed YYYY-MM-DD’ (your guess as to when it went closed. - Is Online that HiddenService? This service is very useful in determining whether onions are up or not. It also gives a reason why they are down.
- Sites on this list that have no chance of coming back (LE takedowns, dead for some time) should be archived to page dead services just in case they should ever be needed.
- CYRUSERV – Hosting service with an emphasis on security, with many features. (clearnet) [Discontinued 2016]]
Torlinks Directory for .onion sites, moderated. [Down 2016/1]
Image Hosting – Free images hosting site, anything goes. [Down 2015/11]
Free imageboard – apply here for free board on this forum, with basic janitor priveleges. [Down 2015/11]
Teddit – A Reddit clone. [Shutdown by owner 2016]
irc.dg.i2p.onion – dg’s onion server for i2p – Down
Dark Tunnel irc2p gateway – Gateway to the irc2p IRC network on I2P.
Onionweb filehosting – Filehosting service. 100MB upload limit, no illegal files allowed - Navigation menu
- Main page Discussion View source History
- Create account Log in
- Navigation
- Main page
Recent changes
Random page
Rules of the site - SearchTools
- What links here
Related changes
Special pages
Printable version
Permanent link
Page information - Powered by MediaWiki
- This page was last modified on 23 February 2017, at 14:06. This page has been accessed 63,502,545 times. Privacy policy About The Hidden Wiki Disclaimers













 Bitcoin
Bitcoin
 Bitcoin
Bitcoin
 Electrum
Electrum
 mSIGNA
mSIGNA
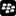
 Bitcoin
Bitcoin

 breadwallet
breadwallet
 Bither
Bither
 GreenBits
GreenBits
 Mycelium
Mycelium
 BitGo
BitGo
 Green
Green
 Coinomi
Coinomi



























You must be logged in to post a comment.